Exam Details
Exam Code
:NSE5Exam Name
:Fortinet Network Security Expert 5 Written Exam (500)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:320 Q&AsLast Updated
:Jul 12, 2025
Fortinet Fortinet Certifications NSE5 Questions & Answers
-
Question 31:
Which Fortinet products and features could be considered part of a comprehensive solution to monitor and prevent the leakage of senstive data? (Select all that apply.)
A. Archive non-compliant outgoing e-mails using FortiMail.
B. Restrict unofficial methods of transferring files such as P2P using Application Control lists on a FortiGate.
C. Monitor database activity using FortiAnalyzer.
D. Apply a DLP sensor to a firewall policy.
E. Configure FortiClient to prevent files flagged as sensitive from being copied to a USB disk.
-
Question 32:
What is the effect of using CLI "config system session-ttl" to set session_ttl to 1800 seconds?
A. Sessions can be idle for no more than 1800 seconds.
B. The maximum length of time a session can be open is 1800 seconds.
C. After 1800 seconds, the end user must reauthenticate.
D. After a session has been open for 1800 seconds, the FortiGate unit will send a keepalive packet to both client and server.
-
Question 33:
Which statements are correct regarding FortiAnalyzer reports? (Choose two.)
A. FortiAnalyzer provides the ability to create custom reports.
B. FortiAnalyzer allows you to schedule reports to run.
C. FortiAnalyzer includes pre-defined reports only.
D. FortiAnalyzer allows reporting for FortiGate devices only.
-
Question 34:
Which part of an email message exchange is NOT inspected by the POP3 and IMAP proxies?
A. TCP connection
B. File attachments
C. Message headers
D. Message body
-
Question 35:
Which of the following statements best describes the green status indicators that appear next to different FortiGuard Distribution Network services as illustrated in the exhibit?
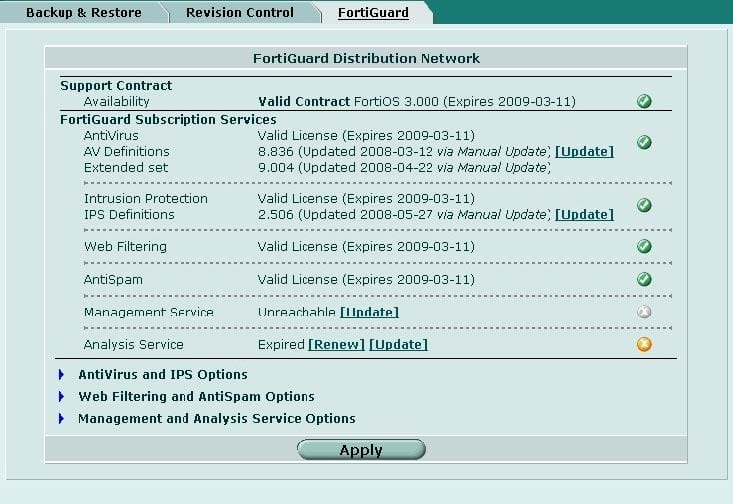
A. They indicate that the FortiGate unit is able to connect to the FortiGuard Distribution Network.
B. They indicate that the FortiGate unit has the latest updates that are available from the FortiGuard Distribution Network.
C. They indicate that updates are available and should be downloaded from the FortiGuard Distribution Network to the FortiGate unit.
D. They indicate that the FortiGate unit is in the process of downloading updates from the FortiGuard Distribution Network.
-
Question 36:
The diag sys session list command is executed in the CLI. The output of this command is shown in the exhibit.
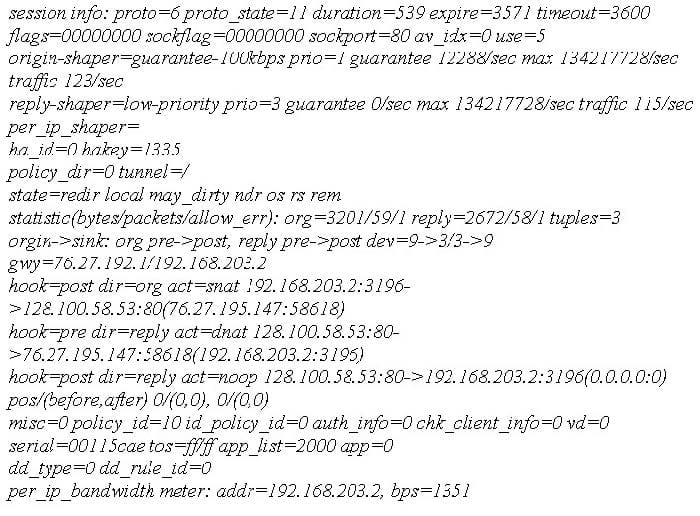
Based on the output from this command, which of the following statements is correct?
A. This is a UDP session.
B. Traffic shaping is being applied to this session.
C. This is an ICMP session.
D. This traffic has been authenticated.
E. This session matches a firewall policy with ID 5.
-
Question 37:
An administrator wants to assign a set of UTM features to a group of users. Which of the following is the correct method for doing this?
A. Enable a set of unique UTM profiles under "Edit User Group".
B. The administrator must enable the UTM profiles in an identity-based policy applicable to the user group.
C. When defining the UTM objects, the administrator must list the user groups which will use the UTM object.
D. The administrator must apply the UTM features directly to a user object.
-
Question 38:
Which part of an email message exchange is NOT inspected by the POP3 and IMAP proxies?
A. TCP connection
B. File attachments
C. Message headers
D. Message body
-
Question 39:
You wish to create a firewall policy that applies only to traffic intended for your web server. The web server has an IP address of 192.168.2.2 and a /24 subnet mask.
When defining the firewall address for use in this policy, which one of the following addresses is correct?
A. 192.168.2.0 / 255.255.255.0
B. 192.168.2.2 / 255.255.255.0
C. 192.168.2.0 / 255.255.255.255
D. 192.168.2.2 / 255.255.255.255
-
Question 40:
An end user logs into the full-access SSL VPN portal and selects the Tunnel Mode option by clicking on the "Connect" button. The administrator has enabled split tunneling.
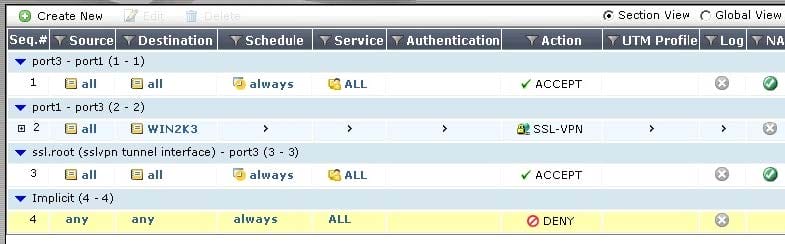
Given that the user authenticates against the SSL VPN policy shown in the image below, which statement below identifies the route that is added to the client's routing table.
A. A route to destination matching the `WIN2K3' address object.
B. A route to the destination matching the `all' address object.
C. A default route.
D. No route is added.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.