Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 91:
Application groups enable access to what?
A. Applications that are explicitly unsanctioned for use within a company
B. Applications that are not explicitly unsanctioned and that an administrator wants users to be able to access
C. Applications that are explicitly sanctioned for use within a company
D. Applications that are not explicitly sanctioned and that an administrator wants users to be able to access
-
Question 92:
Where does a user assign a tag group to a policy rule in the policy creation window?
A. General tab
B. Usage tab
C. Application tab
D. Actions tab
-
Question 93:
Which setting is available to edit when a tag is created on the local firewall?
A. Color
B. Location
C. Order
D. Priority
-
Question 94:
With the PAN-OS 11.0 Nova release, which two attack options can new inline deep learning analysis engines detect and prevent? (Choose two.)
A. Command injection attacks
B. SSL attacks
C. SQL injection attacks
D. HTTP attacks
-
Question 95:
Which profile must be applied to the Security policy rule to block spyware on compromised hosts from trying to phone-home or beacon out to external command-and-control (C2) servers?
A. Anti-spyware
B. File blocking
C. WildFire
D. URL filtering
-
Question 96:
Which feature dynamically analyzes and detects malicious content by evaluating various web page details using a series of machine learning (ML) models?
A. Antivirus Inline ML
B. URL Filtering Inline ML
C. Anti-Spyware Inline ML
D. WildFire Inline ML
-
Question 97:
An administrator is troubleshooting an issue with Office365 and expects that this traffic traverses the firewall.
When reviewing Traffic Log entries, there are no logs matching traffic from the test workstation.
What might cause this issue?
A. Office365 traffic is logged in the System Log.
B. Office365 traffic is logged in the Authentication Log.
C. Traffic matches the interzone-default rule, which does not log traffic by default.
D. The firewall is blocking the traffic, and all blocked traffic is in the Threat Log.
-
Question 98:
Which verdict may be assigned to a WildFire sample?
A. Phishing
B. Spyware
C. PUP
D. Malware
-
Question 99:
Given the network diagram, which two statements are true about traffic between the User and Server networks? (Choose two.)
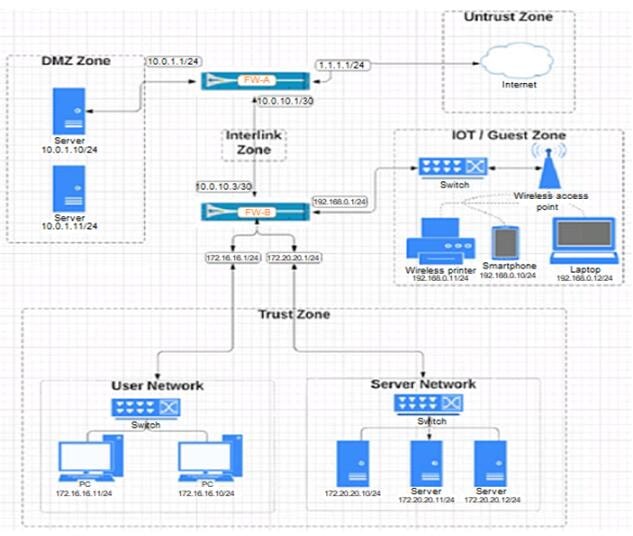
A. Traffic is permitted through the default Intrazone “allow” rule.
B. Traffic restrictions are not possible because the networks are in the same zone.
C. Traffic is permitted through the default Interzone “allow” rule.
D. Traffic restrictions are possible by modifying Intrazone rules.
-
Question 100:
By default, which action is assigned to the intrazone-default rule?
A. Reset-client
B. Reset-server
C. Deny
D. Allow
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.