Exam Details
Exam Code
:PROFESSIONAL-CLOUD-DEVELOPERExam Name
:Professional Cloud DeveloperCertification
:Google CertificationsVendor
:GoogleTotal Questions
:254 Q&AsLast Updated
:Jul 06, 2025
Google Google Certifications PROFESSIONAL-CLOUD-DEVELOPER Questions & Answers
-
Question 91:
Your team develops services that run on Google Cloud. You need to build a data processing service and will use Cloud Functions. The data to be processed by the function is sensitive. You need to ensure that invocations can only happen from authorized services and follow Google-recommended best practices for securing functions. What should you do?
A. Enable Identity-Aware Proxy in your project. Secure function access using its permissions.
B. Create a service account with the Cloud Functions Viewer role. Use that service account to invoke the function.
C. Create a service account with the Cloud Functions Invoker role. Use that service account to invoke the function.
D. Create an OAuth 2.0 client ID for your calling service in the same project as the function you want to secure. Use those credentials to invoke the function.
-
Question 92:
Your application is running on Compute Engine and is showing sustained failures for a small number of requests. You have narrowed the cause down to a single Compute Engine instance, but the instance is unresponsive to SSH. What should you do next?
A. Reboot the machine.
B. Enable and check the serial port output.
C. Delete the machine and create a new one.
D. Take a snapshot of the disk and attach it to a new machine.
-
Question 93:
Your existing application keeps user state information in a single MySQL database. This state information is
very user-specific and depends heavily on how long a user has been using an application.
The MySQL
database is causing challenges to maintain and enhance the schema for various users.
Which storage option should you choose?
A. Cloud SQL
B. Cloud Storage
C. Cloud Spanner
D. Cloud Datastore/Firestore
-
Question 94:
You are a SaaS provider deploying dedicated blogging software to customers in your Google Kubernetes Engine (GKE) cluster. You want to configure a secure multi-tenant platform to ensure that each customer has access to only their own blog and can't affect the workloads of other customers. What should you do?
A. Enable Application-layer Secrets on the GKE cluster to protect the cluster.
B. Deploy a namespace per tenant and use Network Policies in each blog deployment.
C. Use GKE Audit Logging to identify malicious containers and delete them on discovery.
D. Build a custom image of the blogging software and use Binary Authorization to prevent untrusted image deployments.
-
Question 95:
You work for an organization that manages an ecommerce site. Your application is deployed behind a global HTTP(S) load balancer. You need to test a new product recommendation algorithm. You plan to use A/B testing to determine the new algorithm's effect on sales in a randomized way. How should you test this feature?
A. Split traffic between versions using weights.
B. Enable the new recommendation feature flag on a single instance.
C. Mirror traffic to the new version of your application.
D. Use HTTP header-based routing.
-
Question 96:
You are developing an application that will be launched on Compute Engine instances into multiple distinct projects, each corresponding to the environments in your software development process (development, QA, staging, and production).
The instances in each project have the same application code but a different configuration. During deployment, each instance should receive the application's configuration based on the environment it serves. You want to minimize the
number of steps to configure this flow.
What should you do?
A. When creating your instances, configure a startup script using the gcloud command to determine the project name that indicates the correct environment.
B. In each project, configure a metadata key "environment" whose value is the environment it serves. Use your deployment tool to query the instance metadata and configure the application based on the "environment" value.
C. Deploy your chosen deployment tool on an instance in each project. Use a deployment job to retrieve the appropriate configuration file from your version control system, and apply the configuration when deploying the application on each instance.
D. During each instance launch, configure an instance custom-metadata key named "environment" whose value is the environment the instance serves. Use your deployment tool to query the instance metadata, and configure the application based on the "environment" value.
-
Question 97:
You are developing a web application that contains private images and videos stored in a Cloud Storage bucket. Your users are anonymous and do not have Google Accounts. You want to use your application-specific logic to control access to the images and videos. How should you configure access?
A. Cache each web application user's IP address to create a named IP table using Google Cloud Armor. Create a Google Cloud Armor security policy that allows users to access the backend bucket.
B. Grant the Storage Object Viewer IAM role to allUsers. Allow users to access the bucket after authenticating through your web application.
C. Configure Identity-Aware Proxy (IAP) to authenticate users into the web application. Allow users to access the bucket after authenticating through IAP.
D. Generate a signed URL that grants read access to the bucket. Allow users to access the URL after authenticating through your web application.
-
Question 98:
You are creating a Google Kubernetes Engine (GKE) cluster and run this command:
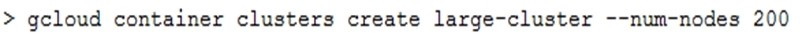
The command fails with the error:

You want to resolve the issue. What should you do?
A. Request additional GKE quota is the GCP Console.
B. Request additional Compute Engine quota in the GCP Console.
C. Open a support case to request additional GKE quotA.
D. Decouple services in the cluster, and rewrite new clusters to function with fewer cores.
-
Question 99:
You recently deployed your application in Google Kubernetes Engine, and now need to release a new version of your application. You need the ability to instantly roll back to the previous version in case there are issues with the new version. Which deployment model should you use?
A. Perform a rolling deployment, and test your new application after the deployment is complete.
B. Perform A/B testing, and test your application periodically after the new tests are implemented.
C. Perform a blue/green deployment, and test your new application after the deployment is. complete.
D. Perform a canary deployment, and test your new application periodically after the new version is deployed.
-
Question 100:
Your analytics system executes queries against a BigQuery dataset. The SQL query is executed in batch and passes the contents of a SQL file to the BigQuery CLI. Then it redirects the BigQuery CLI output to another process. However, you are getting a permission error from the BigQuery CLI when the queries are executed. You want to resolve the issue. What should you do?
A. Grant the service account BigQuery Data Viewer and BigQuery Job User roles.
B. Grant the service account BigQuery Data Editor and BigQuery Data Viewer roles.
C. Create a view in BigQuery from the SQL query and SELECT* from the view in the CLI.
D. Create a new dataset in BigQuery, and copy the source table to the new dataset Query the new dataset and table from the CLI.
Related Exams:
ADWORDS-DISPLAY
Google AdWords: Display AdvertisingADWORDS-FUNDAMENTALS
Google AdWords: FundamentalsADWORDS-MOBILE
Google AdWords: Mobile AdvertisingADWORDS-REPORTING
Google AdWords: ReportingADWORDS-SEARCH
Google AdWords: Search AdvertisingADWORDS-SHOPPING
Google AdWords: Shopping AdvertisingADWORDS-VIDEO
Google AdWords: Video AdvertisingAPIGEE-API-ENGINEER
Apigee Certified API EngineerASSOCIATE-ANDROID-DEVELOPER
Associate Android Developer (Kotlin and Java)ASSOCIATE-CLOUD-ENGINEER
Associate Cloud Engineer
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Google exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PROFESSIONAL-CLOUD-DEVELOPER exam preparations and Google certification application, do not hesitate to visit our Vcedump.com to find your solutions here.