Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 471:
Which of the following can work as an authentication method and as an alerting mechanism for unauthorized access attempts?
A. Smart card
B. push notifications
C. Attestation service
D. HMAC-based
E. one-time password
-
Question 472:
Which of the following techniques eliminates the use of rainbow tables for password cracking?
A. Hashing
B. Tokenization
C. Asymmetric encryption
D. Salting
-
Question 473:
A company discovered that terabytes of data have been exfiltrated over the past year after an employee clicked on an email link. The threat continued to evolve and remain undetected until a security analyst noticed an abnormal amount of external connections when the employee was not working. Which of the following is the MOST likely threat actor?
A. Shadow IT
B. Script kiddies
C. APT
D. Insider threat
-
Question 474:
A security analyst is tasked with classifying data to be stored on company servers. Which of the following should be classified as proprietary?
A. Customers' dates of birth
B. Customers' email addresses
C. Marketing strategies
D. Employee salaries
-
Question 475:
A security analyst is tasked with defining the "something you are" factor of the company's MFA settings. Which of the following is BEST to use to complete the configuration?
A. Gait analysis
B. Vein
C. Soft token
D. HMAC-based, one-time password
-
Question 476:
Several attempts have been made lo pick the door lock of a secure facility As a result the security engineer has been assigned to implement a stronger preventative access control Which of the following would BEST complete the engineer's assignment?
A. Replacing the traditional key with an RFID key
B. Installing and monitoring a camera facing the door
C. Setting motion-sensing lights to illuminate the door on activity
D. Surrounding the property with fencing and gates
-
Question 477:
A user forwarded a suspicious email to the security team, Upon investigation, a malicious URL was discovered. Which of the following should be done FIRST to prevent other users from accessing the malicious URL?
A. Configure the web content filter for the web address.
B. Report the website to threat intelligence partners
C. Set me SIEM to alert for any activity to the web address.
D. Send out a corporate communication to warn all users Of the malicious email.
-
Question 478:
Security analysts notice a server login from a user who has been on vacation for two weeks
The analysts confirm that the user did not log in to the system while on vacation After reviewing packet capture logs, the analysts notice the following:
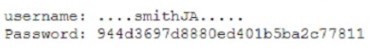
Which of the following occurred?
A. A buffer overflow was exploited to gain unauthorized access
B. The user's account was compromised, and an attacker changed the login credentials
C. An attacker used a pass-the-hash attack to gain access
D. An insider threat with username smithJA logged in to the account
-
Question 479:
Which of the following should an organization consider implementing In the event executives need to speak to the media after a publicized data breach?
A. Incident response plan
B. Business continuity plan
C. Communication plan
D. Disaster recovery plan
-
Question 480:
Which of the following prevents an employee from seeing a colleague who is visting an inappropriate website?
A. Job roration policy
B. NDA
C. AUP
D. Separation of duties policy
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.