NSE6_FML-6.0 Exam Details
-
Exam Code
:NSE6_FML-6.0 -
Exam Name
:Fortinet NSE 6 - FortiMail 6.0 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:30 Q&As -
Last Updated
:Jan 12, 2026
Fortinet NSE6_FML-6.0 Online Questions & Answers
-
Question 1:
While reviewing logs, an administrator discovered that an incoming email was processed using policy IDs: 0:4:9. Which of the following statements are true? (Choose two.)
A. FortiMail applied the default behavior for relaying inbound email
B. FortiMail configuration is missing an access delivery rule to process incoming email
C. Incoming recipient policy ID 9 has the exclusive flag set
D. Email was processed using IP policy ID 4 -
Question 2:
An organization has different groups of users with different needs in email functionality, such as address book access, mobile device access, email retention periods, and disk quotas. Which FortiMail feature specific to server mode can be used to accomplish this?
A. Resource profiles
B. Address book management options
C. Access profiles
D. Domain-level service settings -
Question 3:
Examine the FortiMail topology and IP-based policy shown in the exhibit; then answer the question below.
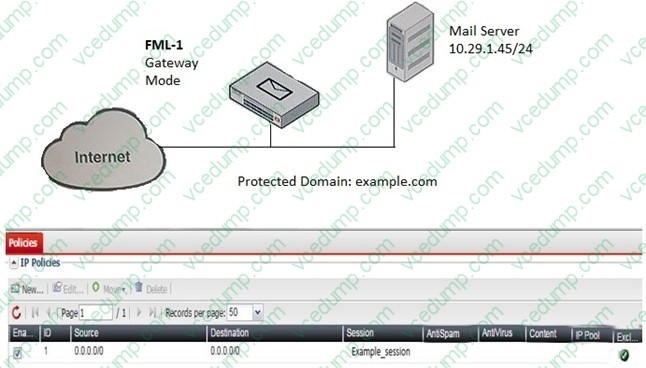
An administrator has enabled the sender reputation feature in the Example_Session profile on FML-1. After a few hours, the deferred queue on the Mail Server started filing up with undeliverable email. What changes should the administrator make to fix this issue? (Choose two.)
A. Clear the sender reputation database using the CLI
B. Create an outbound recipient policy to bypass outbound email from session profile inspections
C. Disable the exclusive flag in IP policy ID 1
D. Apply a session profile with sender reputation disabled on a separate IP policy for outbound sessions -
Question 4:
Which firmware upgrade method for an active-passive HA cluster ensures service outage is minimal and there are no unnecessary failovers?
A. Upgrade the active unit, which will upgrade the standby unit automatically
B. Upgrade both units at the same time
C. Upgrade the standby unit, and then upgrade the active unit
D. Break the cluster, upgrade the units independently, and then form the cluster again as quickly as possible -
Question 5:
Which of the following antispam techniques queries FortiGuard for rating information? (Choose two.)
A. URI filter
B. IP reputation
C. SURBL
D. DNSBL -
Question 6:
Which of the following statements regarding SMTPS and SMTP over TLS are true? (Choose three.)
A. In an SMTPS session, the identities of both sender and receiver are encrypted
B. SMTPS connections are initiated on port 465
C. SMTP over TLS connections are entirely encrypted and initiated on port 465
D. The STARTTLS command is used to initiate SMTP over TLS
E. SMTPS encrypts the body of the email message, where the most sensitive content exists -
Question 7:
A FortiMail is configured with the protected domain "example.com". For this FortiMail, which of the following envelope addresses are considered incoming? (Choose two.)
A. MAIL FROM: training@external.org RCPT TO: students@external.org
B. MAIL FROM: support@example.com PCPT TO: marketing@example.com
C. MAIL FROM: mis@hosted.net RCPT TO: noc@example.com
D. MAIL FROM: accounts@example.com RCPT TO: sales@external.org -
Question 8:
Examine the FortiMail archiving policies shown in the exhibit; then answer the question below.
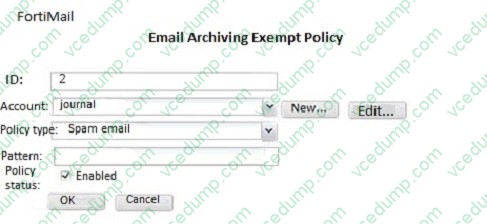
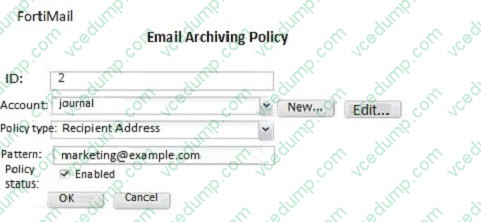
Which of the following statements is true regarding this configuration? (Choose two.)
