Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 51:
An administrator reads through the following Applications and Threats Content Release Notes before an update:
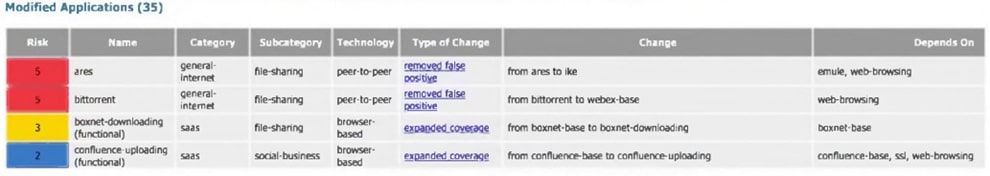
Which rule would continue to allow the file upload to confluence after the update?

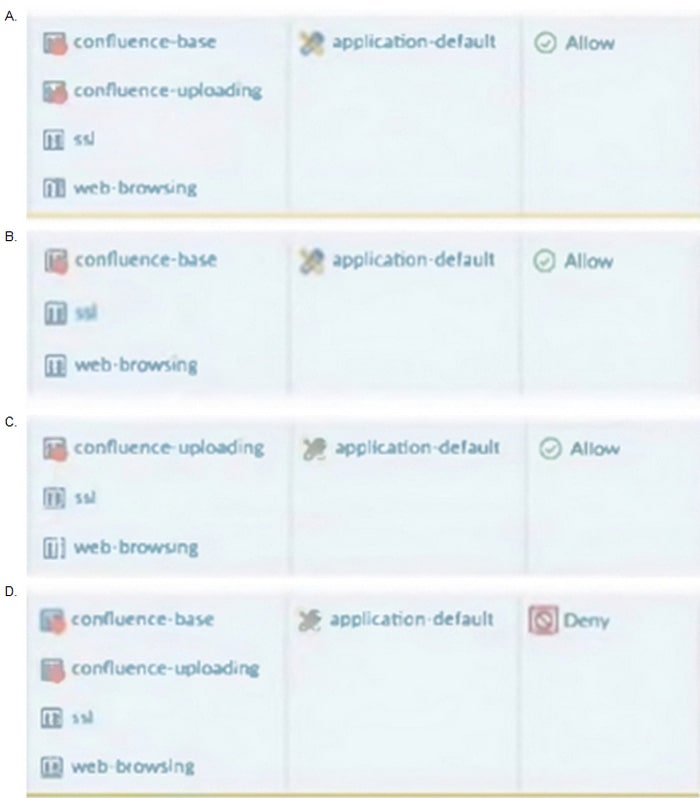
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 52:
An administrator needs to create a Security policy rule that matches DNS traffic sourced from either the LAN or VPN zones, destined for the DMZ or Untrust zones.
The administrator does not want to match traffic where the source and destination zones are LAN, and also does not want to match traffic where the source and destination zones are VPN.
Which Security policy rule type should they use?
A. Interzone
B. Universal
C. Intrazone
D. Default
-
Question 53:
Which Security profile prevents users from submitting valid corporate credentials online?
A. WildFire
B. URL filtering
C. Advanced threat prevention
D. SSL decryption
-
Question 54:
The NetSec Manager asked to create a new firewall Local Administrator profile with customized privileges named New_Admin. This new administrator has to authenticate without inserting any username or password to access the WebUI. What steps should the administrator follow to create the New_Admin Administrator profile?
A. 1. Set the Authentication profile to Local.
2.
Select the "Use only client certificate authentication" check box.
3.
Set Role to Role Based.
B. 1. Select the "Use only client certificate authentication" check box.
2.
Set Role to Dynamic.
3.
Issue to the Client a Certificate with Certificate Name = New Admin
C. 1. Select the "Use only client certificate authentication" check box.
2.
Set Role to Dynamic.
3.
Issue to the Client a Certificate with Common Name = New_Admin
D.
1. Select the "Use only client certificate authentication" check box.
2. Set Role to Role Based.
3.
Issue to the Client a Certificate with Common Name = New Admin
-
Question 55:
An administrator receives a notification about new malware that is being used to attack hosts. The malware exploits a software bug in a common application. Which Security Profile will detect and block access to this threat after the administrator updates the firewall's threat signature database?
A. Vulnerability Profile applied to inbound Security policy rules
B. Antivirus Profile applied to outbound Security policy rules
C. Data Filtering Profile applied to outbound Security policy rules
D. Data Filtering Profile applied to inbound Security policy rules
-
Question 56:
What are three DNS policy actions? (Choose three.)
