Exam Details
Exam Code
:NSE8_810Exam Name
:Fortinet Network Security Expert 8 Written Exam (810)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:60 Q&AsLast Updated
:Aug 09, 2025
Fortinet Fortinet Certifications NSE8_810 Questions & Answers
-
Question 21:
Exhibit Click the Exhibit button. The exhibit shows the steps for creating a URL rewrite policy on a FortiWeb. Which statement represents the purpose of this policy?
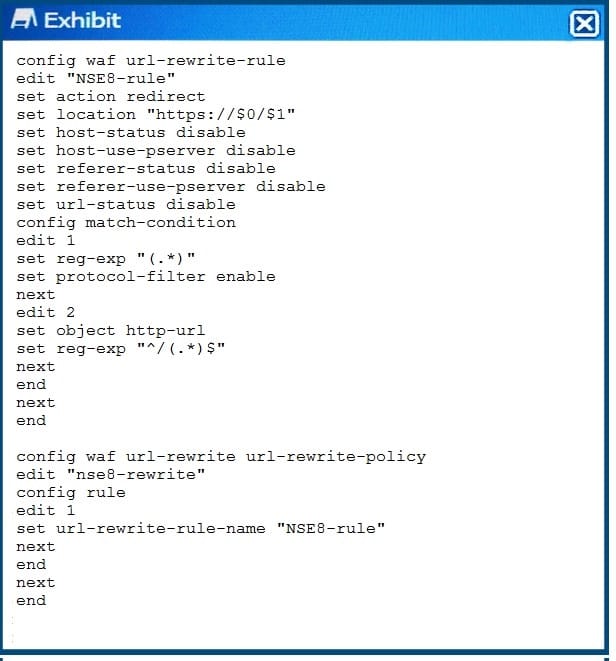
A. The policy redirects all HTTP URLs to HTTPS.
B. The policy redirects all HTTPS URLs to HTTP.
C. The policy redirects only HTTPS URLs containing the ^/ (. *) S string to HTTP.
D. The pokey redirects only HTTP URLs containing the^/ ( .*)S string to HTTPS.
-
Question 22:
You are asked to add a FortiDDoS to the network to combat detected slow connection attacks such as Slowloris.
Which prevention mode on FortiDDoS will protect you against this specific type of attack?
A. aggressive aging mode
B. rate limiting mode
C. blocking mode
D. asymmetric mode
-
Question 23:
Exhibit
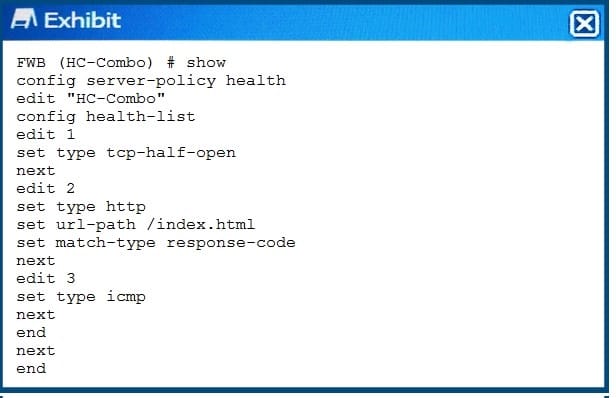
You created a custom health-check for your FortiWeb deployment.
Referring to the output shown in the exhibit, which statement is true?
A. The FortiWeb must receive an RST packet from the server.
B. The FortiWeb must receive an HTTP 200 response code from the server.
C. The FortiWeb must receive an ICMP Echo Request from the server.
D. The FortiWeb must match the hash value of the page index html.
-
Question 24:
A customer wants to enable SYN Rood mitigation in a FortiDDoS device. The FortiDDoS must reply with
one SYN/ACK packet per SYN packet ftom a new source IP address.
Which SYN packet from a new source IP address.
Which SYN flood mitigation mode must the customer use?
A. SYN cookie
B. SYN/ACK cookie
C. ACK cookie
D. SYN retransmission
-
Question 25:
A FortOS devices is used for termination of VPNs for number of remote spoke VPN units (designated group A spokes) using a phase 1 main mode dial-up tunnel using pre-shared. Your company recently acquired another organization. You are asked establish VPN correctively for the newly acquired organization's sites which new devices will be provisioned (designated Group B spokes). Both exiting (Group A) and new (Group B) spoke units are dynamically addressed. You are asked to ensure that spokes from the acquired organization (Group B) have different access permission than your
existing VPN spokes (Group A).
