100-160 Exam Details
-
Exam Code
:100-160 -
Exam Name
:Cisco Certified Support Technician (CCST) Cybersecurity -
Certification
:CCST -
Vendor
:Cisco -
Total Questions
:63 Q&As -
Last Updated
:Jan 10, 2026
Cisco 100-160 Online Questions & Answers
-
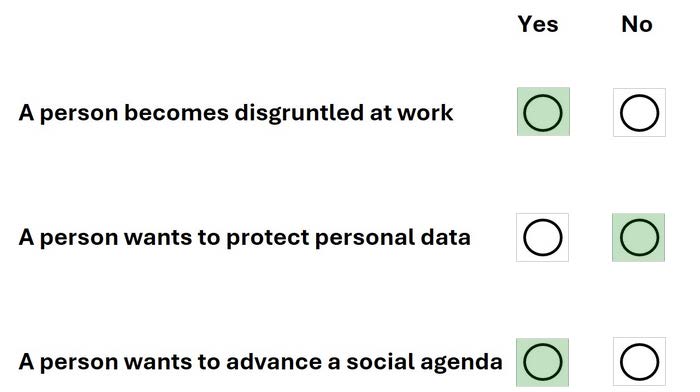
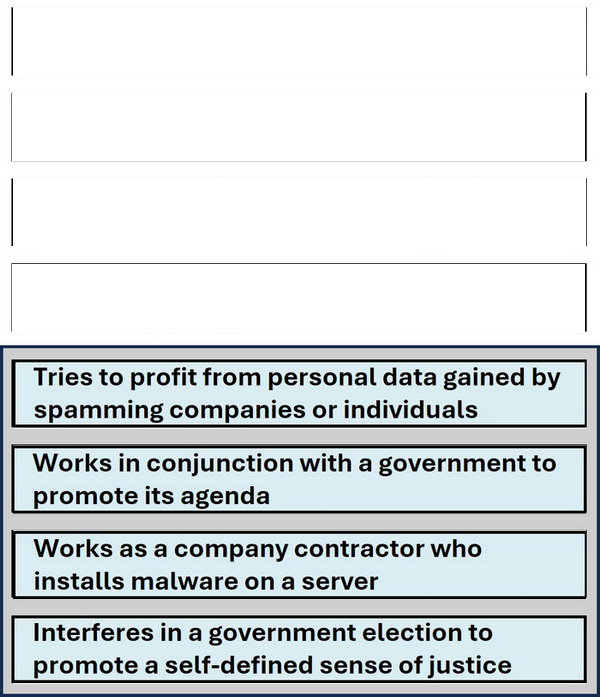
Question 1:
HOT SPOT
For each statement, select True if it is a common motivation to commit cyber attacks or False if it is not.
Note: You will receive partial credit for each correct selection.
-
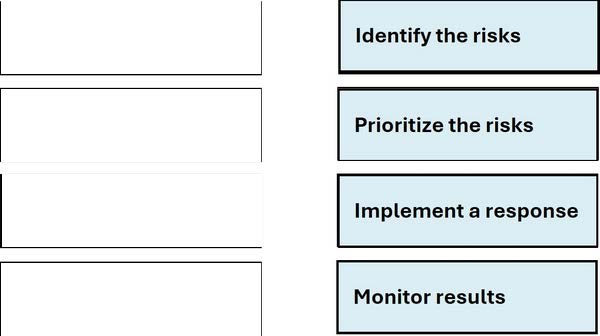
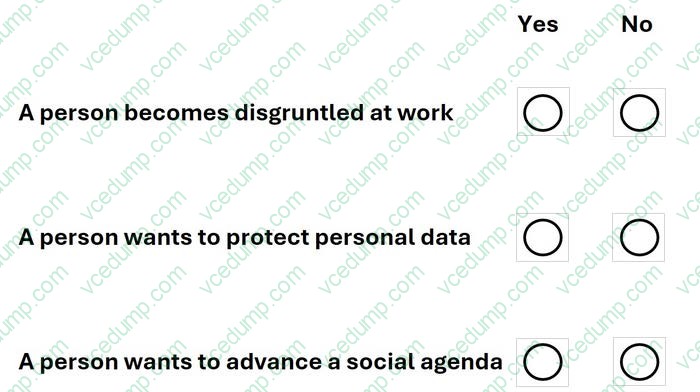
Question 2:
DRAG DROP
You need to manage security risks at your company. In which order should you complete the actions?
