NSE7_ATP-2.5 Exam Details
-
Exam Code
:NSE7_ATP-2.5 -
Exam Name
:Fortinet NSE 7 - Advanced Threat Protection 2.5 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:30 Q&As -
Last Updated
:Jan 12, 2026
Fortinet NSE7_ATP-2.5 Online Questions & Answers
-
Question 1:
Which of the following are FortiWeb's roles when integrated with FortiSandbox? (Choose two.)
A. Share threat information
B. Prevent outbreaks
C. Generate a verdict
D. Block known threats -
Question 2:
Examine the FortiSandbox configuration on FortiMail shown in the exhibit, then answer the following question:
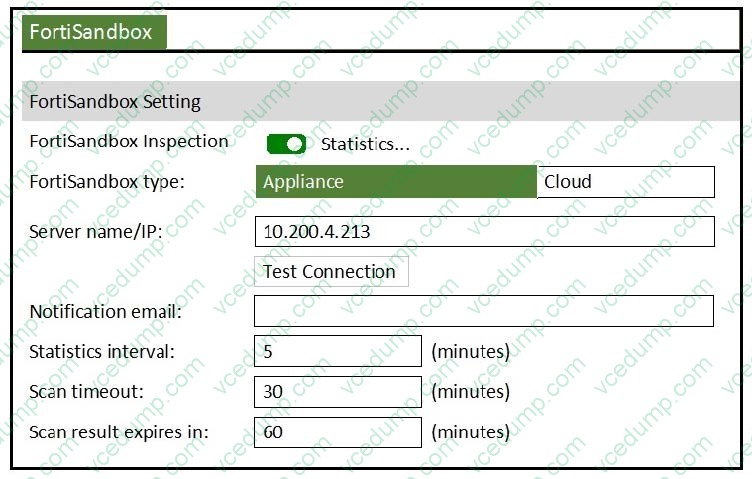
What does the Scan result expires in value specify?
A. How often the local scam results cache will expire on FortiMail.
B. How long FortiMail will wait to send a file or URI to FortiSandbox.
C. How long FortiMail will wait for a scan result from FortiSandbox.
D. How long FortiMail will query FortiSandbox for a scan result. -
Question 3:
Examine the following topology shown in the exhibit, then answer the following question:
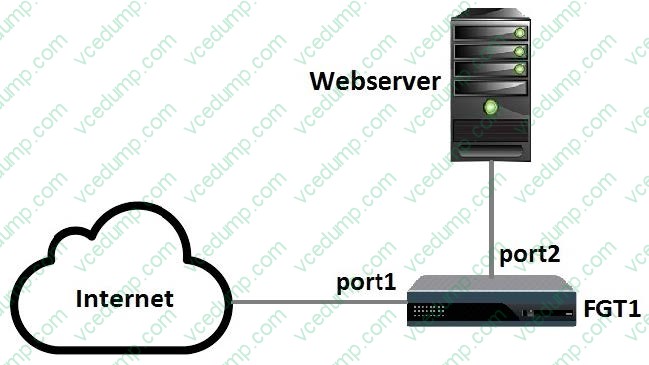
Which of the following configuration tasks are applicable to secure Webserver from known threats? (Choose two.)
A. Apply an SSL inspection profile configured for protecting SSL server.
B. Apply an antivirus profile to the port1 -> port2 firewall policy.
C. Apply an SSL inspection profile configured for full SSL inspection.
D. Apply a web filter profile to the port1 -> port2 firewall policy. -
Question 4:
Examine the scan job report shown in the exhibit, then answer the following question: Which of the following statements are true regarding this verdict? (Choose two.)
