Exam Details
Exam Code
:200-201Exam Name
:Understanding Cisco Cybersecurity Operations Fundamentals (CBROPS)Certification
:CyberOps AssociateVendor
:CiscoTotal Questions
:406 Q&AsLast Updated
:May 02, 2025
Cisco CyberOps Associate 200-201 Questions & Answers
-
Question 301:
Refer to the exhibit.

What is the potential threat identified in this Stealthwatch dashboard?
A. Host 10.201.3.149 is sending data to 152.46.6.91 using TCP/443.
B. Host 152.46.6.91 is being identified as a watchlist country for data transfer.
C. Traffic to 152.46.6.149 is being denied by an Advanced Network Control policy.
D. Host 10.201.3.149 is receiving almost 19 times more data than is being sent to host 152.46.6.91.
-
Question 302:
What is the function of a command and control server?
A. It enumerates open ports on a network device
B. It drops secondary payload into malware
C. It is used to regain control of the network after a compromise
D. It sends instruction to a compromised system
-
Question 303:
At which layer is deep packet inspection investigated on a firewall?
A. internet
B. transport
C. application
D. data link
-
Question 304:
Refer to the exhibit.

An engineer is analyzing this Cuckoo Sandbox report for a PDF file that has been downloaded from an email. What is the state of this file?
A. The file has an embedded executable and was matched by PEiD threat signatures for further analysis.
B. The file has an embedded non-Windows executable but no suspicious features are identified.
C. The file has an embedded Windows 32 executable and the Yara field lists suspicious features for further analysis.
D. The file was matched by PEiD threat signatures but no suspicious features are identified since the signature list is up to date.
-
Question 305:
Refer to the exhibit.
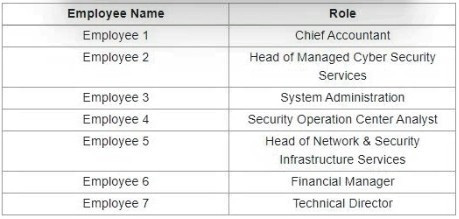
Which stakeholders must be involved when a company workstation is compromised?
A. Employee 1 Employee 2, Employee 3, Employee 4, Employee 5, Employee 7
B. Employee 1, Employee 2, Employee 4, Employee 5
C. Employee 4, Employee 6, Employee 7
D. Employee 2, Employee 3, Employee 4, Employee 5
-
Question 306:
Refer to the exhibit.
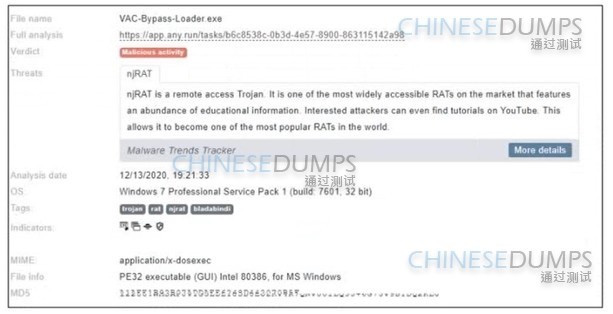
Where is the executable file?
A. info
B. tags
C. MIME
D. name
-
Question 307:
Which process is used when IPS events are removed to improve data integrity?
A. data availability
B. data normalization
C. data signature
D. data protection
-
Question 308:
What is the difference between an attack vector and attack surface?
A. An attack surface identifies vulnerabilities that require user input or validation; and an attack vector identifies vulnerabilities that are independent of user actions.
B. An attack vector identifies components that can be exploited, and an attack surface identifies the potential path an attack can take to penetrate the network.
C. An attack surface recognizes which network parts are vulnerable to an attack; and an attack vector identifies which attacks are possible with these vulnerabilities.
D. An attack vector identifies the potential outcomes of an attack; and an attack surface launches an attack using several methods against the identified vulnerabilities.
-
Question 309:
What is a difference between tampered and untampered disk images?
A. Tampered images have the same stored and computed hash.
B. Untampered images are deliberately altered to preserve as evidence.
C. Tampered images are used as evidence.
D. Untampered images are used for forensic investigations.
-
Question 310:
An analyst received an alert on their desktop computer showing that an attack was successful on the host. After investigating, the analyst discovered that no mitigation action occurred during the attack. What is the reason for this discrepancy?
A. The computer has a HIPS installed on it.
B. The computer has a NIPS installed on it.
C. The computer has a HIDS installed on it.
D. The computer has a NIDS installed on it.
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 200-201 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.