Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 701:
Which of the following is the proper use of a Faraday cage?
A. To block electronic signals sent to erase a cell phone
B. To capture packets sent to a honeypot during an attack
C. To protect hard disks from access during a forensics investigation
D. To restrict access to a building allowing only one person to enter at a time
-
Question 702:
An application developer has neglected to include input validation checks in the design of the company's new web application. An employee discovers that repeatedly submitting large amounts of data, including custom code to an application will allow the execution of the custom code at the administrator level. Which of the following BEST identifies this application attack?
A. Cross-site scripting
B. Clickjacking
C. Buffer overflow
D. Replay
-
Question 703:
A security administrator is reviewing the following firewall configuration after receiving reports that users are unable to connect to remote websites: 10 PERMIT FROM ANY TO:ANY PORT: 80 20 PERMIT FROM:ANY TO:ANY PORT: 443 30 DENY FROM: ANY TO:ANY PORT:ANY Which of the following is the MOST secure solution the security administrator can implement to fix this issue ?
A. Add the following rule to the firewall: 5 PERMIT FROM: ANY TO:ANY PORT:53
B. Replace rule number 10 with the following rule: 10 PERMIT FROM: ANY TO:ANY PORT:22
C. Insert the following rule in the firewall: 25 PERMIT FROM ANY TO:ANY PORTS:ANY
D. Remove the following rule from the firewall: 30 DENY FROM:ANY TO:ANY PORT:ANY
-
Question 704:
A company has a team of penetration testers. This team has located a file on the company file server that they believe contains cleartext usernames followed by a hash. Which of the following tools should the penetration testers use to learn more about the content of this file?
A. Exploitation framework
B. Vulnerability scanner
C. Netcat
D. Password cracker
-
Question 705:
During an audit, the auditor requests to see a copy of the identified mission-critical applications as well as their disaster recovery plans. The company being audited has an SLA around the applications it hosts. With which of the following is the auditor MOST likely concerned?
A. ARO/ALE
B. MTTR/MTBF
C. RTO/RPO
D. Risk assessment
-
Question 706:
A security analyst runs a monthly file integrity check on the main web server. When analyzing the logs, the analyst observed the following entry:
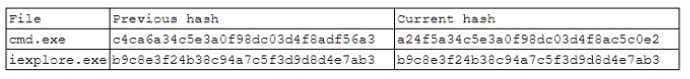
No OS patches were applied to this server during this period. Considering the log output, which of the following is the BEST conclusion?
A. The cmd.exe was executed on the scanned server between the two dates. An incident ticket should be created
B. The iexplore.exe was executed on the scanned server between the two dates. An incident ticket should be created.
C. The cmd.exe was updated on the scanned server. An incident ticket should be created
D. The iexplore.exe was updated on the scanned server. An incident ticket should be created.
-
Question 707:
A security technician is configuring a new firewall appliance for a production environment. The firewall must support secure web services for client workstations on the 10.10.10.0/24 network. The same client workstations are configured to contact a server at 192.168.1.15/24 for domain name resolution. Which of the following rules should the technician add to the firewall to allow this connectivity for the client workstations? (Select TWO).
A. Permit 10.10.10.0/24 0.0.0.0 -p tcp --dport 22
B. Permit 10.10.10.0/24 0.0.0.0 -p tcp --dport 80
C. Permit 10.10.10.0/24192.168.1.15/24 -p udp --dport 21
D. Permit 10.10.10.0/24 0.0.0.0-p tcp --dport 443
E. Permit 10.10.10.0/24 192.168.1.15/24 -p tcp --dport 53
F. Permit 10.10.10.0/24 192.168.1.15/24 -p udp --dport 53
-
Question 708:
Which of the following methods is used by internal security teams to assess the security of internally developed applications?
A. Active reconnaissance
B. Pivoting
C. White-box testing
D. Persistence
-
Question 709:
A company has just experienced a malware attack affecting a large number of desktop users. The antivirus solution was not able to block the malware, but the HIDS alerted to C2 calls as 'Troj.Generic'. Once the security team found a solution to remove the malware, they were able to remove the malware files successfully, and the HIDS stopped alerting. The next morning, however, the HIDS once again started alerting on the same desktops, and the security team discovered the files were back. Which of the following BEST describes the type of malware infecting this company's network?
A. Trojan
B. Spyware
C. Rootkit
D. Botnet
-
Question 710:
A security analyst is assessing a small company's internal servers against recommended security practices. Which of the following should the analyst do to conduct the assessment? (Select TWO).
A. Compare configurations against platform benchmarks,
B. Confirm adherence to the company's industry-specific regulations.
C. Review the company's current security baseline,
D. Verify alignment with policy related to regulatory compliance
E. Run an exploitation framework to confirm vulnerabilities
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.