Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 571:
A security analyst is investigating an incident to determine what an attacker was able to do on a compromised laptop. The analyst reviews the following SIEM log:
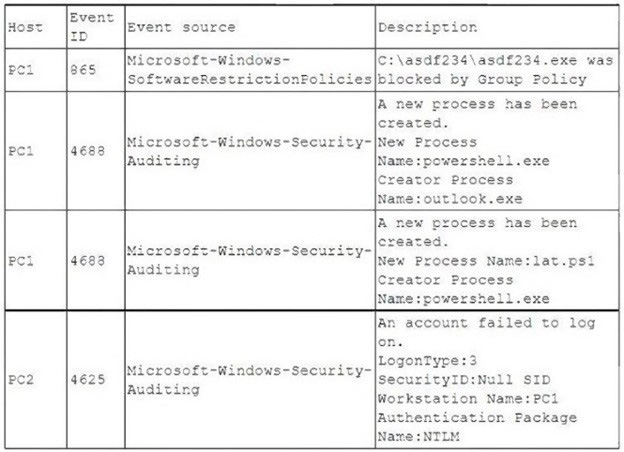
Which of the following describes the method that was used to compromise the laptop?
A. An attacker was able to move laterally from PC1 to PC2 using a pass-the-hash attack
B. An attacker was able to bypass application whitelisting by emailing a spreadsheet attachment with an embedded PowerShell in the file
C. An attacker was able to install malware to the CAasdf234 folder and use it to gam administrator nights and launch Outlook
D. An attacker was able to phish user credentials successfully from an Outlook user profile
-
Question 572:
A host was infected with malware. During the incident response, Joe, a user, reported that he did not receive any emails with links, but he had been browsing the Internet all day. Which of the following would MOST likely show where the malware originated?
A. The DNS logs
B. The web server logs
C. The SIP traffic logs
D. The SNMP logs
-
Question 573:
A Chief Security Officer (CSO) is concerned about the amount of PII that is stored locally on each salesperson's laptop. The sales department has a higher-than-average rate of lost equipment. Which of the following recommendations would BEST address the CSO's concern?
A. Deploy an MDM solution.
B. Implement managed FDE.
C. Replace all hard drives with SEDs.
D. Install DLP agents on each laptop.
-
Question 574:
A security analyst Is hardening a Linux workstation and must ensure It has public keys forwarded to remote systems for secure login Which of the following steps should the analyst perform to meet these requirements? (Select TWO).
A. Forward the keys using ssh-copy-id.
B. Forward the keys using scp.
C. Forward the keys using ash -i.
D. Forward the keys using openssl -s.
E. Forward the keys using ssh-keyger.
-
Question 575:
Against the recommendation of the IT security analyst, a company set all user passwords on a server as "P@)55wOrD". Upon review of the /etc/pesswa file, an attacker found the following:
alice:a8df3b6c4fd75f0617431fd248f35191df8d237f bob:2d250c5b2976b03d757f324ebd59340df96aa05e chris:ea981ec3285421d014108089f3f3f997ce0f4150
Which of the following BEST explains why the encrypted passwords do not match?
A. Perfect forward secrecy
B. Key stretching
C. Salting
D. Hashing
-
Question 576:
A company has limited storage space available and an online presence that cannot be down for more than four hours.
Which of the following backup methodologies should the company implement to allow for the FASTEST database restore time in the event of a failure, while being mindful of the limited available storage space?
A. Implement full tape backups every Sunday at 8:00 p.m. and perform nightly tape rotations.
B. Implement differential backups every Sunday at 8:00 p.m. and nightly incremental backups at 8:00 p.m.
C. Implement nightly full backups every Sunday at 8:00 p.m.
D. Implement full backups every Sunday at 8:00 p.m. and nightly differential backups at 8:00 p.m.
-
Question 577:
A security monitoring company offers a service that alerts its customers if their credit cards have been stolen. Which of the following is the MOST likely source of this information?
A. STIX
B. The dark web
C. TAXI
D. Social media
E. PCI
-
Question 578:
A security auditor is reviewing vulnerability scan data provided by an internal security team. Which of the following BEST indicates that valid credentials were used?
A. The scan results show open ports, protocols, and services exposed on the target host
B. The scan enumerated software versions of installed programs
C. The scan produced a list of vulnerabilities on the target host
D. The scan identified expired SSL certificates
-
Question 579:
A Chief Information Security Officer (CISO) is concerned about the organization's ability to continue business operation in the event of a prolonged DDoS attack on its local datacenter that consumes database resources. Which of the following will the CISO MOST likely recommend to mitigate this risk?
A. Upgrade the bandwidth available into the datacenter
B. Implement a hot-site failover location
C. Switch to a complete SaaS offering to customers
D. Implement a challenge response test on all end-user queries
-
Question 580:
A user recently attended an exposition and received some digital promotional materials The user later noticed blue boxes popping up and disappearing on the computer, and reported receiving several spam emails, which the user did not open Which of the following is MOST likely the cause of the reported issue?
A. There was a drive-by download of malware
B. The user installed a cryptominer
C. The OS was corrupted
D. There was malicious code on the USB drive
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.