Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Aug 15, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 911:
A major political party experienced a server breach. The hacker then publicly posted stolen internal communications concerning campaign strategies to give the opposition party an advantage. Which of the following BEST describes these threat actors?
A. Semi-authorized hackers
B. State actors
C. Script kiddies
D. Advanced persistent threats
-
Question 912:
A bank detects fraudulent activity on user's account. The user confirms transactions completed yesterday on the bank's website at https://www.company.com. A security analyst then examines the user's Internet usage logs and observes the following output:
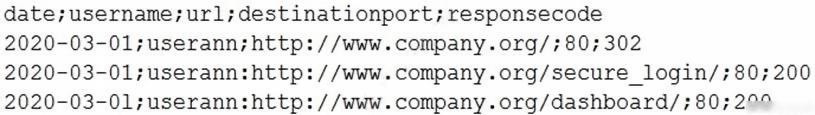
Which of the following has MOST likely occurred?
A. Replay attack
B. SQL injection
C. SSL stripping
D. Race conditions
-
Question 913:
An enterprise needs to keep cryptographic keys in a safe manner. Which of the following network appliances can achieve this goal?
A. HSM
B. CASB
C. TPM
D. DLP
-
Question 914:
An analyst has determined that a server was not patched and an external actor exfiltrated data on port 139. Which of the following sources should the analyst review to BEST ascertain how the incident could have been prevented?
A. The vulnerability scan output
B. The security logs
C. The baseline report
D. The correlation of events
-
Question 915:
A external forensics investigator has been hired to investigate a data breach at a large enterprise with numerous assets. It is known that the breach started in the DMZ and moved to the sensitive information, generating multiple logs as the attacker traversed through the network. Which of the following will BEST assist with this investigation?
A. Perform a vulnerability scan to identify the weak spots.
B. Use a packet analyzer to investigate the NetFlow traffic
C. Check the SIEM to review the correlated logs.
D. Require access to the routers to view current sessions,
-
Question 916:
When implementing automation with loT devices, which of the following should be considered FIRST to keep the network secure?
A. Z-Wave compatibility
B. Network range
C. Zigbee configuration
D. Communication protocols
-
Question 917:
A systems administrator needs to install the same X.509 certificate on multiple servers. Which of the following should the administrator use?
A. Key escrow
B. A self-signed certificate
C. Certificate chaining
D. An extended validation certificate
-
Question 918:
A security analyst has been reading about a newly discovered cyberattack from a known threat actor. Which of the following would BEST support the analyst's review of the tactics, techniques, and protocols the threat actor was observed using in previous campaigns?
A. Security research publications
B. The MITRE ATTandCK framework
C. The Diamond Model of Intrusion Analysis
D. The Cyber Kill Chain
-
Question 919:
Which of the following will MOST likely cause machine-learning and AI-enabled systems to operate with unintended consequences?
A. Stored procedures
B. Buffer overflows
C. Data bias
D. Code reuse
-
Question 920:
An organization that has a large number of mobile devices is exploring enhanced security controls to manage unauthorized access if a device is lost or stolen. Specifically, if mobile devices are more than 3mi(4.8km) from the building, the
management team would like to have the security team alerted and server resources restricted on those devices.
Which of the following controls should the organization implement?
A. Geofencing
B. Lockout
C. Near-field communication
D. GPS tagging
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.