Exam Details
Exam Code
:NSE5_EDR-5.0Exam Name
:Fortinet NSE 5 - FortiEDR 5.0Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:41 Q&AsLast Updated
:Aug 07, 2025
Fortinet Fortinet Certifications NSE5_EDR-5.0 Questions & Answers
-
Question 31:
Refer to the exhibit.
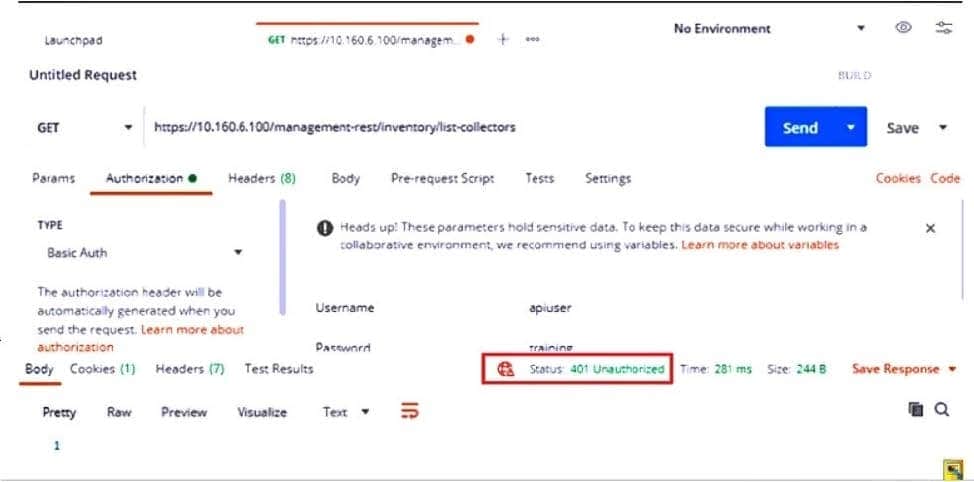
Based on the postman output shown in the exhibit why is the user getting an unauthorized error?
A. The user has been assigned Admin and Rest API roles
B. FortiEDR requires a password reset the first time a user logs in
C. Postman cannot reach the central manager
D. API access is disabled on the central manager
-
Question 32:
Which two types of remote authentication does the FortiEDR management console support? (Choose two.)
A. Radius
B. SAML
C. TACACS D. LDAP
-
Question 33:
Which two statements about the FortiEDR solution are true? (Choose two.)
A. It provides pre-infection and post-infection protection
B. It is Windows OS only
C. It provides central management
D. It provides pant-to-point protection
-
Question 34:
Refer to the exhibit.
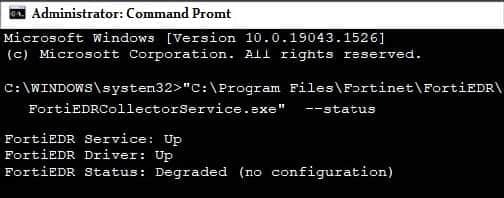
Based on the FortiEDR status output shown in the exhibit, which two statements about the FortiEDR collector are true? (Choose two.)
A. The collector device has windows firewall enabled
B. The collector has been installed with an incorrect port number
C. The collector has been installed with an incorrect registration password
D. The collector device cannot reach the central manager
-
Question 35:
What is the purpose of the Threat Hunting feature?
A. Delete any file from any collector in the organization
B. Find and delete all instances of a known malicious file or hash in the organization
C. Identify all instances of a known malicious file or hash and notify affected users
D. Execute playbooks to isolate affected collectors in the organization
-
Question 36:
What is true about classifications assigned by Fortinet Cloud Sen/ice (FCS)?
A. The core is responsible for all classifications if FCS playbooks are disabled
B. The core only assigns a classification if FCS is not available
C. FCS revises the classification of the core based on its database
D. FCS is responsible for all classifications
-
Question 37:
Refer to the exhibit.