Which two solutions meet the represents for the new spoke group? (Choose two.)
A. implements a new phase 1 dial-up mode tunnel with preshared keys and XAuth. Use identity to filter traffic.
B. Implement a new phase 1 dial-up main mode tunnel with a different pre-shared key than the Group A spokes. Use standard policies to filter for the new dial-up tunnel
C. Implement a new phase 1 dial-up main mode tunnel with certificate authentication. Use standard policies to filter for the dial-up tunnel.
D. Implement separate phase 1 dial-up aggressive mode tunnels with a distinct peer ID. Use standard policies to filter traffic for the new dial-up tunnel.
-
Question 26:
You configure an outgoing firewall policy with a web filter for accessing the internet. The access to URL https// itacm.co and web belonging to the same category should be blocked. You notice that the Web server presents a certificate with CN=www acme.com. The www.it.acme site is as '' information Technology and the www.acme.com site is categorized as ''Business".
Which statements is correct in this scenario?
A. Category "information Technology" needs to blocked, the FortiGate is able to inspection the URL with HTTPS sessions.
B. Category "Business" need a to be block: the certificate name takes precedence over the SNI.
C. SSL inspection must be configured to deep-inspection: the category "information Technology "needs to be blocked.
D. Category :information Technology" needs to be blocked, the SNI takes precedence over the certificate name.
-
Question 27:
Click the Exhibit button.
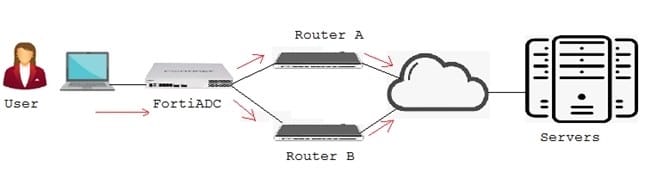
Referring to the exhibit, a FortiADC is load balancing IPv4 traffic between two next-hop routers. The FortiADC does not know the IP addresses of the servers. Also, the FortiADC is doing Layer 7 content inspection and modification.
In this scenario, which application delivery control is configured in the FortiADC?
A. Layer 2
B. Layer 3
C. Laye.4
D. Layer 7
-
Question 28:
A company has just deployed a new FortiMail in gateway mode. The administrator is asked to strengthen e-mail protection by applying the policies shown below.
- E-mails can only be accepted if a valid e-mail account exists.
-
Only authenticated users can send e-mails out
Which two actions will satisfy the requirements? (Choose two. )
A.
Configure recipient address verification.
B.
Configure inbound recipient policies.
C.
Configure outbound recipient policies.
D.
Configure access control rules.
-
Question 29:
Click the exhibit button.
A FortiGate device is configured to authenticate SSL VPN users using digital certificates. Part of the
FortiGate configuration is shown in the exhibit.
Which two statements are true in this scenario? (Choose two.)
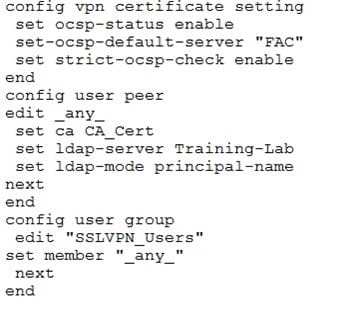
A. The authentication will fail if the OCSP server is down.
B. OCSP is used to verify that the user-signed certificate has not expired.
C. The authentication will fail if the certificate does not contain user principle name (UPN) information.
D. The authentication will fail if the user certificate does not contain the CA_Cert string in the Failed.
-
Question 30:
FortiMail configured with the protected domain "internal lab".
Which two envelopes addresses will need an access control rule to relay e-mail sent for unauthenticated users? (Choose two.)
A. MAIL FROM: traming@fortinet com: RCPT TO: student@fortmet com
B. MAIL FROM student@fortinet com: RCPT TO [email protected]
C. MAIL FROM: trainmg@internallab; RCPT TO student@mternallab
D. MAIL FROM student@internal lab: RCPT TO [email protected]
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE8_810 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.