Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1191:
A company is planning to build an internal website that allows for access to outside contracts and partners. A majority of the content will only be to internal employees with the option to share.
Which of the following concepts is MOST appropriate?
A. VPN
B. Proxy
C. DMZ
D. Extranet
-
Question 1192:
A staff member contacts the help desk because the staff member's device is currently experiencing the following symptoms:
1.
Long delays when launching applications
2.
Timeout errors when loading some websites Errors when attempting to open local Word documents and photo files Pop-up messages in the task bar stating that antivirus is out-of-date VPN connection that keeps timing out, causing the device to lose connectivity
Which of the following BEST describes the root cause of these symptoms?
A. The user has disabled the antivirus software on the device, and the hostchecker for the VPN is preventing access.
B. The device is infected with crypto-malware, and the files on the device are being encrypted.
C. The proxy server for accessing websites has a rootkit installed, and this is causing connectivity issues.
D. A patch has been incorrectly applied to the device and is causing issues with the wireless adapter on the device.
-
Question 1193:
A security analyst is specifying requirements for a wireless network. The analyst must explain the security features provided by various architecture choices. Which of the following is provided by PEAP, EAP-TLS, and EAP-TTLS?
A. Key rotation
B. Mutual authentication
C. Secure hashing
D. Certificate pinning
-
Question 1194:
After discovering the /etc/shadow file had been rewritten, a security administrator noticed an application insecurely creating files in / tmp. Which of the following vulnerabilities has MOST likely been exploited?
A. Privilege escalation
B. Resource exhaustion
C. Memory leak
D. Pointer dereference
-
Question 1195:
A security analyst is checking log files and finds the following entries:
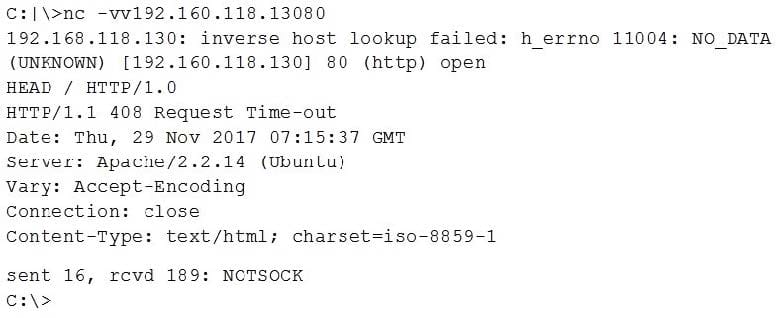
Which of the following is MOST likely happening?
A. A hacker attempted to pivot using the web server interface.
B. A potential hacker could be banner grabbing to determine what architecture is being used.
C. The DNS is misconfigured for the server's IP address.
D. A server is experiencing a DoS, and the request is timing out,
-
Question 1196:
Confidential corporate data was recently stolen by an attacker who exploited data transport protections. Which of the following vulnerabilities is the MOST likely cause of this data breach?
A. Resource exhaustion on VPN concentrators
B. Weak SSL cipher strength
C. Improper input handling on FTP site
D. Race condition on packet inspection firewall
-
Question 1197:
A member of the human resources department received the following email message after sending an email containing benefit and tax information to a candidate:
"Your message has been quarantined for the following policy violation: external potential_PII. Please contact the IT security administrator for further details". Which of the following BEST describes why this message was received?
A. The DLP system flagged the message.
B. The mail gateway prevented the message from being sent to personal email addresses.
C. The company firewall blocked the recipient's IP address.
D. The file integrity check failed for the attached files.
-
Question 1198:
A security administrator needs to configure remote access to a file share so it can only be accessed between the hours of 9:00 a.m. and 5:00 p.m. Files in the share can only be accessed by members of the same department as the data owner. Users should only be able to create files with approved extensions, which may differ by department.
Which of the following access controls would be the MOST appropriate for this situation?
A. RBAC
B. MAC
C. ABAC
D. DAC
-
Question 1199:
If two employees are encrypting traffic between them using a single encryption key, which of the following agorithms are they using?
A. RSA
B. 3DES
C. DSA
D. SHA-2
-
Question 1200:
An organization hosts a public-facing website that contains a login page for users who are registered and authorized to access a secure, non-public section of the site. That non-public site hosts information that requires multifactor authentication for access.
Which of the following access management approaches would be the BEST practice for the organization?
A. Username/password with TOTP
B. Username/password with pattern matching
C. Username/password with a PIN
D. Username/password with a CAPTCHA
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.