Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 61:
After some firewall configuration changes, an administrator discovers that application identification has started failing. The administrator investigates further and notices that a high number of sessions were going to a discard state with the
application showing as unknown-tcp.
Which possible firewall change could have caused this issue?
A. enabling Forward segments that exceed the TCP App-ID inspection queue in Device > Setup > Content-ID > Content-ID Settings
B. enabling Forward segments that exceed the TCP content inspection queue in Device > Setup > Content-ID > Content-ID Settings
C. Jumbo frames were enabled on the firewall, which reduced the App-ID queue size and the number of available packet buffers.
D. Jumbo frames were disabled on the firewall, which reduced the queue sizes dedicated for out-of-order and application identification.
-
Question 62:
A network administrator notices there is a false-positive situation after enabling Security profiles. When the administrator checks the threat prevention logs, the related signature displays: threat type: spyware category: dns-c2 threat ID:
1000011111
Which set of steps should the administrator take to configure an exception for this signature?
A. Navigate to Objects > Security Profiles > Anti-Spyware Select related profile Select the signature exceptions tab and then click show all signatures Search related threat ID and click enable Change the default action Commit
B. Navigate to Objects > Security Profiles > Anti-Spyware Select related profile Select the Exceptions tab and then click show all signatures Search related threat ID and click enable Commit
C. Navigate to Objects > Security Profiles > Vulnerability Protection Select related profile Select the Exceptions tab and then click show all signatures Search related threat ID and click enable Commit
D. Navigate to Objects > Security Profiles > Anti-Spyware Select related profile Select DNS exceptions tabs Search related threat ID and click enable Commit
-
Question 63:
An engineer is attempting to resolve an issue with slow traffic.
Which PAN-OS feature can be used to prioritize certain network traffic?
A. Prisma Access for Mobile Users
B. Forward Error Correction (FEC)
C. SaaS Quality Profile
D. Quality of Service (QoS)
-
Question 64:
An administrator wants to enable Palo Alto Networks cloud services for Device Telemetry and IoT.
Which type of certificate must be installed?
A. External CA certificate
B. Server certificate
C. Device certificate
D. Self-signed root CA certificate
-
Question 65:
Which Palo Alto Networks tool provides configuration heat map displays for security controls?
A. Expedition
B. Security Life Cycle Review
C. Prevention Posture Assessment
D. Best Practice Assessment
-
Question 66:
Which three authentication types can be used to authenticate users? (Choose three.)
A. Local database authentication
B. PingID
C. Kerberos single sign-on
D. GlobalProtect client
E. Cloud authentication service
-
Question 67:
Which three options does Panorama offer for deploying dynamic updates to its managed devices? (Choose three.)
A. Check dependencies
B. Schedules
C. Verify
D. Revert content
E. Install
-
Question 68:
Given the Sample Log Forwarding Profile shown, which two statements are true? (Choose two.)
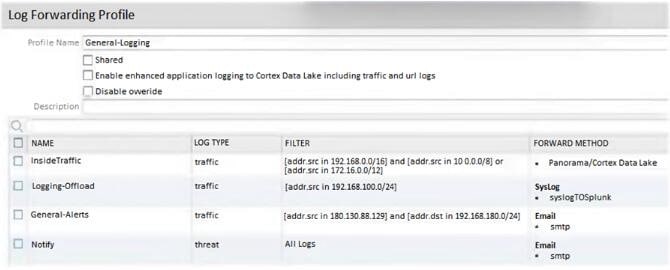
A. All traffic from source network 192.168.100.0/24 is sent to an external syslog target.
B. All threats are logged to Panorama.
C. All traffic logs from RFC 1918 subnets are logged to Panorama / Cortex Data Lake.
D. All traffic from source network 172.12.0.0/24 is sent to Panorama / Cortex Data Lake.
-
Question 69:
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
A. A Certificate profile should be configured with a trusted root CA.
B. An SSL/TLS Service profile should be configured with a certificate assigned.
C. An Interface Management profile with HTTP and HTTPS enabled should be configured.
D. An Authentication profile with the allow list of users should be configured.
-
Question 70:
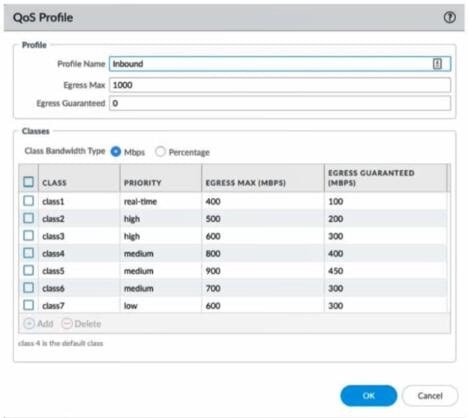
A QoS profile is configured as shown in the image. The following throughput is realized: Class 3 traffic 325Mbps Class 5 traffic 470Mbps Class 7 traffic: 330Mbps What happens as a result?
A. Available bandwidth from the unused classes will be used to maintain the Egress Guaranteed throughput for each.
B. Class 7 traffic will have the most packets dropped in favor of Classes 3 and 5 maintaining their Egress Guaranteed throughput.
C. All traffic continues to flow based on the overhead in each class's Egress Max settings.
D. Classes 3, 5, and 7 will each have round-robin packet drops as needed against the profile Egress Max.
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.