Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Aug 15, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 931:
A company was recently breached, Part of the company's new cybersecurity strategy is to centralize the logs from all security devices. Which of the following components forwards the logs to a central source?
A. Log enrichment
B. Log aggregation
C. Log parser
D. Log collector
-
Question 932:
A security engineering installing A WAF to protect the company's website from malicious web requests over SSL. Which of the following is needed to meet the objective?
A. A reverse proxy
B. A decryption certificate
C. A split-tunnel VPN
D. Load-balanced servers
-
Question 933:
An incident, which is affecting dozens of systems, involves malware that reaches out to an Internet service for rules and updates. The IP addresses for the Internet host appear to be different in each case. The organization would like to determine a common IoC to support response and recovery actions. Which of the following sources of information would BEST support this solution?
A. Web log files
B. Browser cache
C. DNS query logs
D. Antivirus
-
Question 934:
A Chief Security Officer (CSO) is concerned about the volume and integrity of sensitive information that is exchanged between the organization and a third party through email. The CSO is particularly concerned about an unauthorized party who is intercepting information that is in transit between the two organizations.
Which of the following would address the CSO's concerns?
A. SPF
B. DMARC
C. SSL
D. DKIM
E. TLS
-
Question 935:
A company has discovered unauthorized devices are using its WiFi network, and it wants to harden the access point to improve security. Which of the following configurations should an analyst enable to improve security? (Choose two.)
A. RADIUS
B. PEAP
C. WPS
D. WEP-TKIP
E. SSL
F. WPA2-PSK
-
Question 936:
Joe, a security analyst, recently performed a network discovery to fully understand his organization's electronic footprint from a "public" perspective. Joe ran a set of commands and received the following output:
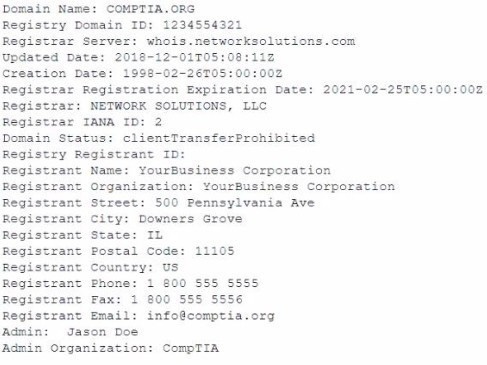
Which of the following can be determined about the organization's public presence and security posture? (Select TWO).
A. Joe used Whois to produce this output.
B. Joe used cURL to produce this output.
C. Joe used Wireshark to produce this output.
D. The organization has adequate information available in public registration.
E. The organization has too much information available in public registration.
F. The organization has too little information available in public registration.
-
Question 937:
An organization's finance department is implementing a policy to protect against collusion. Which of the following control types and corresponding procedures should the organization implement to fulfill this policy's requirement? (Select TWO).
A. Corrective
B. Deterrent
C. Preventive
D. Mandatory vacations
E. Job rotation
F. Separation of duties
-
Question 938:
A network administrator is concerned about users being exposed to malicious content when accessing company cloud applications. The administrator wants to be able to block access to sites based on the AUP. The users must also be protected because many of them work from home or at remote locations, providing on- site customer support. Which of the following should the administrator employ to meet these criteria?
A. Implement NAC.
B. Implement an SWG.
C. Implement a URL filter.
D. Implement an MDM.
-
Question 939:
Which of the following terms should be included in a contract to help a company monitor the ongoing security maturity of a new vendor?
A. A right-to-audit clause allowing for annual security audits
B. Requirements for event logs to be kept for a minimum of 30 days
C. Integration of threat intelligence in the company's AV
D. A data-breach clause requiring disclosure of significant data loss
-
Question 940:
Which of tre following would BEST identity and remediate a catatoss event in an enterprise using third-pany, web-based services and file-sharing platanmns?
A. SIEM
B. CASE
C. UTM
D. EDR
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.