A. The file contained malicious JavaScipt.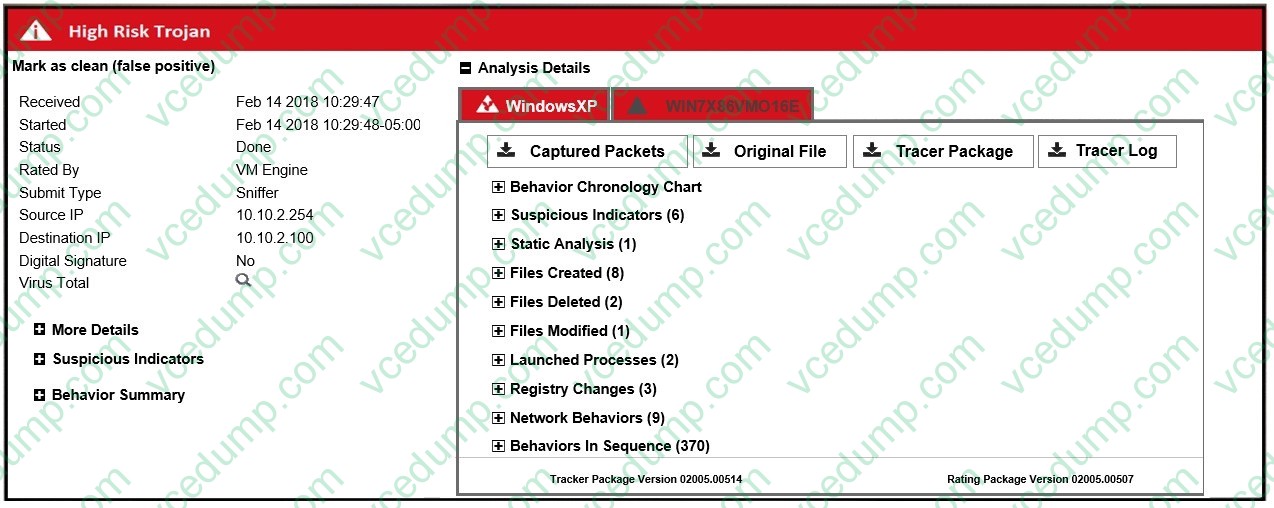
B. The file contained a malicious macro.
C. The file was sandboxed in two-guest VMs.
D. The file was extracted using sniffer-mode inspection. -
Question 5:
Examine the virtual Simulator section of the scan job report shown in the exhibit, then answer the following question:
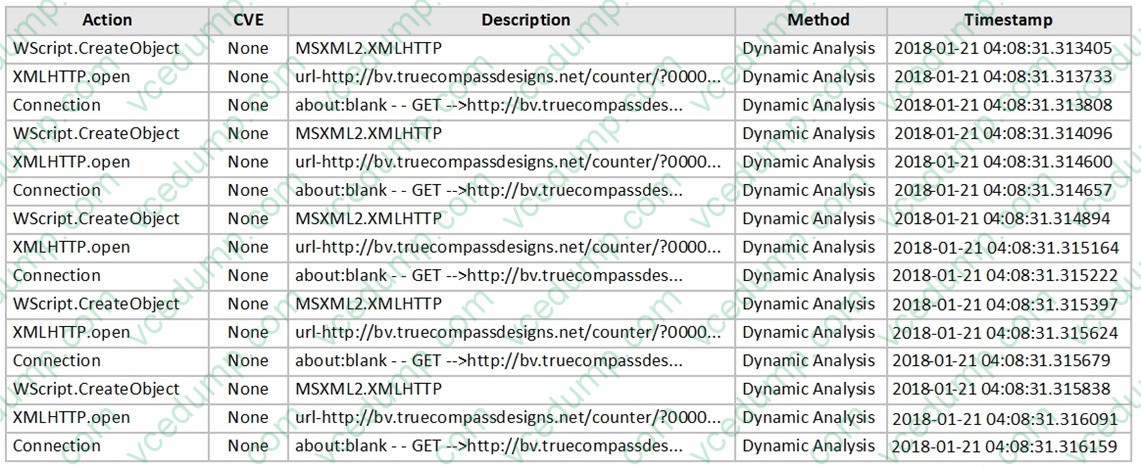
Based on the behavior observed by the virtual simulator, which of the following statements is the most likely scenario?
A. The file contained a malicious image file.
B. The file contained malicious JavaScript.
C. The file contained a malicious macro.
D. The file contained a malicious URL. -
Question 6:
Examine the FortiGate antivirus log detail shown in the exhibit, then answer the following question:
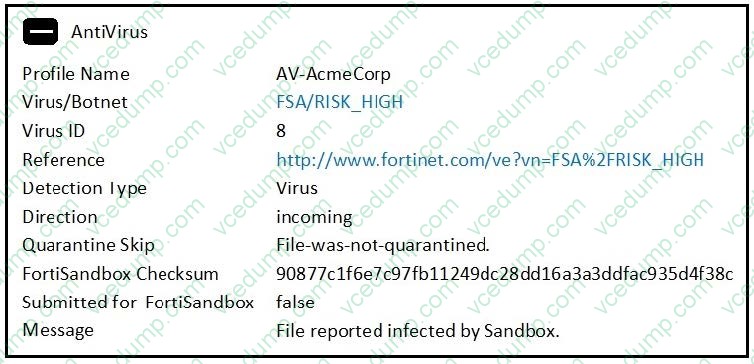
Which of the following statements is true?
A. FortiGate quarantined the file as a malware.
B. The file matched a FortiSandbox-generated malware signature.
C. The file was downloaded from www.fortinet.com.
D. The FSA/RISK_HIGH verdict was generated by FortiSandbox. -
Question 7:
Which of the following actions are performed by FortiSandbox at the static analysis stage?
A. All activity is monitored and recorded while the sample is executed in a virtual environment.
B. The sample's file type is determined and submitted into the appropriate scan job queue.
C. The sample behavior is analyzed and embedded objects are extracted for analysis.
D. Embedded attachments are scanned using the FortiGuard antivirus engine and the latest signature database. -
Question 8:
Which FortiWeb feature supports file submission to FortiSandbox?
A. Attack signature
B. Credential stuffing defense
C. IP reputation
D. File security -
Question 9:
What advantage does sandboxing provide over traditional virus detection methods?
A. Heuristics detection that can detect new variants of existing viruses.
B. Pattern-based detection that can catch multiple variants of a virus.
C. Full code execution in an isolated and protected environment.
D. Code emulation as packets are handled in real-time. -
Question 10:
Examine the CLI configuration, than answer the following question:
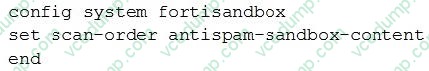
Which of the following statements is true regarding this FortiMail's inspection behavior?
A. Malicious URLs will be removed by antispam and replaced with a message.
B. Suspicious files not detected by antivirus will be inspected by FortiSandbox.
C. Known malicious URLs will be inspected by FortiSandbox.
D. Files are skipped by content profile will be inspected by FortiSandbox.
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_ATP-2.5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.