A. Spam email will be exempt from archiving
B. Email sent from marketing@example.com will be archived
C. Archived email will be saved in the journal account
D. Only the marketing@example.com account will be able to access the archived email -
Question 9:
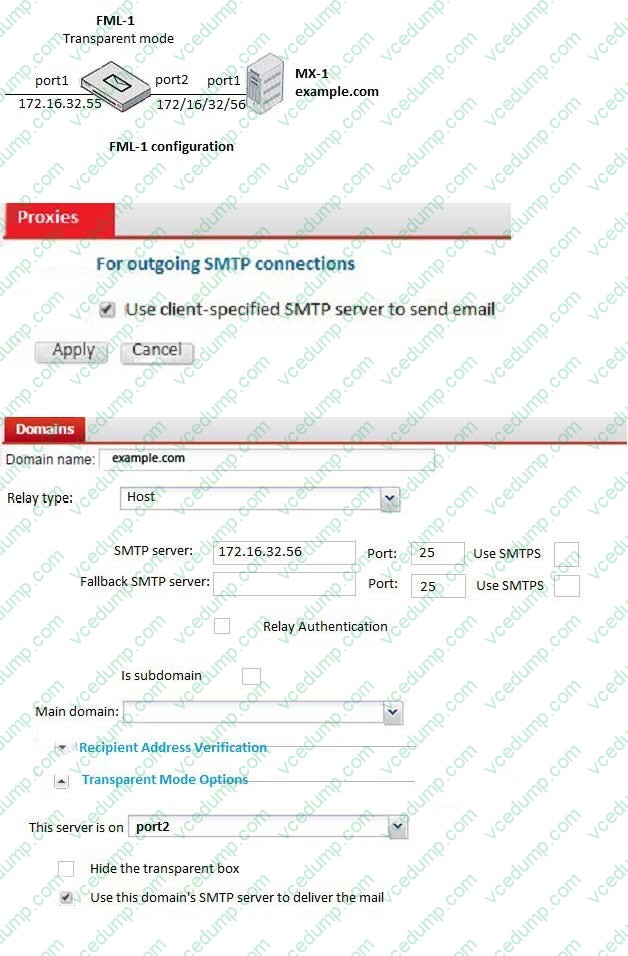
Which of the following statements are true regarding the transparent mode FortiMail's email routing for the example.com domain? (Choose two.)
A. FML-1 will use the built-in MTA for outgoing sessions
B. FML-1 will use the transparent proxy for incoming sessions
C. If incoming email are undeliverable, FML-1 can queue them to retry again later
D. If outgoing email messages are undeliverable, FML-1 can queue them to retry later -
Question 10:
Examine the FortiMail DLP scan rule shown in the exhibit; then answer the question below.
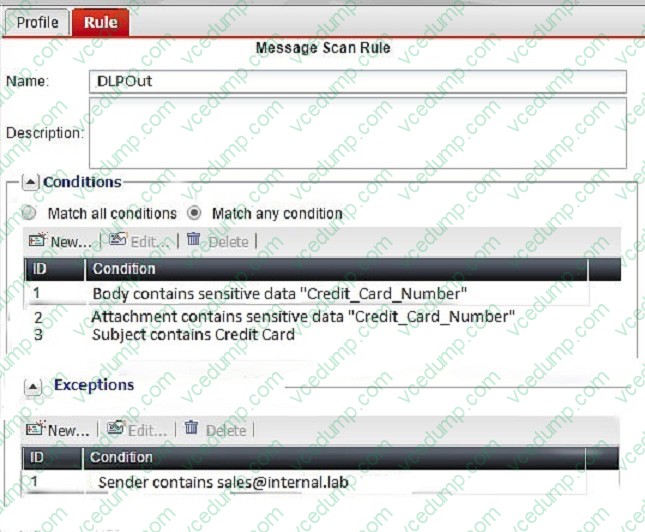
Which of the following statements is true regarding this configuration? (Choose two.)
A. An email message containing the words "Credit Card" in the subject will trigger this scan rule
B. If an email is sent from sales@internal.lab the action will be applied without matching any conditions
C. An email message containing credit card numbers in the body will trigger this scan rule
D. An email must contain credit card numbers in the body, attachment, and subject to trigger this scan rule
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE6_FML-6.0 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.