Exam Details
Exam Code
:PROFESSIONAL-CLOUD-DEVELOPERExam Name
:Professional Cloud DeveloperCertification
:Google CertificationsVendor
:GoogleTotal Questions
:254 Q&AsLast Updated
:
Google Google Certifications PROFESSIONAL-CLOUD-DEVELOPER Questions & Answers
-
Question 81:
You need to migrate a standalone Java application running in an on-premises Linux virtual machine (VM) to Google Cloud in a cost-effective manner. You decide not to take the lift- and-shift approach, and instead you plan to modernize the application by converting it to a container. How should you accomplish this task?
A. Use Migrate for Anthos to migrate the VM to your Google Kubernetes Engine (GKE) cluster as a container.
B. Export the VM as a raw disk and import it as an image. Create a Compute Engine instance from the Imported image.
C. Use Migrate for Compute Engine to migrate the VM to a Compute Engine instance, and use Cloud Build to convert it to a container.
D. Use Jib to build a Docker image from your source code, and upload it to Artifact Registry. Deploy the application in a GKE cluster, and test the application.
-
Question 82:
Your company has a data warehouse that keeps your application information in BigQuery. The BigQuery data warehouse keeps 2 PBs of user data. Recently, your company expanded your user base to include EU users and needs to comply
with these requirements:
Your company must be able to delete all user account information upon user request.
All EU user data must be stored in a single region specifically for EU users.
Which two actions should you take? (Choose two.)
A. Use BigQuery federated queries to query data from Cloud Storage.
B. Create a dataset in the EU region that will keep information about EU users only.
C. Create a Cloud Storage bucket in the EU region to store information for EU users only.
D. Re-upload your data using to a Cloud Dataflow pipeline by filtering your user records out.
E. Use DML statements in BigQuery to update/delete user records based on their requests.
-
Question 83:
You are deploying your application to a Compute Engine virtual machine instance with the Stackdriver
Monitoring Agent installed. Your application is a unix process on the instance. You want to be alerted if the unix process has not run for at least 5 minutes. You are not able to change the application to generate metrics or logs.
Which alert condition should you configure?
A. Uptime check
B. Process health
C. Metric absence
D. Metric threshold
-
Question 84:
You have deployed an HTTP(s) Load Balancer with the gcloud commands shown below.
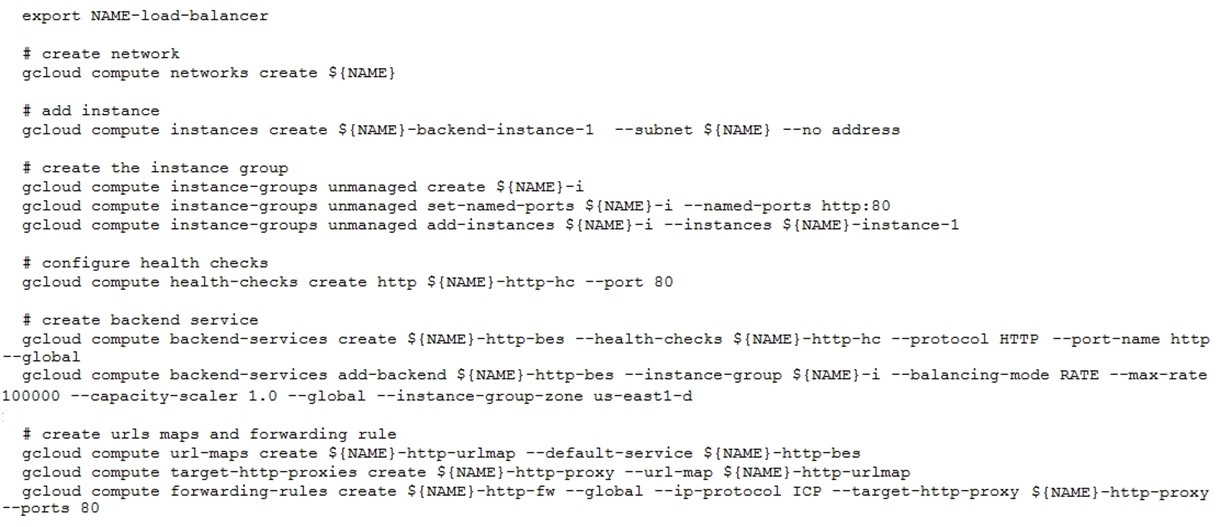
Health checks to port 80 on the Compute Engine virtual machine instance are failing and no traffic is sent to your instances. You want to resolve the problem. Which commands should you run?
A. gcloud compute instances add-access-config ${NAME}-backend-instance-1
B. gcloud compute instances add-tags ${NAME}-backend-instance-1 --tags http-server
C. gcloud compute firewall-rules create allow-lb --network load-balancer --allow tcp --source-ranges 130.211.0.0/22,35.191.0.0/16 --direction INGRESS
D. gcloud compute firewall-rules create allow-lb --network load-balancer --allow tcp --destination-ranges 130.211.0.0/22,35.191.0.0/16 --direction EGRESS
-
Question 85:
You are deploying a single website on App Engine that needs to be accessible via the URL http://www.altostrat.com/. What should you do?
