Exam Details
Exam Code
:NSE8_810Exam Name
:Fortinet Network Security Expert 8 Written Exam (810)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:60 Q&AsLast Updated
:Aug 09, 2025
Fortinet Fortinet Certifications NSE8_810 Questions & Answers
-
Question 41:
Exhibit
Click the Exhibit button.
You have deployed several perimeter FortiGates with internal segmentation FortiGates behind them. All FortiGate devices are logging to FortiAnalyzer. When you search the logs in FortiAnalyzer for denied traffic, you see numerous log messages, as shown in the exhibit, on your perimeter FortiGates only.
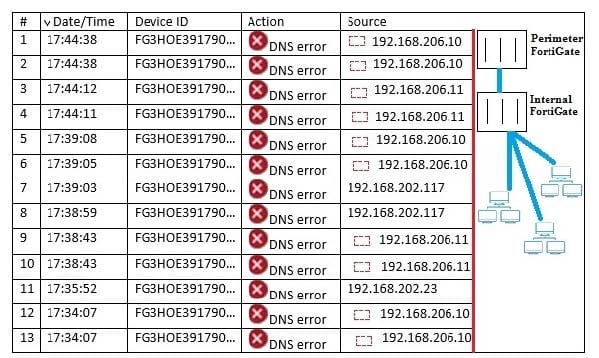
Which two actions would reduce the number of these log messages? (Choose two.)
A. Apply an application control profile lo the perimeter FortiGates that does not inspect DNS traffic to the outbound firewall policy.
B. Configure the internal ForbGates to communicate to ForpGuard using port 8888.
C. Disable DNS events logging horn ForirGate In the config log fortianalyser filter section.
D. Remove DNS signature*
-
Question 42:
Click the Exhibit button.
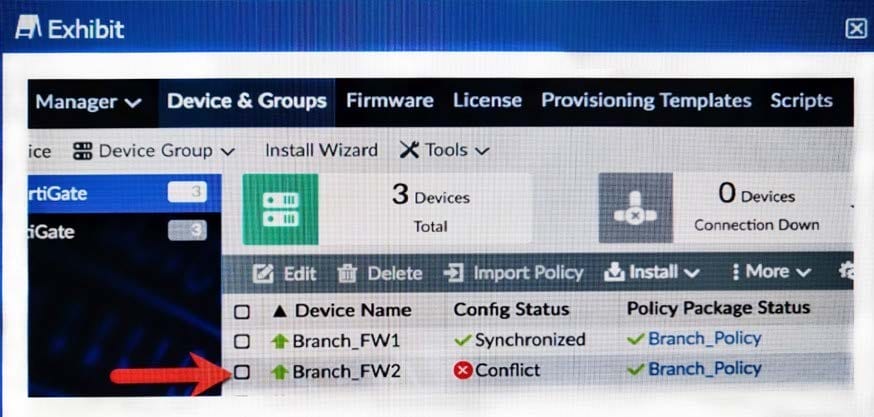
You log into FortiManager, look at the Device Manager window and notice that one of your managed devices is not in normal status.
Referring to the exhibit, which two statements correctly describe the affected device's status and result? (Choose two.)
A. The device configuration was changed on the local FoitiGate side only. auto-update is disabled.
B. The device configuration was changed on both the local FortiGate side and the FortiManager side, auto-update is disabled.
C. The changed configuration on the FortiGate wrt remain the next time that the device configuration is pushed from ForbManager.
D. The changed configuration on the FortiGate will be overwritten in favor of what is on the FortiMAnager the next time that the device configuration is pushed.
-
Question 43:
Click the Exhibit button.
The exhibit shows a full-mesh topology between FortiGates and FortiSwitches. To deploy this
configuration, two requirements must be met:
-20 Gbps full duplex connectivity is available between each FortiGate and the FortiSwitches
-The FortiGate HA must be in AP mode.
