Exam Details
Exam Code
:NSE5Exam Name
:Fortinet Network Security Expert 5 Written Exam (500)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:320 Q&AsLast Updated
:Jul 12, 2025
Fortinet Fortinet Certifications NSE5 Questions & Answers
-
Question 91:
When firewall policy authentication is enabled, only traffic on supported protocols will trigger an authentication challenge.
Select all supported protocols from the following:
A. SMTP
B. SSH
C. HTTP
D. FTP
E. SCP
-
Question 92:
Which of the following statements are correct regarding URL filtering on the FortiGate unit? (Select all that apply.)
A. The allowed actions for URL Filtering include Allow, Block and Exempt.
B. The allowed actions for URL Filtering are Allow and Block.
C. The FortiGate unit can filter URLs based on patterns using text and regular expressions.
D. Any URL accessible by a web browser can be blocked using URL Filtering.
E. Multiple URL Filter lists can be added to a single protection profile.
-
Question 93:
A user selects Install Config for a managed FortiGate device, as shown in the exhibit.
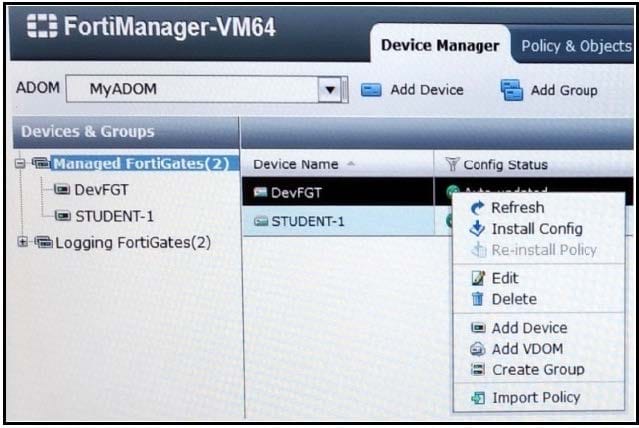
Which two statements are true regarding this action? (Choose two.)
A. It provides the option to preview configuration changes prior to installing them.
B. It allows you to perform a quick install of device level settings, without the need to launch the Install wizard.
C. Once initiated, the install process cannot be cancelled and changes will be installed on the managed device.
D. It will launch the Install wizard to install any configuration changes to the managed device.
-
Question 94:
An administrator wishes to generate a report showing Top Traffic by service type. They notice that web traffic overwhelms the pie chart and want to exclude the web traffic from the report.
Which of the following statements best describes how to do this?
A. In the Service field of the Data Filter, type 80/tcp and select the NOT checkbox.
B. Add the following entry to the Generic Field section of the Data Filter: service="!web".
C. When editing the chart, uncheck wlog to indicate that Web Filtering data is being excluded when generating the chart.
D. When editing the chart, enter 'http' in the Exclude Service field.
-
Question 95:
Which of the following is true regarding Switch Port Mode?
A. Allows all internal ports to share the same subnet.
B. Provides separate routable interfaces for each internal port.
C. An administrator can select ports to be used as a switch.
D. Configures ports to be part of the same broadcast domain.
-
Question 96:
With FSSO, a domain user could authenticate either against the domain controller running the Collector Agent and Domain Controller Agent, or a domain controller running only the Domain Controller Agent.
If you attempt to authenticate with the Secondary Domain Controller running only the Domain Controller Agent, which of the following statements are correct? (Select all that apply.)
A. The login event is sent to the Collector Agent.
B. The FortiGate unit receives the user information from the Domain Controller Agent of the Secondary Controller.
C. The Collector Agent performs the DNS lookup for the authenticated client's IP address.
D. The user cannot be authenticated with the FortiGate device in this manner because each Domain Controller Agent requires a dedicated Collector Agent.
-
Question 97:
Which of the following Session TTL values will take precedence?
