Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1051:
During certain vulnerability scanning scenarios, It is possible for the target system to react in unexpected ways. This type of scenario is MOST commonly known as:
A. intrusive testing.
B. a butter overflow.
C. a race condition
D. active reconnaissance.
-
Question 1052:
Ann a security analyst from a large organization has been instructed to use another more effective scanning tool After installing the tool on her desktop she started a full vulnerability scan After running the scan for eight hours. Ann finds that
there were no vulnerabilities identified.
Which of the following is the MOST likely cause of not receiving any vulnerabilities on the network?
A. The organization has a zero tolerance policy against not applying cybersecurity best practices
B. The organization had a proactive approach to patch management principles and practices
C. The security analyst credentials did not allow full administrative rights for the scanning tool
D. The security analyst just recently applied operating system level patches
-
Question 1053:
Which of the following types of vulnerability scans typically returns more detailed and thorough insights into actual system vulnerabilities?
A. Non-credentialed
B. Intrusive
C. Credentialed
D. Non-Intrusive
-
Question 1054:
During a penetration test, Joe, an analyst, contacts the target's service desk Impersonating a user, he attempts to obtain assistance with resetting an email password. Joe claims this needs to be done as soon as possible, as he is the vice president of sales and does not want to contact the Chief Operations Officer (COO) for approval, since the COO is on vacation. When challenged. Joe reaffirms that he needs this done immediately, and threatens to contact the service desk supervisor over the issue. Which of the following social engineering principles is Joe employing in this scenario'? (Select TWO).
A. Intimidation
B. Consensus
C. Familiarity
D. Scarcity
E. Authority
-
Question 1055:
A new network administrator is establishing network circuit monitoring guidelines to catch potentially malicious traffic. The administrator begins monitoring the NetFlow statistics tor the critical Internet circuit and notes the following data after two weeks.
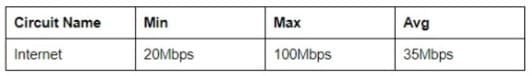
However, after checking the statistics from the weekend following the compiled statistics the administrator notices a spike in traffic to 250Mbps sustained for one hour The administrator is able to track the source of the spike to a server in the
DMZ.
Which of the following is the next BEST course of action the administrator should take?
A. Enable a packet capture on the firewall to catch the raw packets on the next occurrence
B. Consult the NetFlow logs on the NetFlow server to determine what data was being transferred
C. Immediately open a Seventy 1 case with the security analysts to address potential data exfiltration
D. Rerun the baseline data gathering for an additional four weeks and compare the results
-
Question 1056:
Exercising various programming responses for the purpose of gaming insight into a system's security posture without exploiting the system is BEST described as.
A. passive security control testing.
B. control gap analysis
C. peer-conducted code review.
D. non-intrusive scanning
-
Question 1057:
Which of the following controls is implemented in lieu of the primary security controls?
A. Compensating
B. Corrective
C. Detective
D. Deterrent
-
Question 1058:
Which of the following is the BEST example of a reputation impact identified during a risk assessment?
A. A bad software patch taking down the production systems.
B. A misconfigured firewall exposing intellectual properly to the internet.
C. An attacker defacing the e-commerce portal.
D. Malware collecting credentials for company bank accounts.
-
Question 1059:
Exploitation of a system using widely known credentials and network addresses that results in DoS is an example of:
A. improper error handling.
B. default configurations.
C. untrained users
D. lack of vendor support
-
Question 1060:
A security analyst receives the following output

Which of the following MOST likely occurred to produce this output?
A. The host-based firewall prevented an attack from a Trojan horse
B. USB-OTG prevented a file from being uploaded to a mobile device
C. The host DLP prevented a file from being moved off a computer
D. The firewall prevented an incoming malware-infected file
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.