SECRET-SEN Exam Details
-
Exam Code
:SECRET-SEN -
Exam Name
:CyberArk Sentry - Secrets Manager -
Certification
:CyberArk Certifications -
Vendor
:CyberArk -
Total Questions
:60 Q&As -
Last Updated
:Jan 16, 2026
CyberArk SECRET-SEN Online Questions & Answers
-
Question 1:
When installing the Vault Conjur Synchronizer, you see this error:
Forbidden
Logon Token is Empty ?Cannot logon
Unauthorized
What must you ensure to remediate the issue?
A. This admin user must not be logged in to other sessions during the Vault Conjur Synchronizer installation process.
B. You specified the correct url for Conjur and it is listed as a SAN on that url's certificate.
C. You correctly URI encoded the url in the installation script.
D. You ran powershell as Administrator and there is sufficient space on the server on which you are running the installation. -
Question 2:
What does "Line of business (LOB)" represent?
A. a business group requiring access to secrets from the Vault/Privilege Claud to facilitate syncing accounts to Conjur
B. the services that Conjur offers and typically refers to a group of application identities in Conjur
C. a business group that meets a certain set of Conjur policies for entitlements and policy management
D. the services that Conjur offers and typically refers to the list of configured and enabled authenticators in Conjur -
Question 3:
A Kubernetes application attempting to authenticate to the Follower load balancer receives this error:
ERROR: 2024/10/30 06:07:08 authenticator.go:139: CAKC029E Received invalid response to certificate signing request. Reason: status code 401 When checking the logs, you see this message:
authn-k8s/prd-cluster-01 is not enabled
How do you remediate the issue?
A. Check the info endpoint on each Follower behind the load balancer and enable the authenticator on the Follower.
B. Modify conjur.conf in /opt/conjur/etc/authenticators addinqthe authenticator webservice.
C. A network issue is preventing the application from reaching the Follower; correct the issue and verity that it is resolved.
D. Enable the authenticator in the Ul > Webservices > Authenticators > Enable and enable the appropriate authenticator webservice. -
Question 4:
Refer to the exhibit.
In which example will auto-failover occur?
A. Option A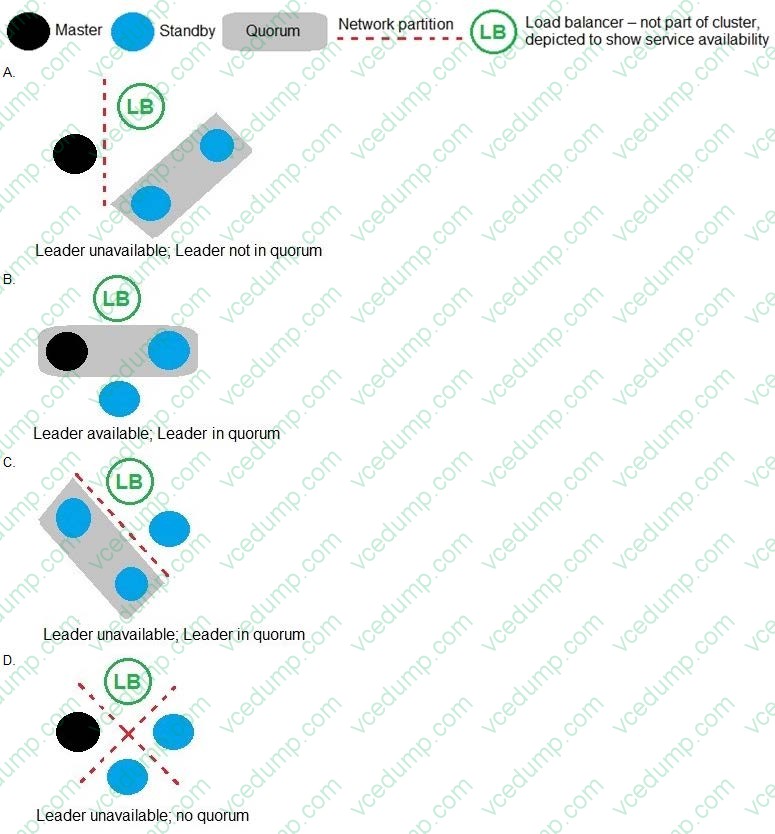
B. Option B
C. Option C
D. Option D -
Question 5:
While retrieving a secret through REST, the secret retrieval fails to find a matching secret. You know the secret onboarding process was completed, the secret is in the expected safe with the expected object name, and the CCP is able to provide secrets to other applications.
