Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1161:
Joe, a member of the sales team, recently logged into the company servers after midnight local time to download the daily lead form before his coworkers did. Management has asked the security team to provide a method for detecting this
type of behavior without impeding the access for sales employee as they travel overseas.
Which of the following would be the BEST method to achieve this objective?
A. Configure time-of-day restrictions for the sales staff.
B. Install DLP software on the devices used by sales employees.
C. Implement a filter on the mail gateway that prevents the lead from being emailed.
D. Create an automated alert on the SIEM for anomalous sales team activity.
-
Question 1162:
An office recently completed digitizing all its paper records. Joe, the data custodian, has been tasked with the disposal of the paper files, which include:
1.
Intellectual property
2.
Payroll records
3.
Financial information
4.
Drug screening results
Which of the following is the BEST way to dispose of these items?
A. Shredding
B. Pulping
C. Deidentifying
D. Recycling
-
Question 1163:
Upon learning about a user who has reused the same password for the past several years, a security specialist reviews the logs. The following is an extraction of the report after the most recent password change requirement:
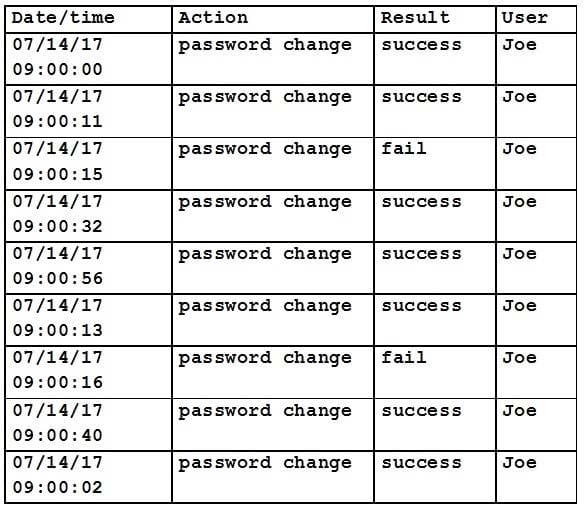
Which of the following security controls is the user's behavior targeting?
A. Password expiration
B. Password history
C. Password complexity
D. Password reuse
-
Question 1164:
In a lessons learned report, it is suspected that a well-organized, well-funded, and extremely sophisticated group of attackers may have been responsible for a breach at a nuclear facility. Which of the following describes the type of actors that may have been implicated?
A. Nation state
B. Hacktivist
C. Insider
D. Competitor
-
Question 1165:
A security administrator is analyzing a user report in which the computer exhibits odd network- related outages. The administrator, however, does not see any suspicious process running. A prior technician's notes indicate the machine has been remediated twice, but the system still exhibits odd behavior. Files were deleted from the system recently.
Which of the following is the MOST likely cause of this behavior?
A. Crypto-malware
B. Rootkit
C. Logic bomb
D. Session hijacking
-
Question 1166:
A company is performing an analysis of the corporate enterprise network with the intent of identifying any one system, person, function, or service that, when neutralized, will cause or cascade disproportionate damage to the company's revenue, referrals, and reputation.
Which of the following an element of the BIA that this action is addressing?
A. Identification of critical systems
B. Single point of failure
C. Value assessment
D. Risk register
-
Question 1167:
An analyst generates the following color-coded table shown in the exhibit to help explain the risk of potential incidents in the company. The vertical axis indicates the likelihood or an incident, while the horizontal axis indicates the impact.
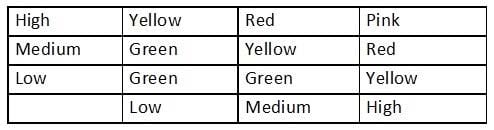
Which of the following is this table an example of?
A. Internal threat assessment
B. Privacy impact assessment
C. Qualitative risk assessment
D. Supply chain assessment
-
Question 1168:
Which of the following needs to be performed during a forensics investigation to ensure the data contained in a drive image has not been compromised?
A. Follow the proper chain of custody procedures.
B. Compare the image hash to the original hash.
C. Ensure a legal hold has been placed on the image.
D. Verify the time offset on the image file.
-
Question 1169:
Which of the following types of security testing is the MOST cost-effective approach used to analyze existing code and identity areas that require patching?
A. Black box
B. Gray box
C. White box
D. Red team
-
Question 1170:
A security analyst identified an SQL injection attack. Which of the following is the FIRST step in remediating the vulnerability?
A. Implement stored procedures.
B. Implement proper error handling.
C. Implement input validations.
D. Implement a WAF.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.