A. Session TTL specified at the system level for that port number
B. Session TTL specified in the matching firewall policy
C. Session TTL dictated by the application control list associated with the matching firewall policy
D. The default session TTL specified at the system level
-
Question 98:
A firewall policy has been configured for the internal email server to receive email from external parties through SMTP. Exhibits A and B show the AntiVirus and Email Filter profiles applied to this policy.
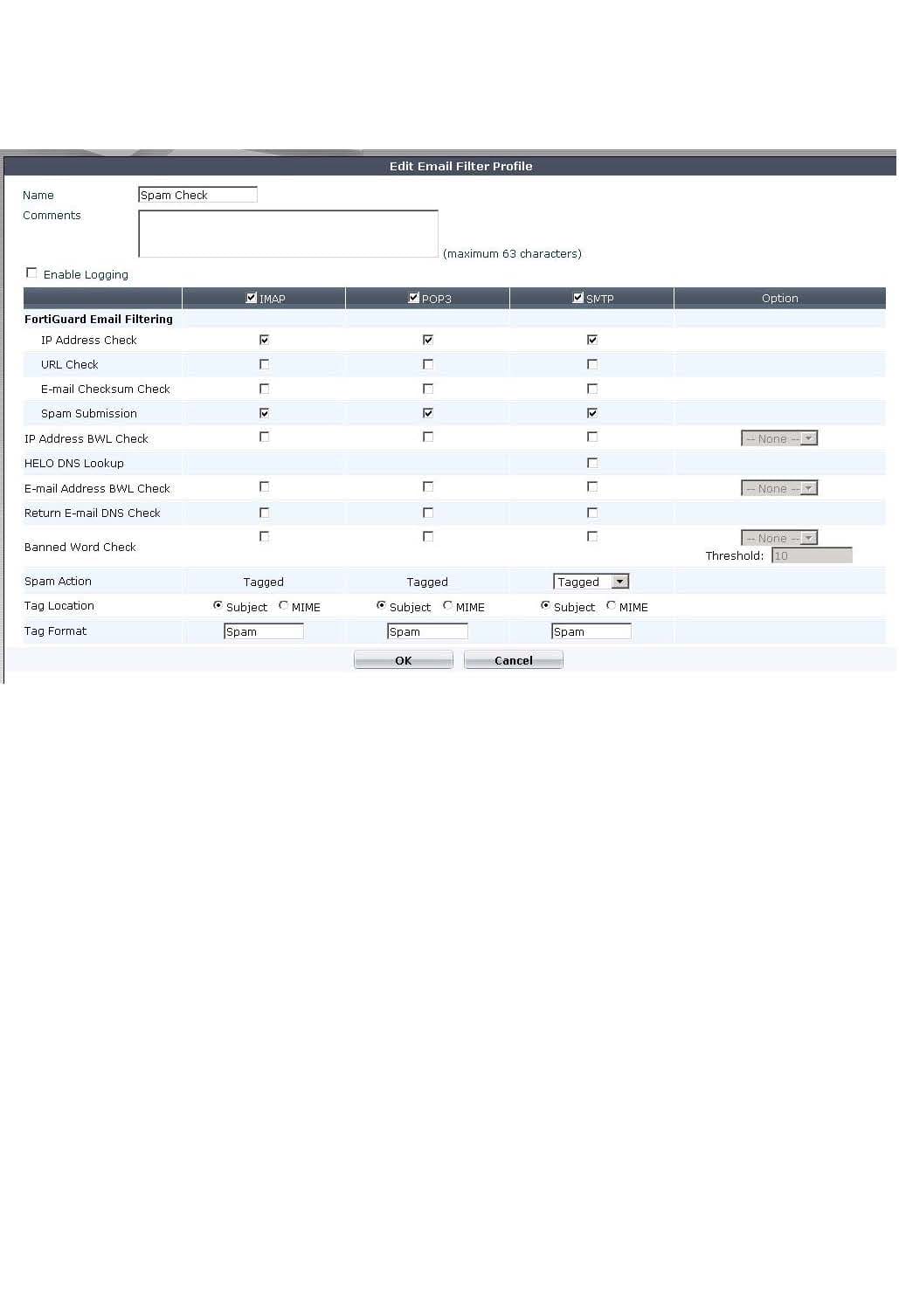
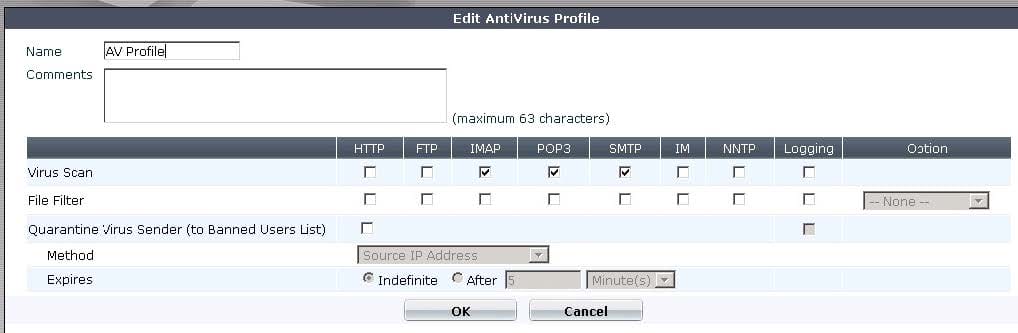
What is the correct behavior when the email attachment is detected as a virus by the FortiGate AntiVirus engine?
A. The FortiGate unit will remove the infected file and deliver the email with a replacement message to alert the recipient that the original attachment was infected.
B. The FortiGate unit will reject the infected email and notify both the sender and recipient.
C. The FortiGate unit will remove the infected file and add a replacement message. Both sender and recipient are notified that the infected file has been removed.
D. The FortiGate unit will reject the infected email and notify the sender.
-
Question 99:
Which of the following logging options are supported on a FortiGate unit? (Select all that apply.)
A. LDAP
B. Syslog
C. FortiAnalyzer
D. Local disk and/or memory
-
Question 100:
A network administrator connects his PC to the INTERNAL interface on a FortiGate unit. The administrator attempts to make an HTTPS connection to the FortiGate unit on the VLAN1 interface at the IP address of 10.0.1.1, but gets no connectivity.
