Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1101:
A transitive trust:
A. is automatically established between a parent and a child.
B. is used to update DNS records.
C. allows access to untrusted domains.
D. can be used in place of a hardware token for logins.
-
Question 1102:
An analyst is reviewing the following web-server log after receiving an alert from the DLP system about multiple PII records being transmitted in cleartext:
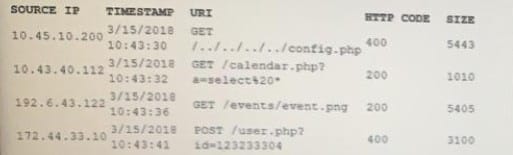
Which of the following IP addresses in MOST likely involved in the data leakage attempt?
A. 10.43.40.112
B. 10.45.10.200
C. 172.44.33.10
D. 192.4.43.122
-
Question 1103:
A computer forensics team is performing an integrity check on key systems files. The team is comparing the signatures of original baseline les with the latest signatures. The original baseline was taken on March 2, 2016. and was established to be clean of malware and uncorrupted. The latest tile signatures were generated yesterday. One file is known to be corrupted, but when the team compares the signatures of the original and latest ies, the team sees the Following:
Original: 2d da b1 4a fc f1 98 06 b1 e5 26 b2 df e5 5b 3e cb 83 e1
Latest: 2d da b1 4a 98 fc f1 98 bl e5 26 b2 df e5 5b 3e cb 83 e1
Which of the following is MOST likely the situation?
A. The forensics team must have reverted the system to the original date. Which resulted in an identical hash calculation?
B. The original baseline was compromised, so the corrupted le was always on the system.
C. The signature comparison is using two different algorithms that happen to have generated the same values.
D. The algorithm used to calculate the hash has a collision weakness, and an attacker has exploited it.
-
Question 1104:
An organization handling highly condential information needs to update its systems. Which of the following is the BEST method to prevent data compromise?
A. Wiping
B. Degaussing
C. Shredding
D. Purging
-
Question 1105:
A malicious actor compromises a legitimate website, configuring it to deliver malware to visitors of the website. Which of the following attacks does this describe?
A. Whaling
B. Watering hole
C. Impersonation
D. Spoofing
-
Question 1106:
The director of information security at a company has recently directed the security engineering team to implement new security technologies aimed at reducing the impact of insider threats. Which of the following tools has the team MOST likely deployed? (Select TWO).
A. DLF
B. UTM
C. SFTP
D. SSH
E. SSL
-
Question 1107:
A red team initiated a DoS attack on the management interface of a switch using a known vulnerability The monitoring solution then raised an alert prompting a network engineer to log in to the switch to diagnose the issue. When the engineer logged in. the red team was able to capture the credentials and subsequently log in to the switch. Which of the following actions should the network team take to prevent this type of breach from reoccurring?
A. Encrypt all communications with TLS 1 3
B. Transition from SNMPv2c to SNMPv3 with AES-256
C. Enable Secure Shell and disable Telnet
D. Use a password manager with complex passwords
-
Question 1108:
A company uses WPA2-PSK. and it appears there are multiple unauthorized devices connected to the wireless network A technician suspects this is because the wireless password has been shared with unauthorized individuals. Which of the following should the technician implement to BEST reduce the risk of this happening in the future?
A. Wireless guest isolation
B. 802.1X
C. WPS
D. MAC address blacklist
-
Question 1109:
A company recently experienced a security breach. The security start determined that the intrusion was due to an out-of-date proprietary software program running on a non- compliant server The server was imaged and copied onto a hardened VM. with the previous connections re-established. Which of the Mowing Is the NEXT step in the incident response process?
A. Recovery
B. Eradication
C. Lessons learned
D. Containment
E. Identification
-
Question 1110:
A penetration tester was able to connect to a company's internal network and perform scans and staged attacks for the duration of the testing period without being noticed. The SIEM did not alert the security team to the presence of the penetration tester's devices on the network. Which of the following would provide the security team with notification in a timely manner?
A. Implement rogue system detection and sensors.
B. Create a trigger on the IPS and alert the security team when unsuccessful logins occur.
C. Decrease the correlation threshold for alerts on the SIEM.
D. Run a credentialed vulnerability scan
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.