Move all the actions to the answer area and place them in the correct order.
Select and Place:
-
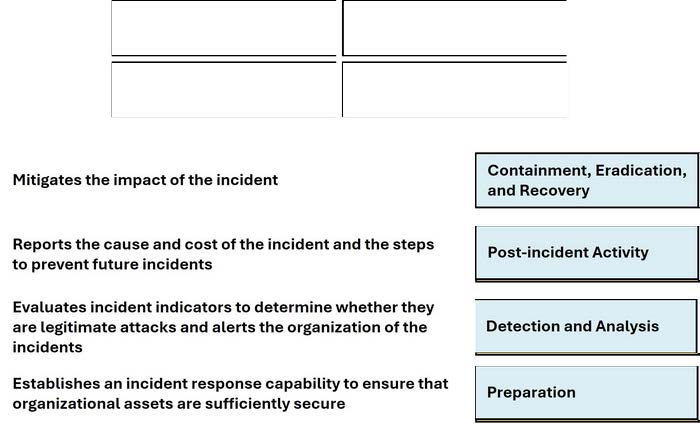
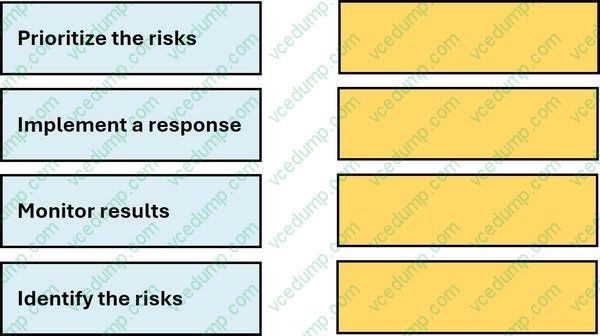
Question 3:
DRAG DROP
Move each NIST Incident Response Lifecycle phase from the list on the left to the correct description on the right.
Note: You will receive partial credit for each correct answer.
Select and Place:
-
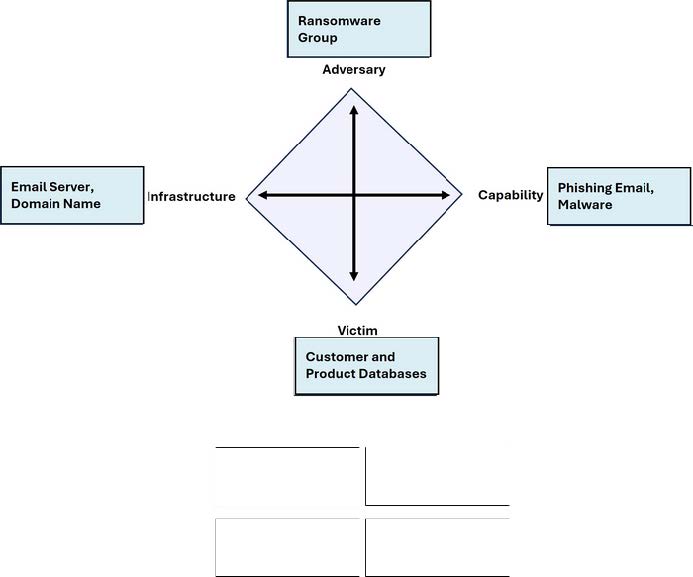
Question 4:
DRAG DROP
You need to diagram an intrusion event by using the Diamond Model.
Move each event detail from the list on the left to the correct location in the diagram on the right.
Note: You will receive partial credit for each correct response.
