Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 321:
An administrator is configuring a Panorama device group
Which two objects are configurable? (Choose two )
A. DNS Proxy
B. Address groups
C. SSL/TLS roles
D. URL Filtering profiles
-
Question 322:
An engineer discovers the management interface is not routable to the User-ID agent What configuration is needed to allow the firewall to communicate to the User-ID agent?
A. Create a NAT policy for the User-ID agent server
B. Add a Policy Based Forwarding (PBF) policy to the User-ID agent IP
C. Create a custom service route for the UID Agent
D. Add a static route to the virtual router
-
Question 323:
A network security engineer configured IP multicast in the virtual router to support a new application. Users in different network segments are reporting that they are unable to access the application.
What must be enabled to allow an interface to forward multicast traffic?
A. IGMP
B. PIM
C. BFD
D. SSM
-
Question 324:
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0. What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
A. No client configuration is required for explicit proxy, which simplifies the deployment complexity.
B. Explicit proxy allows for easier troubleshooting, since the client browser is aware of the existence of the proxy.
C. Explicit proxy supports interception of traffic using non-standard HTTPS ports.
D. It supports the X-Authenticated-User (XAU) header, which contains the authenticated username in the outgoing request
-
Question 325:
An engineer receives reports from users that applications are not working and that websites are only partially loading in an asymmetric environment. After investigating, the engineer observes the flow_tcp_non_syn_drop counter increasing in the show counters global output.
Which troubleshooting command should the engineer use to work around this issue?
A. set deviceconfig setting tcp asymmetric-path drop
B. set deviceconfig setting session tcp-reject-non-syn no
C. set session tcp-reject-non-syn yes
D. set deviceconfig setting tcp asymmetric-path bypass
-
Question 326:
Which source is the most reliable for collecting User-ID user mapping?
A. GlobalProtect
B. Microsoft Active Directory
C. Microsoft Exchange
D. Syslog Listener
-
Question 327:
Where is Palo Alto Networks Device Telemetry data stored on a firewall with a device certificate installed?
A. Cortex Data Lake
B. Panorama
C. On Palo Alto Networks Update Servers
D. M600 Log Collectors
-
Question 328:
A company has configured GlobalProtect to allow their users to work from home. A decrease in performance for remote workers has been reported during peak-use hours. Which two steps are likely to mitigate the issue? (Choose TWO)
A. Exclude video traffic
B. Enable decryption
C. Block traffic that is not work-related
D. Create a Tunnel Inspection policy
-
Question 329:
An engineer reviews high availability (HA) settings to understand a recent HA failover event. Review the screenshot below.
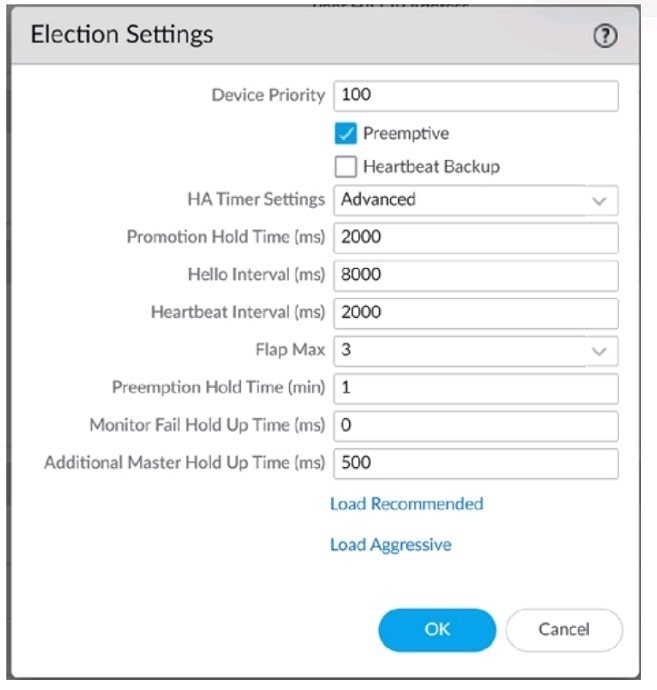
Which timer determines the frequency at which the HA peers exchange messages in the form of an ICMP (ping)
A. Heartbeat Interval
B. Additional Master Hold Up Time
C. Promotion Hold Time
D. Monitor Fall Hold Up Time
-
Question 330:
Which log type will help the engineer verify whether packet buffer protection was activated?
A. Data Filtering
B. Configuration
C. Threat
D. Traffic
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.