Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 401:
In determining when it may be necessary to perform a credentialed scan against a system instead of a noncredentialed scan, which of the following requirements is MOST likely to influence this decision?
A. The scanner must be able to enumerate the host OS of devices scanned.
B. The scanner must be able to footprint the network.
C. The scanner must be able to check for open ports with listening services.
D. The scanner must be able to audit file system permissions
-
Question 402:
A security analyst is working on a project that requires the implementation of a stream cipher. Which of the following should the analyst use?
A. Hash function
B. Elliptic curve
C. Symmetric algorithm
D. Public key cryptography
-
Question 403:
A company recently replaced its unsecure email server with a cloud-based email and collaboration solution that is managed and insured by a third party. Which of the following actions did the company take regarding risks related to its email and collaboration services?
A. Transference
B. Acceptance
C. Mitigation
D. Deterrence
-
Question 404:
A security administrator is reviewing the following network capture:
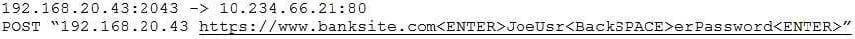
Which of the following malware is MOST likely to generate the above information?
A. Keylogger
B. Ransomware
C. Logic bomb
D. Adware
-
Question 405:
A network administrator adds an ACL to allow only HTTPS connections form host 192.168.2.3 to web server 192.168.5.2. After applying the rule, the host is unable to access the server. The network administrator runs the output and notices the configuration below:

Which of the following rules would be BEST to resolve the issue?
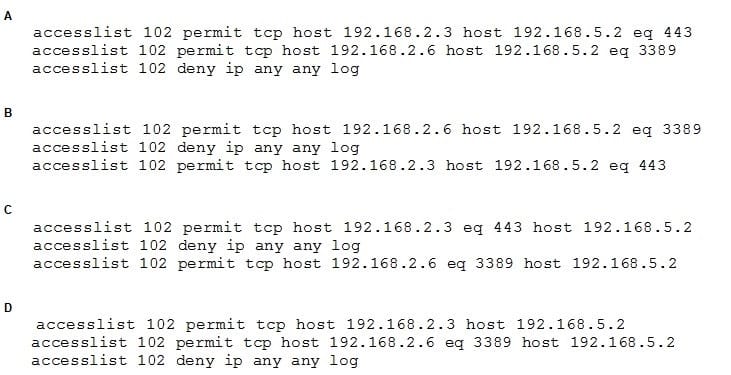
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 406:
A datacenter recently experienced a breach. When access was gained, an RF device was used to access an air-gapped and locked server rack. Which of the following would BEST prevent this type of attack?
A. Faraday cage
B. Smart cards
C. Infrared detection
D. Alarms
-
Question 407:
While performing a penetration test, the technicians want their efforts to go unnoticed for as long as possible while they gather useful data about the network they are assessing. Which of the following would be the BEST choice for the technicians?
A. Vulnerability scanner
B. Offline password cracker
C. Packet sniffer
D. Banner grabbing
-
Question 408:
A security analyst captures forensic evidence from a potentially compromised system for further investigation. The evidence is documented and securely stored to FIRST:
A. maintain the chain of custody.
B. preserve the data.
C. obtain a legal hold.
D. recover data at a later time.
-
Question 409:
A security analyst is investigating a security breach. Upon inspection of the audit an access logs, the analyst notices the host was accessed and the /etc/passwd file was modified with a new entry for username "gotcha" and user ID of 0. Which of the following are the MOST likely attack vector and tool the analyst should use to determine if the attack is still ongoing? (Select TWO)
A. Logic bomb
B. Backdoor
C. Keylogger
D. Netstat
E. Tracert
F. Ping
-
Question 410:
Which of the following penetration testing concepts is being used when an attacker uses public Internet databases to enumerate and learn more about a target?
A. Reconnaissance
B. Initial exploitation
C. Pivoting
D. Vulnerability scanning
E. White box testing
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.