Exam Details
Exam Code
:NSE6_FML-6.0Exam Name
:Fortinet NSE 6 - FortiMail 6.0Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:30 Q&AsLast Updated
:Aug 08, 2025
Fortinet Fortinet Certifications NSE6_FML-6.0 Questions & Answers
-
Question 11:
Examine the message column of a log cross search result of an inbound email shown in the exhibit; then answer the question below
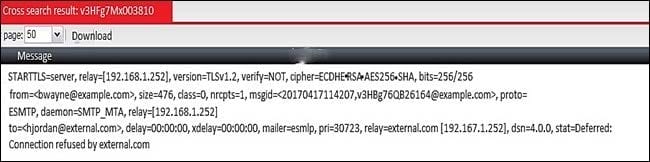
Based on logs, which of the following statements are true? (Choose two.)
A. The FortiMail is experiencing issues delivering the email to the back-end mail server
B. The logs were generated by a server mode FortiMail
C. The logs were generated by a gateway or transparent mode FortiMail
D. The FortiMail is experiencing issues accepting the connection from the remote sender
-
Question 12:
Examine the exhibit; then answer the question below.

MTA 1 is delivering an email intended for User 1 to MTA 2. Which of the following statements about protocol usage between the devices are true? (Choose two.)
A. MTA 2 will use IMAP to receive the email message from MTA 1
B. MTA 1 will use SMTP to deliver the email message to MTA 2
C. User 1 will use IMAP to download the email message from MTA 2
D. MTA 1 will use POP3 to deliver the email message to User 1 directly
-
Question 13:
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to the protected domain for undeliverable email messages. After searching the logs, the administrator identifies that the DSNs were not generated as a result of any outbound email sent from the protected domain. Which FortiMail antispam technique can the administrator use to prevent this scenario? (Choose one.)
A. Bounce address tag validation
B. Spam outbreak protection
C. Spoofed header detection
D. FortiGuard IP Reputation
-
Question 14:
Examine the FortiMail user webmail interface shown in the exhibit; then answer the question below.

Which one of the following statements is true regarding this server mode FortiMail's configuration?
A. The protected domain-level service settings have been modified to allow access to the domain address book
B. This user's account has a customized access profile applied that allows access to the personal address book
C. The administrator has not made any changes to the default address book access privileges
D. The administrator has configured an inbound recipient policy with a customized resource profile
-
Question 15:
Examine the FortiMail IBE service configuration shown in the exhibit; then answer the question below.
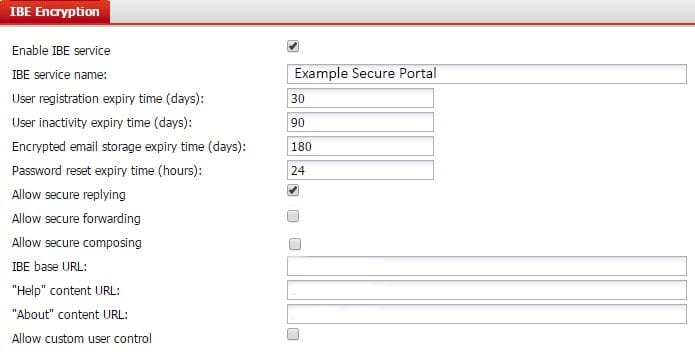
Which of the following statements describes the User inactivity expiry time of 90 days?
A. First time IBE users must register to access their email within 90 days of receiving the notification email message
B. After initial registration, IBE users can access the secure portal without authenticating again for 90 days
C. Registered IBE users have 90 days from the time they receive a notification email message to access their IBE email
D. IBE user accounts will expire after 90 days of inactivity, and must register again to access new IBE email message
-
Question 16:
Examine the configured routes shown in the exhibit; then answer the question below.
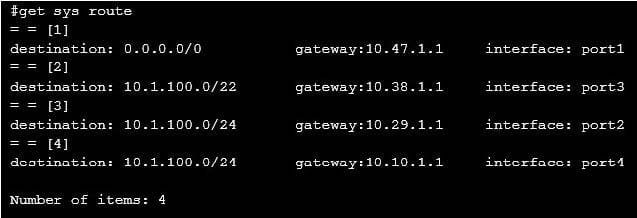
Which interface will FortiMail use to forward an email message destined for 10.1.100.252?
A. port2
B. port4
C. port3
D. port1
-
Question 17:
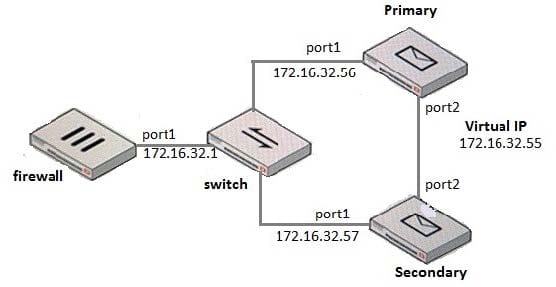
What IP address should the DNS MX record for this deployment resolve to?
