Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 811:
A systems administrator needs to configure an SSL remote access VPN according to the following organizational guidelines:
*
The VPN must support encryption of header and payload.
*
The VPN must route all traffic through the company's gateway. Which of the following should be configured on the VPN concentrator?
A.
Full tunnel
B.
Transport mode
C.
Tunnel mode
D.
IPSec
-
Question 812:
In which of the following risk management strategies would cybersecurity insurance be used?
A. Transference
B. Avoidance
C. Acceptance
D. Mitigation
-
Question 813:
While testing a new vulnerability scanner, a technician becomes concerned about reports that list security concerns that are not present on the systems being tested. Which of the following BEST describes this flaw?
A. False positives
B. Crossover error rate
C. Uncredentialed scan
D. Passive security controls
-
Question 814:
A systems engineer wants to leverage a cloud-based architecture with low latency between network- connected devices that also reduces the bandwidth that is required by performing analytics directly on the endpoints. Which of the following would BEST meet the requirements? (Select TWO).
A. Private cloud
B. SaaS
C. Hybrid cloud
D. laaS
E. DRaaS
F. Fog computing
-
Question 815:
A user from the financial aid office is having trouble interacting with the finaid directory on the university's ERP system. The systems administrator who took the call ran a command and received the following output:
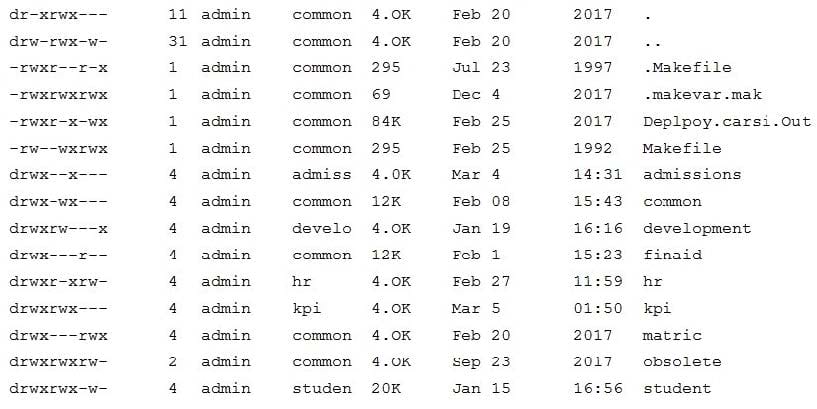
Subsequently, the systems administrator has also confirmed the user is a member of the finaid group on the ERP system. Which of the following is the MOST likely reason for the issue?
A. The permissions on the finaid directory should be drwxrwxrwx.
B. The problem is local to the user, and the user should reboot the machine.
C. The files on the finaid directory has an improper group assignment.
D. The finaid directory should be d---rwx--
-
Question 816:
Which of the following is a benefit of credentialed vulnerability scans?
A. Credentials provide access to scan documents to identify possible data theft.
B. The vulnerability scanner is able to inventory software on the target.
C. A scan will reveal data loss in real time.
D. Black-box testing can be performed.
-
Question 817:
An organization is drafting an IRP and needs to determine which employees have the authority to take systems offline during an emergency situation. Which of the following is being outlined?
A. Reporting and escalation procedures
B. Permission auditing
C. Roles and responsibilities
D. Communication methodologies
-
Question 818:
A systems administrator is installing and configuring an application service that requires access to read and write to log and configuration files on a local hard disk partition. The service must run as an account with authorization to interact with the file system. Which of the following would reduce the attack surface added by the service and account? (Select TWO)
A. Use a unique managed service account
B. Utilize a generic password for authenticating
C. Enable and review account audit logs
D. Enforce least possible privileges for the account
E. Add the account to the local administrator's group.
F. Use a guest account placed in a non-privileged users' group
-
Question 819:
The help desk received a call from a user who was trying to access a set of files from the day before but received the following error message: File format not recognized. Which of the following types of malware MOST likely caused this to occur?
A. Ransomware
B. Polymorphic virus
C. Rootkit
D. Spyware
-
Question 820:
A security analyst is emailing PII in a spreadsheet file to an audit validator for after-actions related to a security assessment. The analyst must make sure the PII data is protected with the following minimum requirements:
*
Ensure confidentiality at rest.
*
Ensure the integrity of the original email message.
Which of the following controls would ensure these data security requirements are carried out?
A.
Encrypt and sign the email using S/MIME.
B.
Encrypt the email and send it using TLS.
C.
Hash the email using SHA-1.
D.
Sign the email using MD5
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.