A. Block
B. Allow
C. Strict
D. Sinkhole
E. Alert
-
Question 57:
Which System log severity level would be displayed as a result of a user password change?
A. Low
B. Medium
C. High
D. Critical
-
Question 58:
An administrator would like to block traffic to all high risk audio streaming applications, including new App-IDs introduced with content updates. Which filter should the administrator configure in the application filter object?
A. The category is media, and the characteristic includes Evasive.
B. The subcategory is audio-streaming, and the risk is 1.
C. The subcategory is audio-streaming, and the risk is 5.
D. The category is media, and the tag is high risk.
-
Question 59:
Given the detailed log information above, what was the result of the firewall traffic inspection?
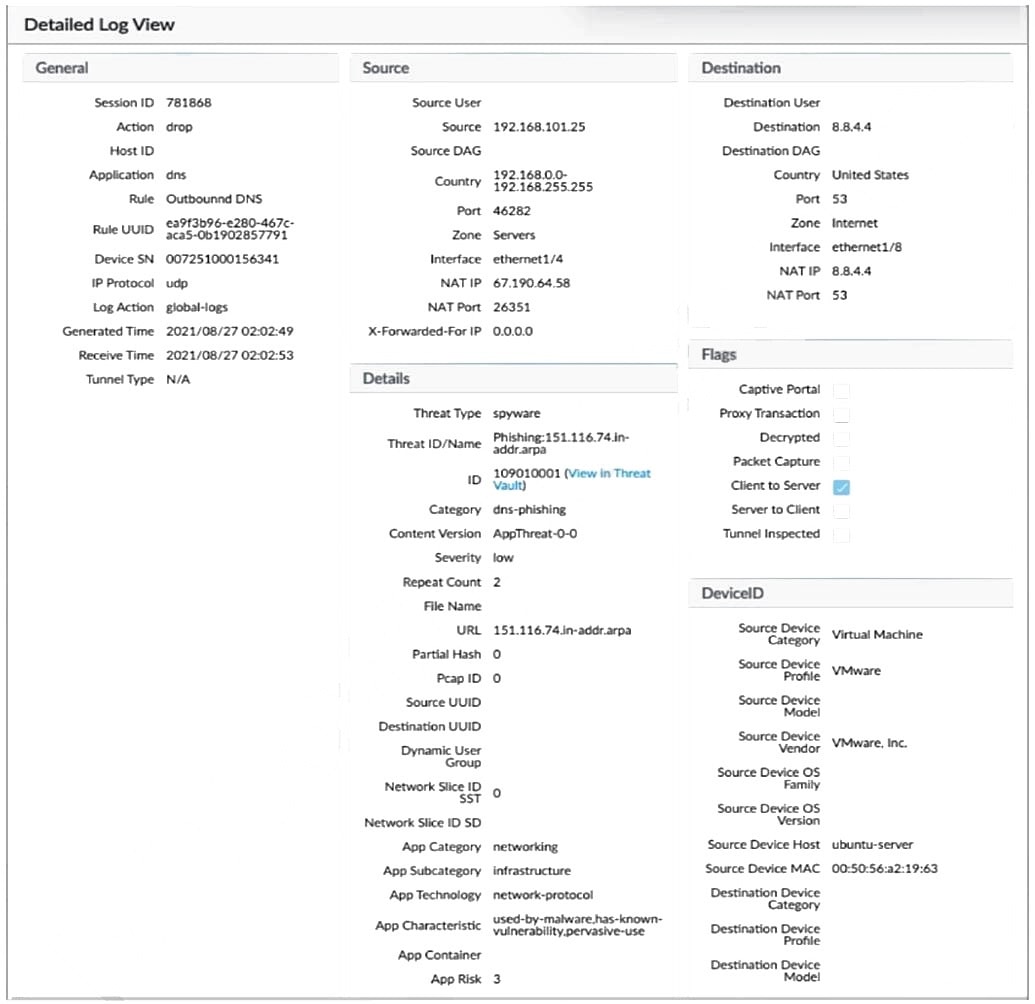
A. It denied the category DNS phishing.
B. It denied the traffic because of unauthorized attempts.
C. It was blocked by the Anti-Virus Security profile action.
D. It was blocked by the Anti-Spyware Profile action.
-
Question 60:
Which interface types are assigned to IEEE 802.1Q VLANs?
A. Tunnel interfaces
B. Layer 2 subinterfaces
C. Layer 3 subinterfaces
D. Loopback interfaces
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.