Exam Details
Exam Code
:NSE4_FGT-5.6Exam Name
:Fortinet NSE 4 - FortiOS 5.6Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:114 Q&AsLast Updated
:Jul 10, 2025
Fortinet Fortinet Certifications NSE4_FGT-5.6 Questions & Answers
-
Question 71:
How are the application control signatures updated on a FortiGate device? Response:
A. By running the application control auto-learning feature.
B. Through FortiGuard updates.
C. By upgrading the FortiOS firmware to a newer release.
D. By clicking Update Signatures in the application control profile.
-
Question 72:
Which statements about One-to-One IP pool are true?
(Choose two.)
Response:
A. It allows configuration of ARP replies.
B. It allows fixed mapping of an internal address range to an external address range.
C. It is used for destination NAT.
D. It does not use port address translation.
-
Question 73:
Under what circumstance would you enable LEARN as the Action on a firewall policy? Response:
A. You want FortiGate to compile security feature activity from various security-related logs, such as virus and attack logs.
B. You want FortiGate to monitor a specific security profile in a firewall policy, and provide recommendations for that profile.
C. You want to capture data across all traffic and security vectors, and receive learning logs and a report with recommendations.
D. You want FortiGate to automatically modify your firewall policies as it learns your networking behavior.
-
Question 74:
You have configured the following log settings on the Log Settings page. Which configurations are now
required to generate log messages on traffic coming through your network?
(Choose two.)
Response:
A. Enable Log Allowed Traffic on your firewall policy.
B. Enable Local Traffic Log on the Log Settings page.
C. Enable Historical FortiView on the Log Settings page.
D. Enable a security profile on your firewall policy.
E. Enable Capture Packets on your firewall policy.
-
Question 75:
What is the Unknown Applications category option in the application control profile?
Response:
A. Any traffic that does not match the RFC pattern for its protocol.
B. Any traffic that does not match an application control signature.
C. Any traffic whose packet fails the CRC check.
D. Any traffic that matches custom application control signatures.
-
Question 76:
Which actions can be configured in an application control profile?
(Choose three.)
Response:
A. Monitor
B. Block
C. Warning
D. Authenticate
E. Quarantine
-
Question 77:
View the exhibit.
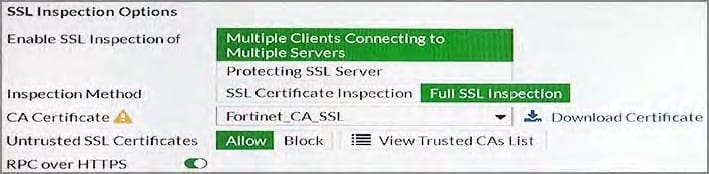
When a user attempts to connect to an HTTPS site, what is the expected result with this configuration? Response:
A. The user is required to authenticate before accessing sites with untrusted SSL certificates.
B. The user is presented with certificate warnings when connecting to sites that have untrusted SSL certificates.
C. The user is allowed access all sites with untrusted SSL certificates, without certificate warnings.
D. The user is blocked from connecting to sites that have untrusted SSL certificates (no exception provided).
-
Question 78:
Which of the following are differences between IPsec main mode and IPsec aggressive mode?
(Choose two.)
Response:
A. Aggressive mode supports XAuth, while main mode does not.
B. Six packets are usually exchanged during main mode, while only three packets are exchanged during aggressive mode.
C. The first packet of aggressive mode contains the peer ID, while the first packet of main mode does not.
D. Main mode cannot be used for dialup VPNs, while aggressive mode can.
-
Question 79:
Which statement is true about split tunneling in SSL VPN? Response:
A. It is supported in web-only mode.
B. It can be enabled by the SSL VPN user, after connecting to the SSL VPN.
C. If enabled, Internet traffic uses the local gateway of the connecting host.
D. If disabled, SSL VPN users must authenticate using FortiToken.
-
Question 80:
Which of the following statements regarding FortiGate inspection modes are correct?
(Choose three.)
Response:
A. Proxy-based inspection mode supports more features.
B. Flow-based is the default FortiGate inspection mode.
C. Switching from proxy-based inspection mode to flow-based inspection mode will result in a warning message.
D. Security profiles must be manually converted to flow-based before switching the inspection mode from proxy-based to flow-based.
E. Switching from proxy-based to flow-based and then back to proxy-based will not produce original configurations.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-5.6 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.