Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 781:
The application team within a company is asking the security team to investigate why its application is slow after an upgrade. The source of the team's application is 10.13.136.9. and the destination IP is 10.17.36.5. The security analyst pulls the logs from the endpoint security software but sees nothing is being blocked. The analyst then looks at the UTM firewall logs and sees the following:
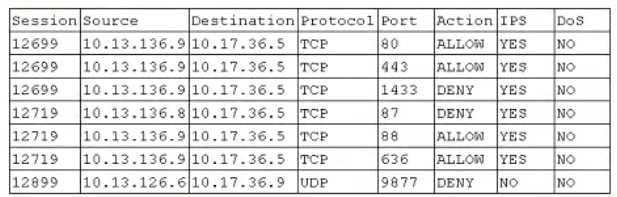
Which of the following should the security analyst request NEXT based on the UTM firewall analysis?
A. Request the application team to allow TCP port 87 to listen on 10.17.36.5.
B. Request the network team to open port 1433 from 10.13.136.9 to 10.17.36.5.
C. Request the network team to turn of IPS for 10.13.136.8 going to 10.17.36.5.
D. Request the application team to reconfigure the application and allow RPC communication.
-
Question 782:
Fuzzing is used to reveal which of the following vulnerabilities in web applications?
A. Weak cipher suites
B. Improper input handling
C. DLL injection
D. Certificate signing flaws
-
Question 783:
After a ransomware attack. a forensics company needs to review a cryptocurrency transaction between the victim and the attacker. Which of the following will the company MOST likely review to trace this transaction?
A. The public ledger
B. The NetFlow data
C. A checksum
D. The event log
-
Question 784:
A forensics analyst is investigating a hard drive for evidence of suspected illegal activity. Which of the following should the analyst do FIRST?
A. Create a hash of the hard drive.
B. Export the Internet history.
C. Save a copy of the case number and date as a text file in the root directory.
D. Back up the pictures directory for further inspection.
-
Question 785:
A coding error has been discovered on a customer-facing website. The error causes each request to return confidential PHI data for the incorrect organization. The IT department is unable to identify the specific customers who are affected. As a result, all customers must be notified of the potential breach. Which of the following would allow the team to determine the scope of future incidents?
A. Intrusion detection system
B. Database access monitoring
C. Application fuzzing
D. Monthly vulnerability scans
-
Question 786:
A system uses an application server and database server Employing the principle of least privilege, only database administrators are given administrative privileges on the database server, and only application team members are given administrative privileges on the application server. Audit and log file reviews are performed by the business unit (a separate group from the database and application teams). The organization wants to optimize operational efficiency when application or database changes are needed, but it also wants to enforce least privilege, prevent modification of log files, and facilitate the audit and log review performed by the business unit. Which of the following approaches would BEST meet the organization's goals?
A. Restrict privileges on the log file directory to "read only" and use a service account to send a copy of these files to the business unit.
B. Switch administrative privileges for the database and application servers. Give the application team administrative privileges on the database servers and the database team administrative privileges on the application servers.
C. Remove administrative privileges from both the database and application servers, and give the business unit "read only" privileges on the directories where the log files are kept.
D. Give the business unit administrative privileges on both the database and application servers so they can Independently monitor server activity.
-
Question 787:
A small business just recovered from a ransomware attack against its file servers by purchasing the decryption keys from the attackers. The issue was triggered by a phishing email and the IT administrator wants lo ensure il does not happen again. Which of the following should the IT administrator do FIRST after recovery?
A. Scan the NAS for residual or dormant malware and take new dally backups that are tested on a frequent basis.
B. Restrict administrative privileges and patch all systems and applications.
C. Rebuild all workstations and Install new antivirus software.
D. Implement application whitelisting and perform user application hardening.
-
Question 788:
After successfully breaking into several networks and infecting multiple machines with malware. hackers contact the network owners, demanding payment to remove the infection and decrypt files. The hackers threaten to publicly release information about the breach if they are not paid. Which of the following BEST describes these attackers?
A. Gray hat hackers
B. Organized crime
C. Insiders
D. Hacktivists
-
Question 789:
A security administrator in a bank is required to enforce an access control policy so no single individual is allowed to both initiate and approve financial transactions. Which of the following BEST represents the impact the administrator is deterring?
A. Principle of least privilege
B. External intruder
C. Conflict of Interest
D. Fraud
-
Question 790:
A systems engineer is setting up a RADIUS server to support a wireless network that uses certificate authentication. Which of the following protocols must be supported by both the RADIUS server and the WAPs?
A. CCMP
B. TKIP
C. WPS
D. EAP
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.