Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 321:
An administrator would like to reference the same address object in Security policies on 100 Panorama managed firewalls, across 10 devices groups and five templates.
Which configuration action should the administrator take when creating the address object?
A. Ensure that Disable Override is cleared.
B. Ensure that the Shared option is cleared.
C. Ensure that the Shared option is checked.
D. Tag the address object with the Global tag.
-
Question 322:
Which list of actions properly defines the order of steps needed to add a local database user account and create a new group to which this user will be assigned?
A. 1. Navigate to Device > Local User Database > Users and click Add.
2.
Enter a Name for the user.
3.
Enter and Confirm a Password or Hash.
4.
Enable the account and click OK.
5.
Navigate to Device > Local User Database > User Groups and click Add.
6.
Enter a Name for the group.
7.
Add the user to the group and click OK.
B. 1. Navigate to Device > Authentication Profile > Users and click Add.
2.
Enter a Name for the user.
3.
Enter and Confirm a Password or Hash.
4.
Enable the account and click OK.
5.
Navigate to Device > Local User Database > User Groups and click Add.
6.
Enter a Name for the group.
7.
Add the user to the group and click OK.
C. 1. Navigate to Device > Users and click Add.
2.
Enter a Name for the user.
3.
Enter and Confirm a Password or Hash.
4.
Enable the account and click OK.
5.
Navigate to Device > User Groups and click Add.
6.
Enter a Name for the group.
7.
Add the user to the group and click OK.
D. 1. Navigate to Device > Admins and click Add.
2.
Enter a Name for the user.
3.
Enter and Confirm a Password or Hash.
4.
Enable the account and click OK.
5.
Navigate to Device > User Groups and click Add.
6.
Enter a Name for the group.
7.
Add the user to the group and click OK.
-
Question 323:
What are the three DNS Security categories available to control DNS traffic? (Choose three.)
A. Parked Domains
B. Spyware Domains
C. Vulnerability Domains
D. Phishing Domains
E. Malware Domains
-
Question 324:
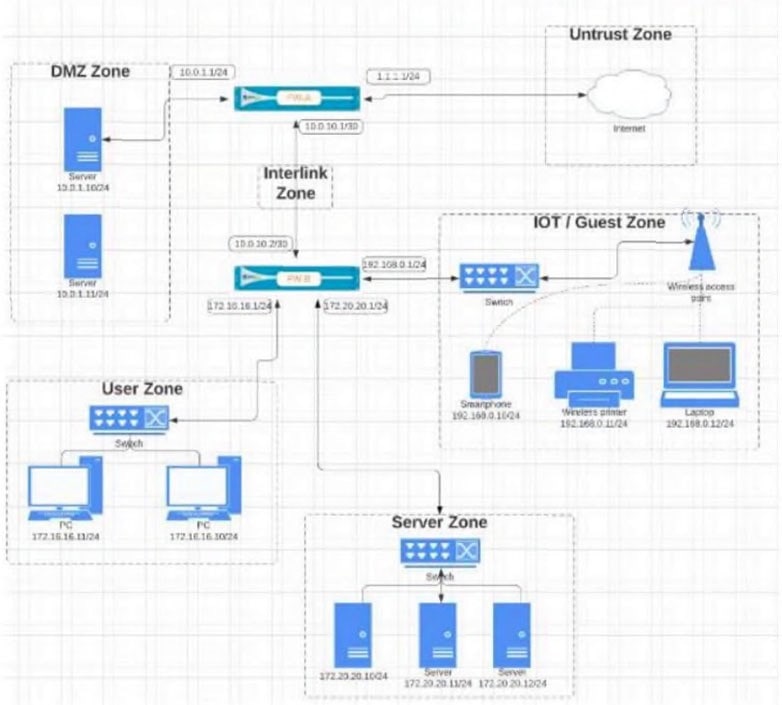
Given the network diagram, traffic must be permitted for SSH and MYSQL from the DMZ to the SERVER zones, crossing two firewalls. In addition, traffic should be permitted from the SERVER zone to the DMZ on SSH only. Which rule group enables the required traffic?
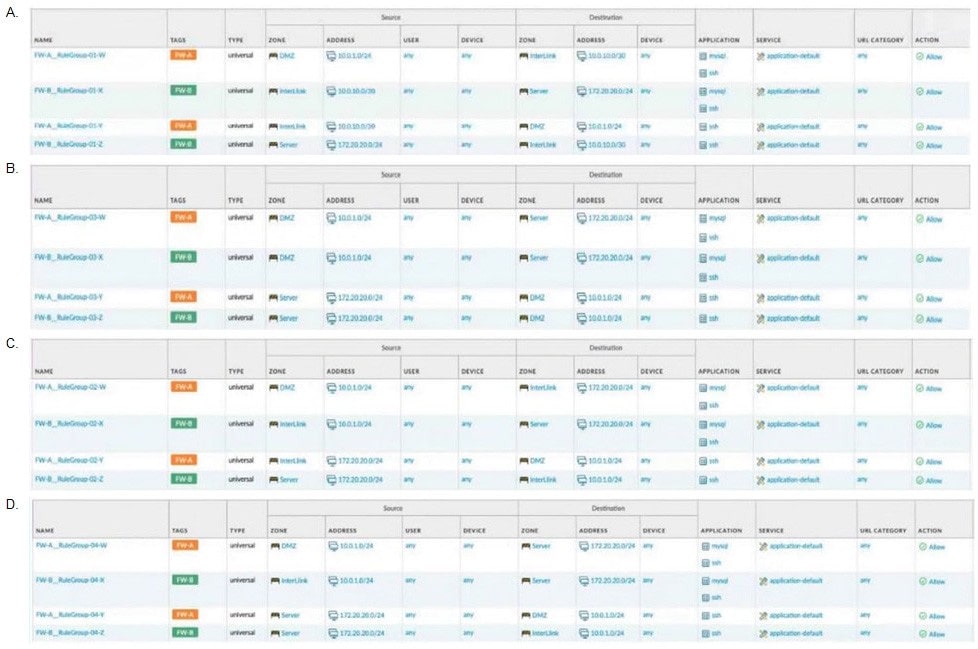
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 325:
An administrator is creating a NAT policy.
Which combination of address and zone are used as match conditions? (Choose two.)
A. Pre-NAT address
B. Pre-NAT zone
C. Post-NAT address
D. Post-NAT zone
-
Question 326:
An administrator wants to prevent hacking attacks through DNS queries to malicious domains.
Which two DNS policy actions can the administrator choose in the Anti-Spyware Security Profile? (Choose two.)
A. deny
B. block
C. sinkhole
D. override
-
Question 327:
A coworker found a USB labeled "confidential in the parking lot. They inserted the drive and it infected their corporate laptop with unknown malware The malware caused the laptop to begin infiltrating corporate data. Which Security Profile feature could have been used to detect the malware on the laptop?
A. DNS Sinkhole
B. WildFire Analysis
C. Antivirus
D. DoS Protection
-
Question 328:
According to best practices, how frequently should WildFire updates he made to perimeter firewalls?
A. every 10 minutes
B. every minute
C. every 5 minutes
D. in real time
-
Question 329:
Access to which feature requires a URL Filtering license?
A. PAN-DB database
B. External dynamic lists
C. DNS Security
D. Custom URL categories
-
Question 330:
What are two valid selections within a Vulnerability Protection profile? (Choose two.)
A. deny
B. drop
C. default
D. sinkhole
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.