Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 361:
What can missing SSL packets when performing a packet capture on dataplane interfaces?
A. The packets are hardware offloaded to the offloaded processor on the dataplane
B. The missing packets are offloaded to the management plane CPU
C. The packets are not captured because they are encrypted
D. There is a hardware problem with offloading FPGA on the management plane
-
Question 362:
Which two methods can be used to mitigate resource exhaustion of an application server? (Choose two)
A. Vulnerability Object
B. DoS Protection Profile
C. Data Filtering Profile
D. Zone Protection Profile
-
Question 363:
Which operation will impact performance of the management plane?
A. DoS protection
B. WildFire submissions
C. generating a SaaS Application report
D. decrypting SSL sessions
-
Question 364:
Which three log-forwarding destinations require a server profile to be configured? (Choose three)
A. SNMP Trap
B. Email
C. RADIUS
D. Kerberos
E. Panorama
F. Syslog
-
Question 365:
What are three valid actions in a File Blocking Profile? (Choose three)
A. Forward
B. Block
C. Alret
D. Upload
E. Reset-both
F. Continue
-
Question 366:
A company hosts a publically accessible web server behind a Palo Alto Networks next generation firewall with the following configuration information.
Users outside the company are in the "Untrust-L3" zone The web server physically resides in the "Trust-L3" zone. Web server public IP address: 23.54.6.10 Web server private IP address: 192.168.1.10
Which two items must be NAT policy contain to allow users in the untrust-L3 zone to access the web server? (Choose two)
A. Untrust-L3 for both Source and Destination zone
B. Destination IP of 192.168.1.10
C. Untrust-L3 for Source Zone and Trust-L3 for Destination Zone
D. Destination IP of 23.54.6.10
-
Question 367:
Which three rule types are available when defining policies in Panorama? (Choose three.)
A. Pre Rules
B. Post Rules
C. Default Rules
D. Stealth Rules
E. Clean Up Rules
-
Question 368:
A company hosts a publicly accessible web server behind a Palo Alto Networks next- generation firewall with the following configuration information:
*
Users outside the company are in the "Untrust-L3" zone.
*
The web server physically resides in the "Trust-L3" zone.
*
Web server public IP address: 23.54.6.10
*
Web server private IP address: 192.168.1.10
Which two items must the NAT policy contain to allow users in the Untrust-L3 zone to access the web server? (Choose two.)
A.
Destination IPof 23.54.6.10
B.
UntrustL3 for both Source and Destination Zone
C.
Destination IP of 192.168.1.10
D.
UntrustL3 for Source Zone and Trust-L3 for Destination Zone
-
Question 369:
Palo Alto Networks maintains a dynamic database of malicious domains.
Which two Security Platform components use this database to prevent threats? (Choose two)
A. Brute-force signatures
B. BrightCloud Url Filtering
C. PAN-DB URL Filtering
D. DNS-based command-and-control signatures
-
Question 370:
Click the Exhibit button An administrator has noticed a large increase in bittorrent activity. The administrator wants to determine where the traffic is going on the company.
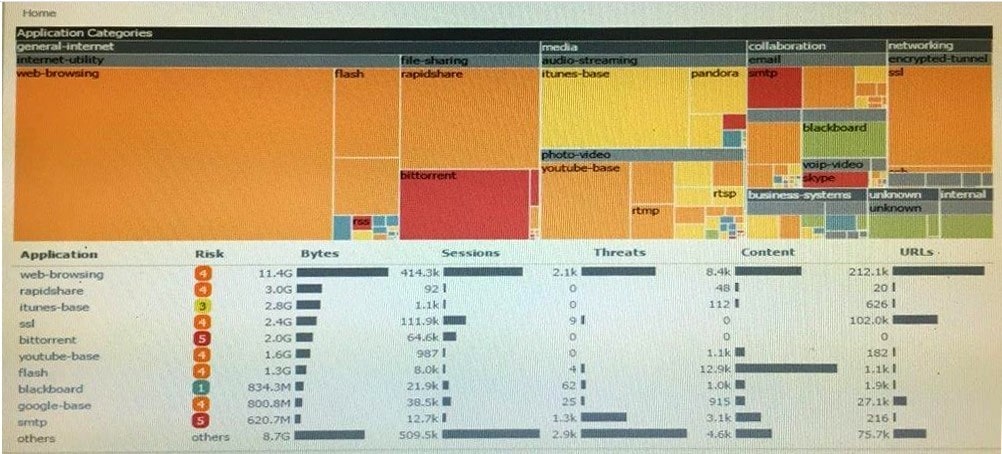
What would be the administrator's next step?
A. Right-Click on the bittorrent link and select Value from the context menu
B. Create a global filter for bittorrent traffic and then view Traffic logs.
C. Create local filter for bittorrent traffic and then view Traffic logs.
D. Click on the bittorrent application link to view network activity
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.