Select and Place:
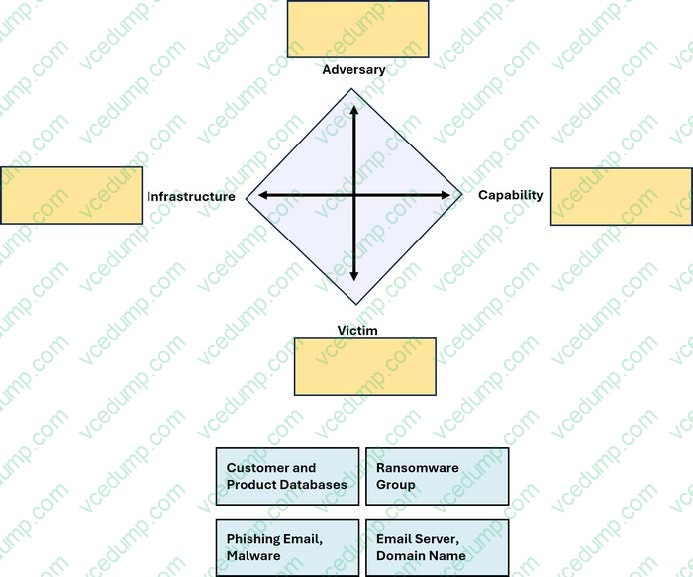
-
Question 5:
DRAG DROP
Move each scenario from the list on the left to the correct type of attacker on the right.
Note: You will receive partial credit for each correct answer.
Select and Place:
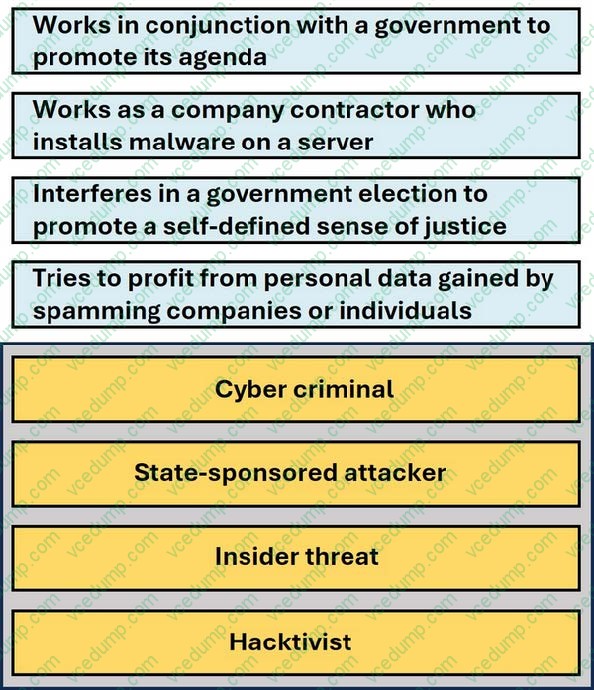
-
Question 6:
Which encryption type is commonly used to secure WiFi networks?
A. Data Encryption Standard (DES)
B. Triple Data Encryption Algorithm (Triple DES)
C. Advanced Encryption Algorithm (AES)
D. RSA (Rivest-Shamir-Adleman) -
Question 7:
Which two basic metrics should be taken into consideration when assigning a severity to a vulnerability during an assessment?(Choose 2.)
A. The likelihood that an adversary can and will exploit the vulnerability
B. The impacts that an exploit of the vulnerability will have on the organization
C. The time involved in choosing replacement software to replace older systems
D. The age of the hardware running the software that contains the vulnerability -
Question 8:
A SOC analyst notices repeated failed login attempts from a foreign IP address followed by a successful login to a privileged account. What is the most appropriate next step?
A. Reset the affected user's password and investigate the scope of compromise.
B. Block all foreign IP addresses from accessing the network.
C. Run a full vulnerability scan of the corporate network.
D. Ignore the event unless it happens again. -
Question 9:
How do threat actors launch ransomware attacks on organizations?
A. They implant malware to collect data from the corporation's financial system.
B. They deface an organization's public-facing website.
C. They lock data and deny access to the data until they receive money.
D. They secretly spy on employees and collect employees' personal information. -
Question 10:
You work for a hospital that stores electronic protected health information (ePHI) in an online portal. Authorized employees can use their mobile devices to access patient ePHI.
You need to ensure that employees' mobile devices comply with HIPAA regulations.
Which safeguard should you develop and implement?
A. An ownership policy for employees' mobile devices
B. A contingency plan
C. A policy that requires multi-factor authentication to use the mobile device
D. A policy to govern how ePHI is removed from mobile devices
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Cisco exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your 100-160 exam preparations and Cisco certification application, do not hesitate to visit our Vcedump.com to find your solutions here.