Exam Details
Exam Code
:NSE5_EDR-5.0Exam Name
:Fortinet NSE 5 - FortiEDR 5.0Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:41 Q&AsLast Updated
:Aug 07, 2025
Fortinet Fortinet Certifications NSE5_EDR-5.0 Questions & Answers
-
Question 11:
Which three steps does FortiXDR perform to find and prevent cyberattacks? (Choose three.)
A. Extended analysis
B. Extended detection
C. Extended discovery
D. Extended investigation
E. Extended response
-
Question 12:
An administrator finds a third party free software on a user's computer mat does not appear in me application list in the communication control console
Which two statements are true about this situation? (Choose two)
A. The application is allowed in all communication control policies
B. The application is ignored as the reputation score is acceptable by the security policy
C. The application has not made any connection attempts
D. The application is blocked by the security policies
-
Question 13:
Exhibit.
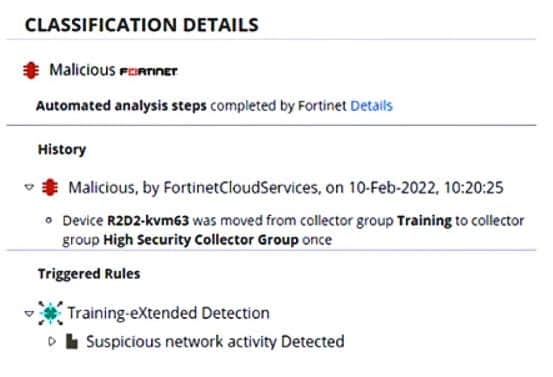
Based on the event shown in the exhibit which two statements about the event are true? (Choose two.)
A. The device is moved to isolation.
B. Playbooks is configured for this event.
C. The event has been blocked
D. The policy is in simulation mode
-
Question 14:
Which FortiEDR component is required to find malicious files on the entire network of an organization?
A. FortiEDR Aggregator
B. FortiEDR Central Manager
C. FortiEDR Threat Hunting Repository
D. FortiEDR Core
-
Question 15:
Which threat hunting profile is the most resource intensive?
A. Comprehensive
B. Inventory
C. Default
D. Standard Collection
-
Question 16:
What is the role of a collector in the communication control policy?
A. A collector blocks unsafe applications from running
B. A collector is used to change the reputation score of any application that collector runs
C. A collector records applications that communicate externally
D. A collector can quarantine unsafe applications from communicating
-
Question 17:
A company requires a global communication policy for a FortiEDR multi-tenant environment.
How can the administrator achieve this?
A. An administrator creates a new communication control policy and shares it with other organizations
B. A local administrator creates new a communication control policy and shares it with other organizations
C. A local administrator creates a new communication control policy and assigns it globally to all organizations
D. An administrator creates a new communication control policy for each organization
-
Question 18:
Exhibit.
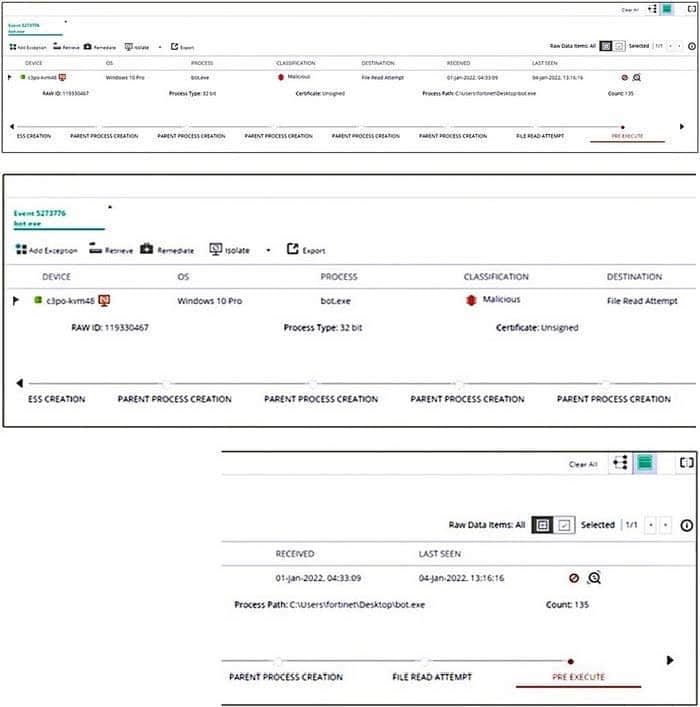
Based on the forensics data shown in the exhibit, which two statements are true? (Choose two.)
A. An exception has been created for this event
B. The forensics data is displayed m the stacks view
C. The device has been isolated
D. The exfiltration prevention policy has blocked this event
-
Question 19:
A FortiEDR security event is causing a performance issue with a third-parry application. What must you do first about the event?
A. Contact Fortinet support
B. Terminate the process and uninstall the third-party application
C. Immediately create an exception
D. Investigate the event to verify whether or not the application is safe
-
Question 20:
Refer to the exhibit.
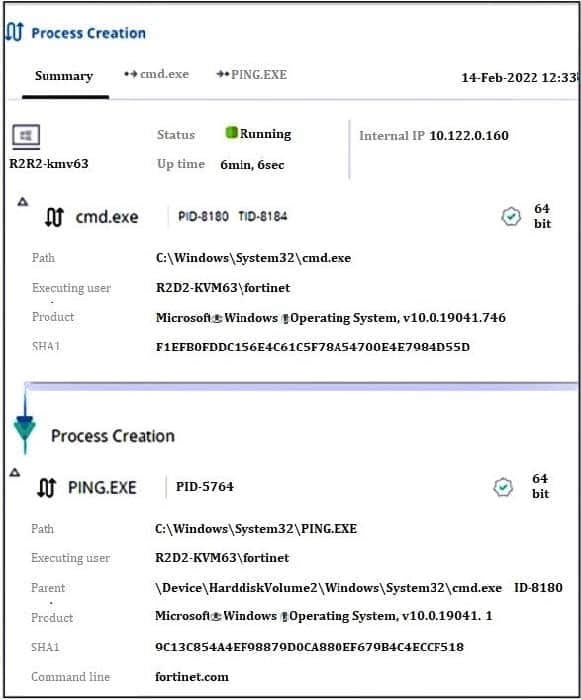
Based on the threat hunting event details shown in the exhibit, which two statements about the event are true? (Choose two.)
A. The PING EXE process was blocked
B. The user fortinet has executed a ping command
C. The activity event is associated with the file action
D. There are no MITRE details available for this event
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5_EDR-5.0 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.