A. 172.16.32.1
B. 172.16.32.57
C. 172.16.32.55
D. 172.16.32.56
-
Question 18:
Examine the FortiMail topology and access receive rule shown in the exhibit; then answer the question below.
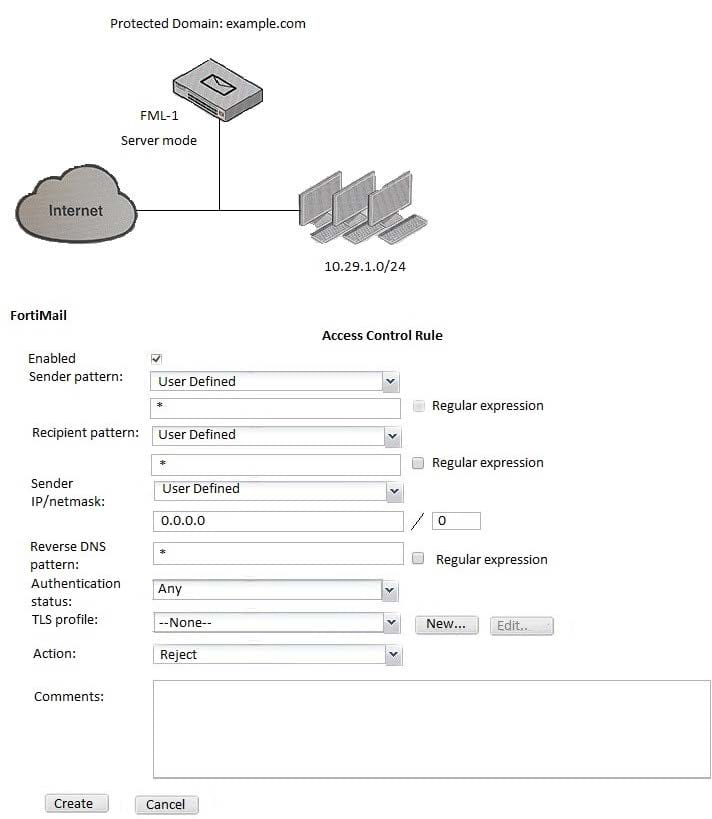
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain. Which of the following settings should be used to configure the access receive rule? (Choose two.)
A. The Sender IP/netmask should be set to 10.29.1.0/24
B. The Authentication status should be set to Authenticated
C. The Recipient pattern should be set o *@example.com
D. The Action should be set to Reject
-
Question 19:
Which of the following statements are true regarding FortiMail's behavior when using the built-in MTA to process email in transparent mode? (Choose two.)
A. FortiMail can queue undeliverable messages and generate DSNs
B. If you disable the built-in MTA, FortiMail will use its transparent proxies to deliver email
C. FortiMail ignores the destination set by the sender and uses its own MX record lookup to deliver email
D. MUAs need to be configured to connect to the built-in MTA to send email
-
Question 20:
Examine the access receive rule shown in the exhibit; then answer the question below.
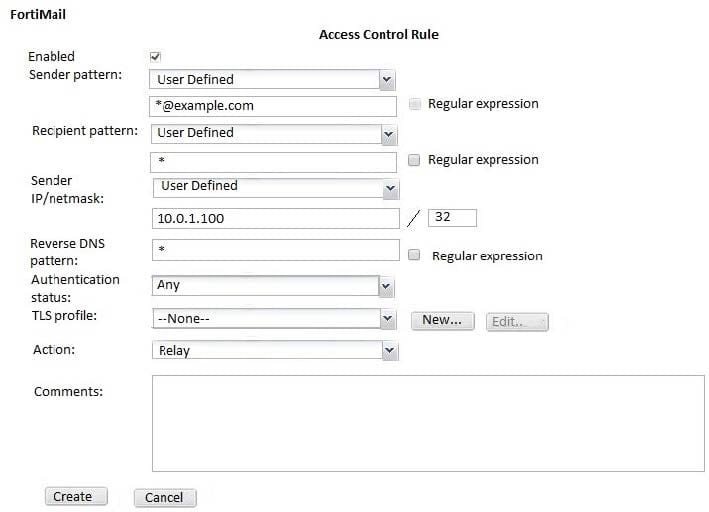
Which of the following statements are true? (Choose two.)
A. Email from any host in the 10.0.1.0/24 subnet can match this rule
B. Senders must be authenticated to match this rule
C. Email matching this rule will be relayed
D. Email must originate from an example.com email address to match this rule
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE6_FML-6.0 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.