Exam Details
Exam Code
:210-255Exam Name
:Cisco Cybersecurity OperationsCertification
:Cisco CertificationsVendor
:CiscoTotal Questions
:224 Q&AsLast Updated
:Nov 03, 2022
Cisco Cisco Certifications 210-255 Questions & Answers
-
Question 161:
Refer to the exhibit. You notice that the email volume history has been abnormally high. Which potential result is true?
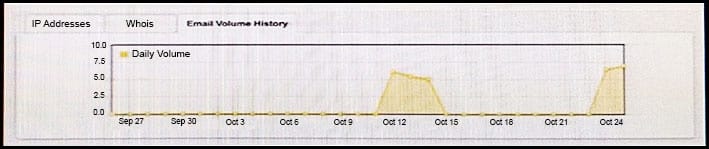
A. Email sent from your domain might be filtered by the recipient.
B. Messages sent to your domain may be queued up until traffic dies down.
C. Several hosts in your network may be compromised.
D. Packets may be dropped due to network congestion.
-
Question 162:
Which element can be used by a threat actor to discover a possible opening into a target network and can also be used by an analyst to determine the protocol of the malicious traffic?
A. TTLs
B. ports
C. SMTP replies
D. IP addresses
-
Question 163:
Refer to the exhibit. Which type of log is this an example of?

A. syslog
B. NetFlow log
C. proxy log
D. IDS log
-
Question 164:
Refer to the exhibit. Which type of log is this an example of?
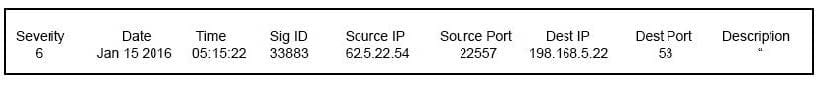
A. IDS log
B. proxy log
C. NetFlow log
D. syslog
-
Question 165:
Which option allows a file to be extracted from a TCP stream within Wireshark?
A. File > Export Objects
B. Analyze > Extract
C. Tools > Export > TCP
D. View > Extract
-
Question 166:
During which phase of the forensic process are tools and techniques used to extract the relevant information from the collective data?
A. examination
B. reporting
C. collection
D. investigation
-
Question 167:
Which element is included in an incident response plan?
A. organization mission
B. junior analyst approval
C. day-to-day firefighting
D. siloed approach to communications
-
Question 168:
In Microsoft Windows, as files are deleted the space they were allocated eventually is considered available for use by other files. This creates alternating used and unused areas of various sizes. What is this called?
A. network file storing
B. free space fragmentation
C. alternate data streaming
D. defragmentation
-
Question 169:
Which process is being utilized when IPS events are removed to improve data integrity?
A. data normalization
B. data availability
C. data protection
D. data signature
-
Question 170:
Which goal of data normalization is true?
A. Reduce data redundancy.
B. Increase data redundancy.
C. Reduce data availability.
D. Increase data availability
Related Exams:
300-915
Developing Solutions using Cisco IoT and Edge Platforms (DEVIOT)300-920
Developing Applications for Cisco Webex and Webex Devices (DEVWBX)352-011
Cisco Certified Design Expert Practical500-052
Cisco Unified Contact Center Express500-173
Designing the FlexPod Solution (FPDESIGN)500-174
Implementing and Administering the FlexPod Solution (FPIMPADM)500-201
Deploying Cisco Service Provider Mobile Backhaul Solutions500-210
SP Optical Technology Field Engineer Representative500-220
Cisco Meraki Solutions Specialist500-230
Cisco Service Provider Routing Field Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 210-255 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.