Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 491:
While investigating a recent security incident, a security analyst decides to view all network connections on a particular server, Which of the following would provide the desired information?
A. arp
B. nslookup
C. netstat
D. nmap
-
Question 492:
A security analyst is reviewing application logs to determine the source of a breach and locates the following log: Which Of the following has been observed?
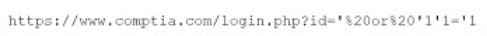
A. DLL Injection
B. API attack
C. SQLI
D. XSS
-
Question 493:
The new Chief Information Security Officer at a company has asked the security team to implement stronger user account policies. The new policies require:
1.
Users to choose a password unique to their last ten passwords
2.
Users to not log in from certain high-risk countries
Which of the following should the security team implement? (Select TWO).
A. Password complexity
B. Password history
C. Geolocation
D. Geofencing
E. Geotagging
F. Password reuse
-
Question 494:
Which of the following is the MOST likely reason for securing an air-gapped laboratory HVAC system?
A. To avoid data leakage
B. To protect surveillance logs
C. To ensure availability
D. To facilitate third-party access
-
Question 495:
During a security incident investigation, an analyst consults the company's SIEM and sees an event concerning high traffic to a known, malicious command-and-control server. The analyst would like to determine the number of company workstations that may be impacted by this issue. Which of the following can provide the information?
A. WAF logs
B. DNS logs
C. System logs
D. Application logs
-
Question 496:
A network engineer created two subnets that will be used for production and development servers. Per security policy, production and development servers must each have a dedicated network that cannot communicate with one another directly.
Which of the following should be deployed so that server administrators can access these devices?
A. VLANS
B. Internet proxy servers
C. NIDS
D. Jump servers
-
Question 497:
A Chief Information Security Officer wants to ensure the organization is validating and checking the Integrity of zone transfers. Which of the following solutions should be implemented?
A. DNSSEC
B. LOAPS
C. NGFW
D. DLP
-
Question 498:
A penetration tester is fuzzing an application to identify where the EIP of the stack is located on memory. Which of the following attacks is the penetration tester planning to execute?
A. Race-condition
B. Pass-the-hash
C. Buffer overflow
D. XSS
-
Question 499:
After a recent security breach, a security analyst reports that several administrative usernames and passwords are being sent via cleartext across the network to access network devices over port 23. Which of the following should be implemented so all credentials sent over the network are encrypted when remotely accessing and configuring network devices?
A. SSH
B. SNMPv3
C. SFTP
D. Telnet
E. FTP
-
Question 500:
Which of the following is a reason to publish files' hashes?
A. To validate the integrity of the files
B. To verify if the software was digitally signed
C. To use the hash as a software activation key
D. To use the hash as a decryption passphrase
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.