Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 281:
What do application filters help provide access to?
A. Applications that are explicitly sanctioned for use within a company
B. Applications that are not explicitly sanctioned and that a company wants users to be able to access
C. Applications that are explicitly unsanctioned for use within a company
D. Applications that are not explicitly unsanctioned and that a company wants users to be able to access
-
Question 282:
Which three management interface settings must be configured for functional dynamic updates and administrative access on a Palo Alto Networks firewall? (Choose three.)
A. NTP
B. IP address
C. MTU
D. DNS server
E. service routes
-
Question 283:
How does the Policy Optimizer policy view differ from the Security policy view?
A. It provides sorting options that do not affect rule order
B. It specifies applications seen by rules
C. It displays rule utilization
D. It details associated zones
-
Question 284:
An administrator creates a new Security policy rule to allow DNS traffic from the LAN to the DMZ zones. The administrator does not change the rule type from its default value. What type of Security policy rule is created?
A. Intrazone
B. Interzone
C. Universal
D. Tagged
-
Question 285:
An interface can belong to how many Security Zones?
A. 1
B. 2
C. 3
D. 4
-
Question 286:
What are the two types of Administrator accounts? (Choose two.)
A. Role Based
B. Superuser
C. Dynamic
D. Local
-
Question 287:
The Net Sec Manager asked to create a new Firewall Operator profile with customized privileges.
In particular, the new firewall operator should be able to:
Check the configuration with read-only privilege for LDAP, RADIUS, TACACS+, and SAML as Server profiles to be used inside an Authentication profile.
The firewall operator should not be able to access anything else.
What is the right path m order to configure the new firewall Administrator Profile?
A. Device > Admin Roles > Add > Web UI > Device > Server Profiles Device > Admin Roles > Add > Web UI > disable access to everything else
B. Device > Admin Roles > Add > Web UI > Objects > Server Profiles Device > Admin Roles > Add > Web UI > disable access to everything else
C. Device > Admin Roles > Add >Web UI > Objects > Authentication Profile Device > Admin Roles > Add > Web UI > disable access to everything else
D. Device > Admin Roles > Add > Web UI > Device > Authentication Profile Device > Admin Roles > Add > Web UI > disable access to everything else
-
Question 288:
Which policy set should be used to ensure that a policy is applied just before the default security rules?
A. Shared post-rulebase
B. Local firewall policy
C. Parent device-group post-rulebase
D. Child device-group post-rulebase
-
Question 289:
Review the screenshot below. Based on the information it contains, which protocol decoder will detect a machine-learning match, create a Threat log entry, and permit the traffic?
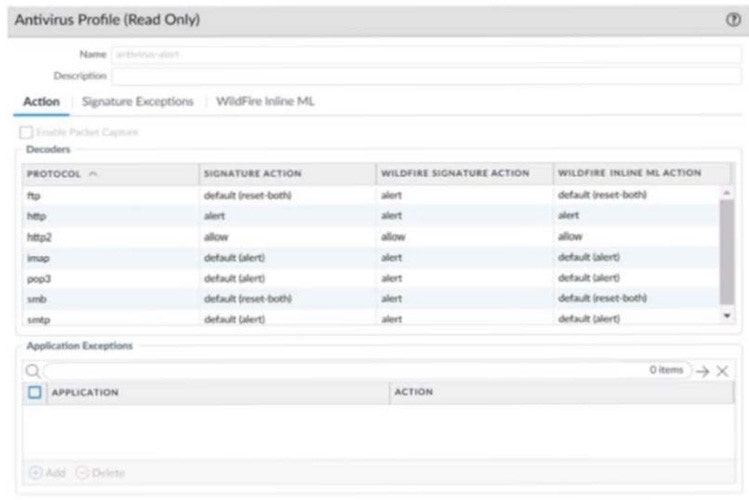
A. smb
B. imap
C. ftp
D. http2
-
Question 290:
If a universal security rule was created for source zones A and B and destination zones A and B, to which traffic would the rule apply?
A. Some traffic between A and B
B. Some traffic within A
C. All traffic within zones A and B
D. Some traffic within B
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.