Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1231:
A security analyst has identified malware that is propagating automatically to multiple systems on the network. Which of the following types of malware is MOST likely impacting the network?
A. Virus
B. Worm
C. Logic bomb
D. Backdoor
-
Question 1232:
An organization allows the use of open-source software as long as users perform a file integrity check on the executables and verify the file against hashes of known malware. A user downloads the following files from an open-source website:

After submitting the hashes to the malware registry, the user is alerted that 2f40 3221 33ad 8f34 1032 1adc 13ef 51a4 matches a known malware signature. The organization has been running all of the above software with no known issues. Which of the following actions should the user take and why?
A. Download and run the software but notify the organization's cybersecurity office. The malware registry has a false positive since the software has been running without any issues.
B. Do not run any of the software and notify the organization's cybersecurity office. The open-source website has been compromised, and none of the software can be trusted.
C. Download and run only webserver_82.exe and opendatabase_44.exe and notify the organization's cybersecurity office. Legacy versions of the software have been compromised.
D. Do not run webserver_82.exe and notify the organization's cybersecurity office. The software is malware.
-
Question 1233:
A systems administrator just issued the ssh-keygen
-
Question 1234:
A newly hired Chief Security Officer (CSO) is reviewing the company's IRP and notices the procedures for zero-day malware attacks are being poorly executed, resulting in the CSIRT failing to address and coordinate malware removal from the system. Which of the following phases would BEST address these shortcomings?
A. Identification
B. Lessons learned
C. Recovery
D. Preparation
E. Eradication
-
Question 1235:
A law firm wants to protect its customers' individual information, which is stored at a remote facility, from inadvertently being compromised through a violation of the security objectives. Which of the following BEST describes the customer information that is being stored at this facility?
A. Trade secrets
B. Personal health information
C. Proprietary
D. Confidential
-
Question 1236:
A technician wants to configure a wireless router at a small office that manages a family-owned dry cleaning business. The router will support five laptops, personal smartphones, a wireless printer, and occasional guests. Which of the following wireless configurations is BEST implemented in this scenario?
A. Single SSID with WPA2-Enterprise
B. 802.1X with a guest VLAN
C. Dual SSID with WPA2-PSK
D. Captive portal with two-factor authentication
-
Question 1237:
When choosing a hashing algorithm for storing passwords in a web database, which of the following is the BEST explanation for choosing HMAC-MD5 over simple MD5?
A. HMAC provides hardware acceleration, thus speeding up authentication
B. HMAC adds a transport layer handshake, which improves authentication
C. HMAC-MD5 can be decrypted faster, speeding up performance
D. HMAC-MD5 is more resistant to brute forcing
-
Question 1238:
Given the following:
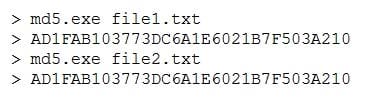
Which of the following concepts of cryptography is shown?
A. Collision
B. Salting
C. Steganography
D. Stream cipher
-
Question 1239:
Which of the following BEST explains "likelihood of occurrence"?
A. The chance that an event will happen regardless of how much damage it may cause
B. The overall impact to the organization once all factors have been considered
C. The potential for a system to have a weakness or flaw that might be exploited
D. The probability that a threat actor will target and attempt to exploit an organization's systems
-
Question 1240:
A security analyst receives the following output:

Which of the following MOST likely occurred to produce this output?
A. The host-based firewall prevented an attack from a Trojan horse
B. USB-OTG prevented a file from being uploaded to a mobile device
C. The host DLP prevented a file from being moved off a computer
D. The firewall prevented an incoming malware-infected file
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.