A. Verify domain ownership with Webmaster Central. Create a DNS CNAME record to point to the App Engine canonical name ghs.googlehosted.com.
B. Verify domain ownership with Webmaster Central. Define an A record pointing to the single global App Engine IP address.
C. Define a mapping in dispatch.yaml to point the domain www.altostrat.com to your App Engine service. Create a DNS CNAME record to point to the App Engine canonical name ghs.googlehosted.com.
D. Define a mapping in dispatch.yaml to point the domain www.altostrat.com to your App Engine service. Define an A record pointing to the single global App Engine IP address.
-
Question 86:
Your company has a new security initiative that requires all data stored in Google Cloud to be encrypted by customer-managed encryption keys. You plan to use Cloud Key Management Service (KMS) to configure access to the keys. You need to follow the "separation of duties" principle and Google-recommended best practices. What should you do? (Choose two.)
A. Provision Cloud KMS in its own project.
B. Do not assign an owner to the Cloud KMS project.
C. Provision Cloud KMS in the project where the keys are being used.
D. Grant the roles/cloudkms.admin role to the owner of the project where the keys from Cloud KMS are being used.
E. Grant an owner role for the Cloud KMS project to a different user than the owner of the project where the keys from Cloud KMS are being used.
-
Question 87:
You are developing a web application that will be accessible over both HTTP and HTTPS and will run on Compute Engine instances. On occasion, you will need to SSH from your remote laptop into one of the Compute Engine instances to conduct maintenance on the app. How should you configure the instances while following Google-recommended best practices?
A. Set up a backend with Compute Engine web server instances with a private IP address behind a TCP proxy load balancer.
B. Configure the firewall rules to allow all ingress traffic to connect to the Compute Engine web servers, with each server having a unique external IP address.
C. Configure Cloud Identity-Aware Proxy API for SSH access. Then configure the Compute Engine servers with private IP addresses behind an HTTP(s) load balancer for the application web traffic.
D. Set up a backend with Compute Engine web server instances with a private IP address behind an HTTP(S) load balancer. Set up a bastion host with a public IP address and open firewall ports. Connect to the web instances using the bastion host.
-
Question 88:
You are writing from a Go application to a Cloud Spanner database. You want to optimize your application's performance using Google-recommended best practices. What should you do?
A. Write to Cloud Spanner using Cloud Client Libraries.
B. Write to Cloud Spanner using Google API Client Libraries
C. Write to Cloud Spanner using a custom gRPC client library.
D. Write to Cloud Spanner using a third-party HTTP client library.
-
Question 89:
You are creating an App Engine application that writes a file to any user's Google Drive. How should the application authenticate to the Google Drive API?
A. With an OAuth Client ID that uses the https://www.googleapis.com/auth/drive.file scope to obtain an access token for each user.
B. With an OAuth Client ID with delegated domain-wide authority.
C. With the App Engine service account and https://www.googleapis.com/auth/drive.file scope that generates a signed JWT.
D. With the App Engine service account with delegated domain-wide authority.
-
Question 90:
You are developing a corporate tool on Compute Engine for the finance department, which needs to authenticate users and verify that they are in the finance department. All company employees use G Suite. What should you do?
A. Enable Cloud Identity-Aware Proxy on the HTTP(s) load balancer and restrict access to a Google Group containing users in the finance department. Verify the provided JSON Web Token within the application.
B. Enable Cloud Identity-Aware Proxy on the HTTP(s) load balancer and restrict access to a Google Group containing users in the finance department. Issue client-side certificates to everybody in the finance team and verify the certificates in the application.
C. Configure Cloud Armor Security Policies to restrict access to only corporate IP address ranges. Verify the provided JSON Web Token within the application.
D. Configure Cloud Armor Security Policies to restrict access to only corporate IP address ranges. Issue client side certificates to everybody in the finance team and verify the certificates in the application.
Related Exams:
ADWORDS-DISPLAY
Google AdWords: Display AdvertisingADWORDS-FUNDAMENTALS
Google AdWords: FundamentalsADWORDS-MOBILE
Google AdWords: Mobile AdvertisingADWORDS-REPORTING
Google AdWords: ReportingADWORDS-SEARCH
Google AdWords: Search AdvertisingADWORDS-SHOPPING
Google AdWords: Shopping AdvertisingADWORDS-VIDEO
Google AdWords: Video AdvertisingAPIGEE-API-ENGINEER
Apigee Certified API EngineerASSOCIATE-ANDROID-DEVELOPER
Associate Android Developer (Kotlin and Java)ASSOCIATE-CLOUD-ENGINEER
Associate Cloud Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Google exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PROFESSIONAL-CLOUD-DEVELOPER exam preparations and Google certification application, do not hesitate to visit our Vcedump.com to find your solutions here.