Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 221:
Which of the following physical security controls is MOST effective when trying to prevent tailgating?
A. CCTV
B. Mantrap
C. Biometrics
D. RFID badge
E. Motion detection
-
Question 222:
Which of the following is the purpose of an industry-standard framework?
A. To promulgate compliance requirements for sales of common IT systems
B. To provide legal relief to participating organizations in the event of a security breach
C. To promulgate security settings on a vendor-by-vendor basis
D. To provide guidance across common system implementations
-
Question 223:
A security administrator wants to better prepare the incident response team for possible security events. The IRP has been updated and distributed to incident response team members. Which of the following is the BEST option to fulfill the administrator's objective?
A. Identify the member's roles and responsibilities
B. Select a backup/failover location
C. Determine the order of restoration
D. Conduct a tabletop test
-
Question 224:
A network administrator was provided the following output from a vulnerability scan:
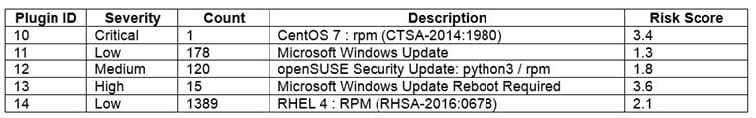
The network administrator has been instructed to prioritize remediation efforts based on overall risk to the enterprise. Which of the following plugin IDs should be remediated FIRST?
A. 10
B. 11
C. 12
D. 13
E. 14
-
Question 225:
A company notices that at 10 a.m. every Thursday, three users' computers become inoperable. The security analyst team discovers a file called where.pdf.exe that runs on system startup. The contents of where.pdf.exe are shown below:
@echo off if [c:\file.txt] deltree C:\
Based on the above information, which of the following types of malware was discovered?
A. Rootkit
B. Backdoor
C. Logic bomb
D. RAT
-
Question 226:
An email systems administrator is configuring the mail server to prevent spear phishing attacks through email messages. Which of the following refers to what the administrator is doing?
A. Risk avoidance
B. Risk mitigation
C. Risk transference
D. Risk acceptance
-
Question 227:
After running an online password cracking tool, an attacker recovers the following password:
gh ;j SKSTOi;618and
Based on the above information, which of the following technical controls have been implemented? (Choose two.)
A. Complexity
B. Encryption
C. Hashing
D. Length
E. Salting
F. Stretching
-
Question 228:
Which of the following controls is implemented in lieu of the primary security controls?
A. Compensating
B. Corrective
C. Detective
D. Deterrent
-
Question 229:
A transitive trust:
A. is automatically established between a parent and a child
B. is used to update DNS records
C. allows access to untrusted domains
D. can be used in place of a hardware token for logins
-
Question 230:
A security engineer is concerned about susceptibility to HTTP downgrade attacks because the current customer portal redirects users from port 80 to the secure site on port 443. Which of the following would be MOST appropriate to mitigate the attack?
A. DNSSEC
B. HSTS
C. Certificate pinning
D. OCSP
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.