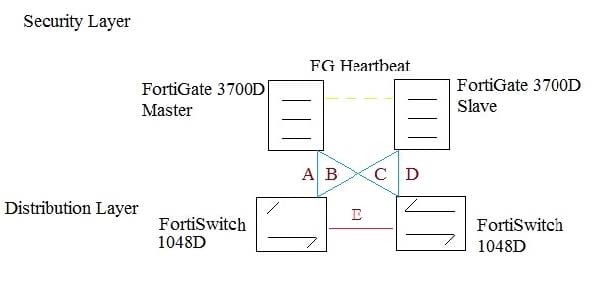
Referring to the exhibit, what are two actions that will fulfill the requirements? (Choose two.)
A. Configure both FortiSwitch as pears with ICL over cable E, create one MCLAG on ports connected to cables A and C, and create another MCLAG on ports connected to cables B and D.
B. Configure the master FortiGate with one and FortiLink split interface disable on ports connected to cables A and C and make sure the same ports are used for to cables B and D.
C. Configure both FortiSwitches as peers ISL over cable on create one MCLAG on ports connected cables A and C, and ceate another MCLAG on ports connected to cables B and D.
D. Configure the master FortiGate with one LAG and FortiLink split interface enables on ports connected to cable A and C make sure the ports are used for cables B and D on the slave.
-
Question 44:
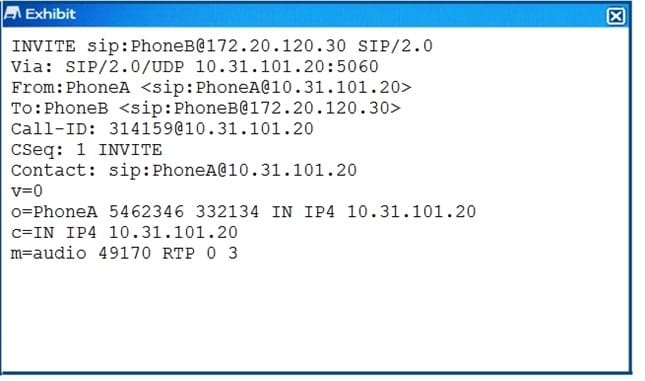
Click the Exhibit button.
A FortiGate with the default configuration is deployed between two IP phones. FortiGate receives the INVITE request shown in the exhibit form Phone A (internal)to Phone B (external). Which two actions are taken by the FortiGate after the packet is received? (Choose two.)
A. A pinhole will be opened to accept traffic sent to FortiGate's WAN IP address and ports 49169 and 49170.
B. a pinhole will be opened to accept traffic sent to FortiGate's WAN IP address and ports 49l70 and 49171.
C. The phone A IP address will be translated lo the WAN IP address in all INVITE header fields and the m: field of the SDP statement.
D. The phone A IP address will be translated for the WAN IP address in all INVITE header fields and the SDP statement remains intact.
-
Question 45:
Your client wants to use a central RADIUS server for management authentication when connecting to the FortiGate GUL and provide different levels of access for different types of employees.
Which three actions required providing the requested functionality? (Choose three.)
A. Enable radius-vdom-override in the CLI.
B. Create a wildcard administrator on the FortGate
C. Enable occprofile-override in the CLI.
D. Set the RADIUS authencation type to MS-CHApV2.
E. Create multiple administrator profiles with matching RADIUS VSAs.
-
Question 46:
Click the Exhibit button.
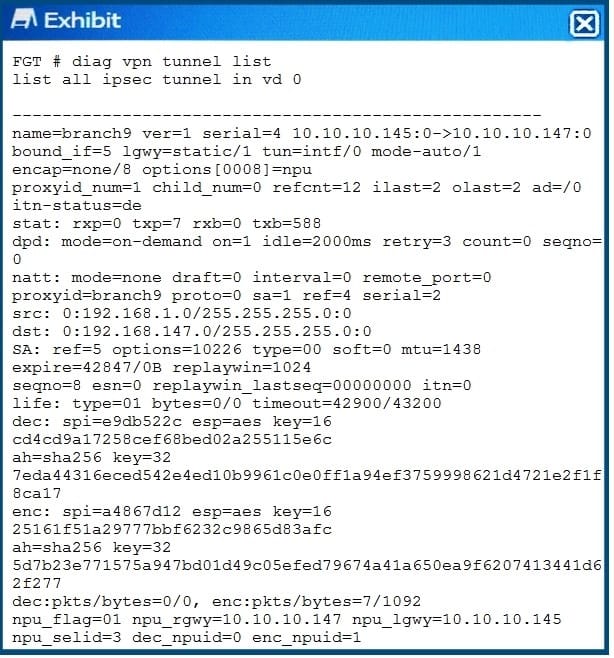
You configured an IPsec tunnel to a branch office. Now you want to make sure that the encryption of the tunnel is offloaded to hardware. Referring to the exhibit, which statement is true?