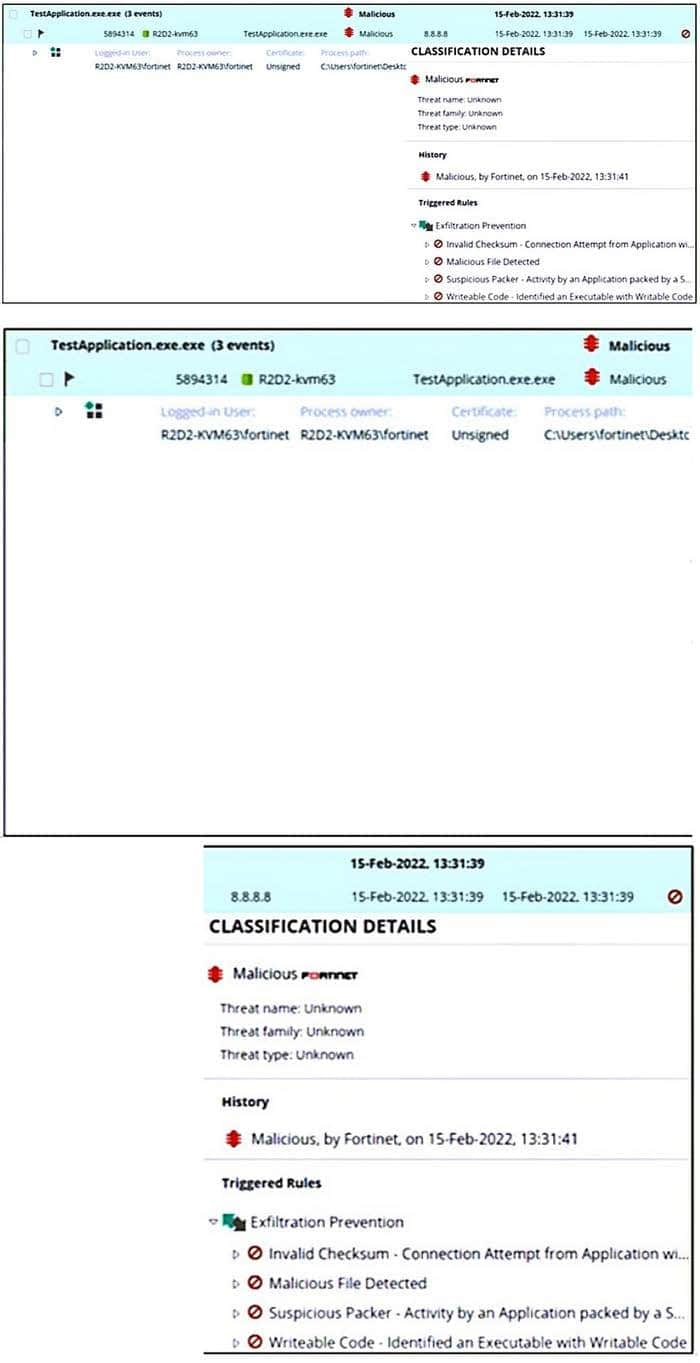
Based on the event shown in the exhibit, which two statements about the event are true? (Choose two.)
A. The NGAV policy has blocked TestApplication exe
B. TestApplication exe is sophisticated malware
C. The user was able to launch TestApplication exe
D. FCS classified the event as malicious
-
Question 38:
How does FortiEDR implement post-infection protection?
A. By preventing data exfiltration or encryption even after a breach occurs
B. By using methods used by traditional EDR
C. By insurance against ransomware
D. By real-time filtering to prevent malware from executing
-
Question 39:
Which security policy has all of its rules disabled by default?
A. Device Control
B. Ransomware Prevention
C. Execution Prevention
D. Exfiltration Prevention
-
Question 40:
Which connectors can you use for the FortiEDR automated incident response? (Choose two.)
A. FortiNAC
B. FortiGate
C. FortiSiem
D. FortiSandbox
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5_EDR-5.0 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.