Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 351:
An administrator would like to block access to a web server, while also preserving resources and minimizing half-open sockets. What are two security policy actions the administrator can select? (Choose two.)
A. Reset server
B. Reset both
C. Drop
D. Deny
-
Question 352:
Which interface does not require a MAC or IP address?
A. Virtual Wire
B. Layer3
C. Layer2
D. Loopback
-
Question 353:
Which prevention technique will prevent attacks based on packet count?
A. zone protection profile
B. URL filtering profile
C. antivirus profile
D. vulnerability profile
-
Question 354:
Which statement is true about Panorama managed devices?
A. Panorama automatically removes local configuration locks after a commit from Panorama
B. Local configuration locks prohibit Security policy changes for a Panorama managed device
C. Security policy rules configured on local firewalls always take precedence
D. Local configuration locks can be manually unlocked from Panorama
-
Question 355:
Which administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact and command-and-control (C2) server. Which security profile components will detect and prevent this threat after the firewall`s signature database has been updated?
A. antivirus profile applied to outbound security policies
B. data filtering profile applied to inbound security policies
C. data filtering profile applied to outbound security policies
D. vulnerability profile applied to inbound security policies
-
Question 356:
An administrator would like to create a URL Filtering log entry when users browse to any gambling website. What combination of Security policy and Security profile actions is correct?
A. Security policy = drop, Gambling category in URL profile = allow
B. Security policy = deny. Gambling category in URL profile = block
C. Security policy = allow, Gambling category in URL profile = alert
D. Security policy = allow. Gambling category in URL profile = allow
-
Question 357:
Which three statement describe the operation of Security Policy rules or Security Profiles? (Choose three)
A. Security policy rules inspect but do not block traffic.
B. Security Profile should be used only on allowed traffic.
C. Security Profile are attached to security policy rules.
D. Security Policy rules are attached to Security Profiles.
E. Security Policy rules can block or allow traffic.
-
Question 358:
Which plane on a Palo Alto Networks Firewall provides configuration, logging, and reporting functions on a separate processor?
A. data
B. network processing
C. management
D. security processing
-
Question 359:
An administrator is investigating a log entry for a session that is allowed and has the end reason of aged-out. Which two fields could help in determining if this is normal? (Choose two.)
A. Packets sent/received
B. IP Protocol
C. Action
D. Decrypted
-
Question 360:
Based on the screenshot presented which column contains the link that when clicked opens a window to display all applications matched to the policy rule?
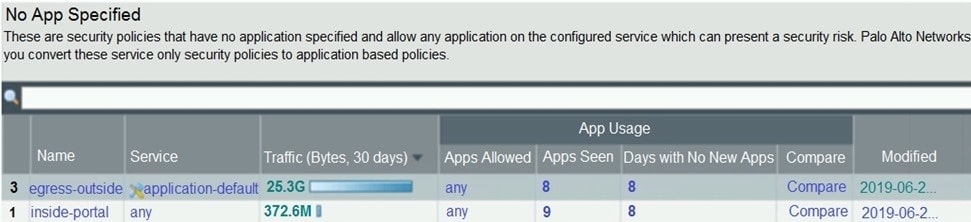
A. Apps Allowed
B. Name
C. Apps Seen
D. Service
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.