A. Incoming and outgoing traffic is offloaded
B. Outgoing traffic is offloaded, you cannot determine if incoming traffic is offloaded at this time.
C. Traffic is not offloaded.
D. Outgoing traffic is offloaded: incoming traffic not offloaded.
-
Question 47:
Exhibit Click the Exhibit button. You are trying to configure Link-Aggregation Group (LAG), but ports A and B do not appear on the list of
member options. Referring to the exhibit, which statement is correct in this situation?

A. The FortiGate model being used does not support LAG.
B. The FortiGate model does not have an Integrated Switch Fabric (ISF).
C. The FortiGate SFP+ slot does not have the correct module.
D. The FortiGate interfaces are defective and require replacement.
-
Question 48:
Exhibit
Click the Exhibit button.
The exhibit shows the configuration of a service protection profile (SPP) in a FortiDDoS device.
Which two statements are true about the traffic matching being inspected by this SPP? (Choose two.)
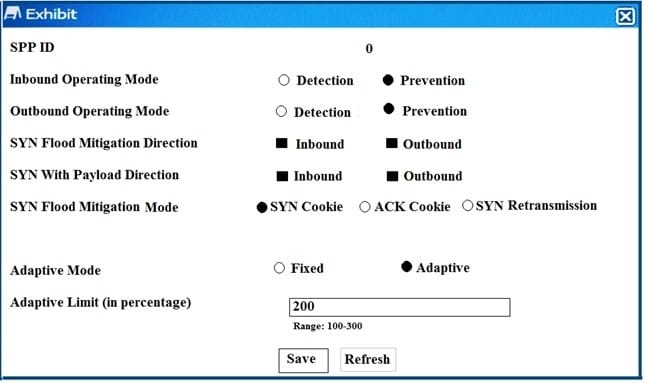
A. Traffic that does match any spp policy will not be inspection by this spp.
B. FortiDDos will not send a SYNACK if a SYN packet is coming from an IP address that is not the legtimate IP (LIP) address table.
C. FortiDooS will start dropping packets as soon as the traffic executed the configured maintain threshold.
D. SYN packets with payloads will be drooped.
-
Question 49:
You deploy a FortiGate device in a remote office based on the requirements shown below.
-- Due to company's security policy, management IP of your FortiGate is not allowed to access the Internet.
-- Apply Web Filtering, Antivirus, IPS and Application control to the protected subnet. -- Be managed by a
central FortiManager in the head office.
Which action will help to achieve the requirements?
A. Configure a default route and make sure that the FortiGate device can pmg to service fortiguard net.
B. Configure the FortiGuard override server and use the IP address of the FortiManager
C. Configure the FortiGuard override server and use the IP address of service, fortiguard net.
D. Configure FortiGate to use FortiGuard Filtering Port 8888.
-
Question 50:
Click the Exhibit button.
config system ha
set mode a-a
set group-id 1
set group-name main
set hb_dev port2 100
set session-pickup enable
end
You have configured an HA cluster with two FortiGates. You want to make sure that you are able to
manage the individual cluster members directly using port3.
Referring to the exhibit, what are two ways to accomplish this task? (Choose two.)
A. Disable the sync feature on porl3: then configure specific IPs for ports on both cluster members.
B. Configure port3 to be a dedicated HA management interface, then configure specific IPs for port3 on both cluster members.
C. Create a management VDOM and Disable the HA synchronization for this VDOM, assign ports to this VDOM, then configure specific IPs for ports on both cluster member.
D. Allow administrative access in the HA heartbeat interfaces.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE8_810 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.