What is the most likely cause for this issue?
A. The application ID or Application Provider does not have the correct permissions on the safe.
B. The client certificate fingerprint is not trusted.
C. The service account running the application does not have the correct permissions on the safe.
D. The OS user does not have the correct permissions on the safe -
Question 6:
What is the correct command to import the root CA certificate into Conjur?
A. docker exec evoke ca import --no-restart --root;
B. docker exec evoke import --no-restart --root;
C. docker exec evoke ca import --no-restart;
D. docker exec ca import -
Question 7:
You are diagnosing this log entry: From Conjur logs:
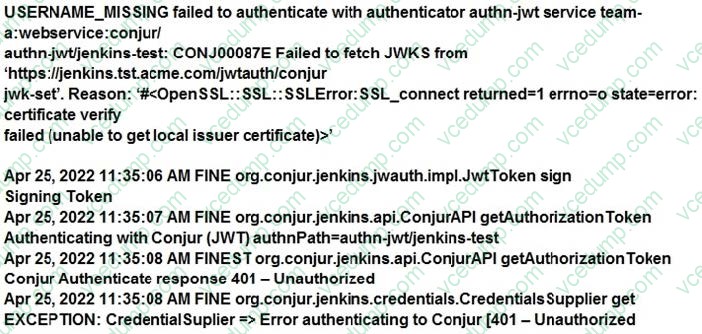
Given these errors, which problem is causing the breakdown?
A. The Jenkins certificate chain is not trusted by Conjur.
B. The Conjur certificate chain is not trusted by Jenkins.
C. The JWT sent by Jenkins does not match the Conjur host annotations.
D. The Jenkins certificate is malformed and will not be trusted by Conjur. -
Question 8:
You are setting up a Kubernetes integration with Conjur. With performance as the key deciding factor, namespace and service account will be used as identity characteristics.
Which authentication method should you choose?
A. JWT-based authentication
B. Certificate-based authentication
C. API key authentication
D. Connect (OIDC) authentication -
Question 9:
A customer requires high availability in its AWS cloud infrastructure.
What is the minimally viable Conjur deployment architecture to achieve this?
A. one Follower in each AZ. load balancer for the region
B. two Followers in each region, load balanced for the region
C. two Followers in each AZ. load balanced for the region
D. two Followers in each region, load balanced across all regions -
Question 10:
In the event of a failover of the Vault server from the primary to the DR, which configuration option ensures that a CP will continue being able to refresh its cache?
A. Add the DR Vault IP address to the "Address" parameter in the file main_appprovider.conf. . found in the AppProviderConf safe.
B. Add the IP address of the DR vault to the "Address" parameter in the file Vault.ini.file on the machine on which the CP is installed.
C. In the Password Vault Web Access UI, add the IP address of the DR Vault in the Disaster Recovery section under Applications > Options.
D. In the Conjur UI, add the IP address of the DR Vault in the Disaster Recovery section under Cluster Config > Credential Provider > Options.
Related Exams:
-
CAU201
CyberArk Defender -
CAU301
CyberArk Sentry -
CAU302
CyberArk Defender - Sentry -
CAU305
Sentry (Combined) CAU305 - CyberArk CDE Recertification -
CPC-SEN
CyberArk Sentry - Privilege Cloud -
EPM-DEF
CyberArk Defender - EPM -
PAM-CDE-RECERT
CyberArk CDE Recertification -
PAM-DEF
CyberArk Defender - PAM -
PAM-SEN
CyberArk Sentry PAM -
SECRET-SEN
CyberArk Sentry - Secrets Manager
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CyberArk exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SECRET-SEN exam preparations and CyberArk certification application, do not hesitate to visit our Vcedump.com to find your solutions here.