The following troubleshooting commands are executed from the DOS prompt on the PC and from the CLI. C:\>ping 10.0.1.1 Pinging 10.0.1.1 with 32 bytes of data: Reply from 10.0.1.1: bytes=32 time=1ms TTL=255 Reply from 10.0.1.1: bytes=32 time<1ms TTL=255 Reply from 10.0.1.1: bytes=32 time<1ms TTL=255 Reply from 10.0.1.1: bytes=32 time<1ms TTL=255
user1 # get system interface == [ internal ] name. internal mode. static ip: 10.0.1.254 255.255.255.128 status: up netbios-forward. disable type. physical mtu-override. disable
== [ vlan1 ]
name. vlan1 mode. static ip: 10.0.1.1 255.255.255.128 status: up netb
ios-forward. disable type. vlan mtu-override. disable
user1 # diagnose debug flow trace start 100
user1 # diagnose debug ena
user1 # diagnose debug flow filter daddr 10.0.1.1 10.0.1.1
id=20085 trace_id=274 msg="vd-root received a packet(proto=6, 10.0.1.130:47927- >10.0.1.1:443) from
internal."
id=20085 trace_id=274 msg="allocate a new session-00000b1b"
id=20085 trace_id=274 msg="find SNAT: IP-10.0.1.1, port-43798"
id=20085 trace_id=274 msg="iprope_in_check() check failed, drop"
Based on the output from these commands, which of the following explanations is a possible cause of the
problem?
A. The Fortigate unit has no route back to the PC.
B. The PC has an IP address in the wrong subnet.
C. The PC is using an incorrect default gateway IP address.
D. The FortiGate unit does not have the HTTPS service configured on the VLAN1 interface.
E. There is no firewall policy allowing traffic from INTERNAL-> VLAN1.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE5 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.