Exam Details
Exam Code
:SC-400Exam Name
:Microsoft Information Protection AdministratorCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:362 Q&AsLast Updated
:Aug 10, 2025
Microsoft Microsoft Certifications SC-400 Questions & Answers
-
Question 11:
You have a Microsoft 365 E5 subscription.
You need to prevent users from uploading data loss prevention (DLP)-protected documents to the following third-party websites:
1.
web1.contoso.com
2.
web2.contoso.com
The solution must minimize administrative effort.
To what should you set the Service domains setting for Endpoint DLP?
A. contoso.com
B. web*.contoso.com
C. *.contoso.com
D. web1.contoso.com and web2.contoso.com
-
Question 12:
You have a Microsoft 365 E5 subscription that contains multiple data loss prevention (DLP) policies.
You need to identify which DLP rules include conditions that can trigger the DLP policies.
Which report should you use from the Microsoft Purview compliance portal?
A. DLP policy matches
B. False positives and overrides
C. DLP incidents
D. Third-party DLP policy matches
-
Question 13:
You have a Microsoft 365 E5 tenant that contains a Microsoft SharePoint Online site named Site1 and a user named User1. The tenant has auditing enabled.
You need to ensure that User1 can perform disposition reviews. The solution must use the principle of the least privilege.
What should you do?
A. Assign User1 the Compliance Data Administrator role.
B. Add User1 to the Records Management role group.
C. Assign User1 the Data Investigator role.
D. Add User1 to the Content Explorer Content Viewer role group.
-
Question 14:
You have a Microsoft 365 E5 subscription that contains a trainable classifier named Trainable1. You plan to create the items shown in the following table.
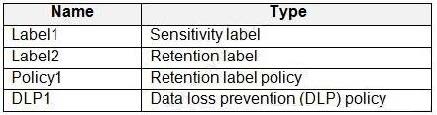
Which items can use Trainable1?
A. Label2 only
B. Label1 and Label2 only
C. Label1 and Policy1 only
D. Label2, Policy1, and DLP1 only
-
Question 15:
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1. Site1 contains a file named File1.
You have a retention policy named Retention1 that has the following settings:
Retention items for a specific period
-Retention period: 5 years
-
At the end of the retention period: Delete items automatically Retention1 is applied to Site1. You need to ensure that File1 is deleted automatically after seven years. The solution must NOT affect the retention of other files on Site1. What should you do first?
A.
Move File1 to a new folder and configure the access control list (ACL) entries for File1.
B.
Create a new retention policy.
C.
Create and publish a new retention label.
D.
Move File1 to a new folder and list the excluded locations for Retention1.
-
Question 16:
You have a Microsoft 365 E5 tenant that contains a Microsoft SharePoint Online document library named Library1.
You need to declare a collection of files that are stored in Library1 as regulatory records.
What should you use?
A. a sensitivity label policy
B. a retention label policy
C. a retention policy
D. data loss prevention (DLP) policy
-
Question 17:
You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1.
You need to implement a records management solution for the files stored on Site1. The solution must meet the following requirements:
The files must be retained for seven years.
Files older than seven years must be deleted automatically.
What should you use to manage the files?
A. a label policy
B. an adaptive scope
C. a file plan
D. a disposition review
-
Question 18:
You have a Microsoft 365 E5 subscription.
You need to create static retention policies for the following locations:
Teams chats Exchange email SharePoint sites Microsoft 365 Groups Teams channel messages
What is the minimum number of retention policies required?
A. 1
B. 2
C. 3
D. 4
E. 5
-
Question 19:
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
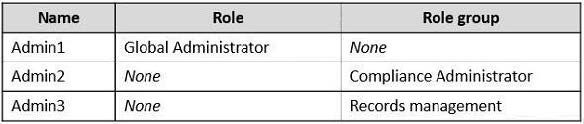
You create the retention label shown in the following exhibit.
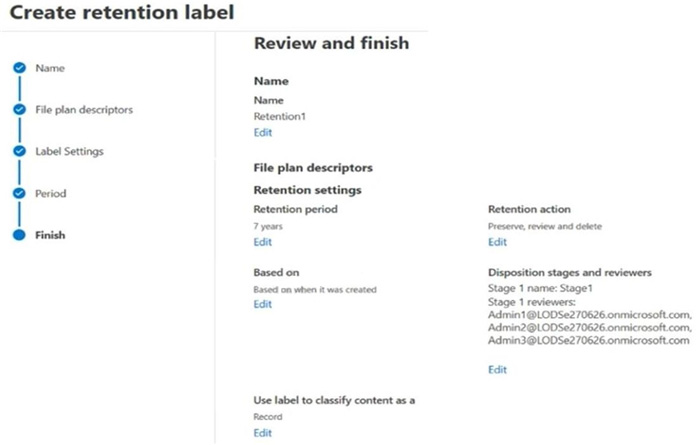
Which users can perform a disposition review of content that has Retention1 applied?
A. Admin2 only
B. Admin3 only
C. Admin1 and Admin2 only
D. Admin1 and Admin3 only
E. Admin2 and Admin3 only
F. Admin1, Admin2, and Admin3
-
Question 20:
You have a Microsoft 365 E5 tenant that uses Microsoft Teams and contains two users named User1 and User2.
You create a data loss prevention (DLP) policy that is applied to the Teams chat and channel messages location for User1 and User2.
Which Teams entities will have DLP protection?
A. 1:1/n chats and private channels only
B. 1:1/n chats and general channels only
C. 1:1/n chats, general channels, and private channels
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SC-400 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.