Exam Details
Exam Code
:NSE7_ATP-2.5Exam Name
:Fortinet NSE 7 - Advanced Threat Protection 2.5Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:30 Q&AsLast Updated
:Jul 03, 2025
Fortinet Fortinet Certifications NSE7_ATP-2.5 Questions & Answers
-
Question 11:
Which threats can FortiSandbox inspect when it is deployed in sniffer mode? (Choose three.)
A. Spam emails
B. Known malware
C. Encrypted files
D. Malicious URLs
E. Botnet connections
-
Question 12:
Which FortiSandbox diagnostic command should you use to diagnose Internet connectivity issues on port3?
A. ping
B. tcpdump
C. test-network
D. traceroute
-
Question 13:
What information does a scan job report include? (Choose two.)
A. Updates to the antivirus database
B. Summary of the file activity
C. Details about system files deleted of modified
D. Changes to the FortiSandbox configuration
-
Question 14:
Examine the CLI configuration, than answer the following question:
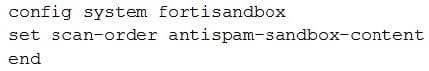
Which of the following statements is true regarding this FortiMail's inspection behavior?
A. Malicious URLs will be removed by antispam and replaced with a message.
B. Suspicious files not detected by antivirus will be inspected by FortiSandbox.
C. Known malicious URLs will be inspected by FortiSandbox.
D. Files are skipped by content profile will be inspected by FortiSandbox.
-
Question 15:
What advantage does sandboxing provide over traditional virus detection methods?
A. Heuristics detection that can detect new variants of existing viruses.
B. Pattern-based detection that can catch multiple variants of a virus.
C. Full code execution in an isolated and protected environment.
D. Code emulation as packets are handled in real-time.
-
Question 16:
Examine the FortiClient configuration shown in the exhibit. then answer the following question:
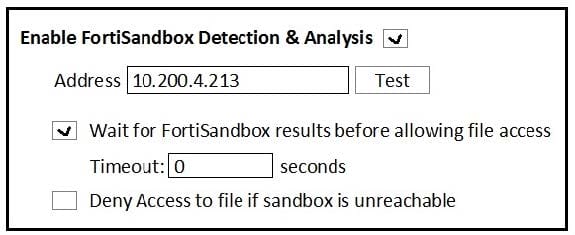
What is the general rule you should follow when configuring the Timeout value for files submitted to FortiSandbox?
A. It should be long enough for FortiSandbox to complete an antivirus scan of files.
B. It should be long enough for FortiSandbox to complete a cloud query of file hashes.
C. It should be long enough for FortiSandbox to complete sandbox analysis of files.
D. It should be long enough for FortiSandbox to complete a static analysis of files.
-
Question 17:
Which of the following scan job report sections are generated by static analysis? (Choose two.)
A. Office Behaviors
B. Launched Processes
C. Registry Changes
D. Virtual Simulator
-
Question 18:
When using FortiSandbox in sniffer-mode, you should configure FortiSandbox to inspect both inbound and outbound traffic.
What type of threats can FortiSandbox detect on inbound traffic? (Choose two.)
A. Botnet connections
B. Malware
C. Malicious URLs
D. Intrusion attempts
-
Question 19:
Which of the advanced threat protection solutions should you use to protect against an attacker may take during the lateral movement stage of the kill chain? (Choose two.)
A. FortiClient and FortiSandbox
B. FortiMail and FortiSandbox
C. FortiGate and FortiSandbox
D. FortiWeb and FortiSandbox
-
Question 20:
Examine the Suspicious Indicators section of the scan job shown in the exhibit, then answer the following question:

Which FortiSandbox component identified the vulnerability exploits?
A. VM scan
B. Antivirus scan
C. Static analysis
D. Cache check
Related Exams:
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4NSE4_FGT-7.0
Fortinet NSE 4 - FortiOS 7.0NSE4_FGT-7.2
Fortinet NSE 4 - FortiOS 7.2
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_ATP-2.5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.