Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jun 02, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 851:
A network administrator has been asked to install an IDS to improve the security posture of an organization.
Which of the following control types is an IDS?
A. Corrective
B. Physical
C. Detective
D. Administrative
-
Question 852:
A company is setting up a web server on the Internet that will utilize both encrypted and unencrypted web-browsing protocols. A security engineer runs a port scan against the server from the Internet and sees the following output:
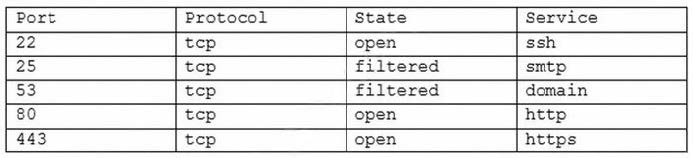
Which of the following steps would be best for the security engineer to take NEXT?
A. Allow DNS access from the internet.
B. Block SMTP access from the Internet
C. Block HTTPS access from the Internet
D. Block SSH access from the Internet.
-
Question 853:
When used at the design stage, which of the following improves the efficiency, accuracy, and speed of a database?
A. Tokenization
B. Data masking
C. Normalization
D. Obfuscation
-
Question 854:
A security analyst Is investigating a malware incident at a company. The malware is accessing a command-and-control website at www.comptia.com. All outbound Internet traffic is logged to a syslog server and stored in / logfiles/messages. Which of the following commands would be BEST for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?
A. head -500 www.comptia.com | grep /logfiles/messages
B. cat /logfiles/messages | tail -500 wew.comptia.com
C. tail -500 /legfiles/messages | grep www.comptia.com
D. grep -500 /logfiles/messages | cat www.comptia.com
-
Question 855:
A security manager for a retailer needs to reduce the scope of a project to comply with PCI DSS. The PCI data is located in different offices than where credit cards are accepted. All the offices are connected via MPLS back to the primary datacenter.
Which of the following should the security manager implement to achieve the objective?
A. Segmentation
B. Containment
C. Geofencing
D. Isolation
-
Question 856:
A startup company is using multiple SaaS and IaaS platform to stand up a corporate infrastructure and build out a customer-facing web application. Which of the following solutions would be BEST to provide security, manageability, and visibility into the platforms?
A. SIEM
B. DLP
C. CASB
D. SWG
-
Question 857:
An organization is tuning SIEM rules based off of threat intelligence reports. Which of the following phases of the incident response process does this scenario represent?
A. Lessons learned
B. Eradication
C. Recovery
D. Preparation
-
Question 858:
Which of the following is a difference between a DRP and a BCP?
A. A BCP keeps operations running during a disaster while a DRP does not.
B. A BCP prepares for any operational interruption while a DRP prepares for natural disasters.
C. BCP is a technical response to disasters while a DRP is operational.
D. A BCP is formally written and approved while a DRP is not.
-
Question 859:
A security analyst is reviewing information regarding recent vulnerabilities. Which of the following will the analyst MOST likely consult to validate which platforms have been affected?
A. SINT
B. SIEM
C. CVSS
D. CVE
-
Question 860:
The Chief Financial Officer (CFO) of an insurance company received an email from Ann, the company's Chief Executive Officer (CEO), requesting a transfer of $10,000 to an account. The email states Ann is on vacation and has lost her purse, containing cash and credit cards. Which of the following social-engineering techniques is the attacker using?
A. Phishing
B. Whaling
C. Type squatting
D. Pharming
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.