Exam Details
Exam Code
:NSE4_FGT-5.6Exam Name
:Fortinet NSE 4 - FortiOS 5.6Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:114 Q&AsLast Updated
:Jul 10, 2025
Fortinet Fortinet Certifications NSE4_FGT-5.6 Questions & Answers
-
Question 61:
Which are the different types of memory conserve mode that can occur on a FortiGate device?
(Choose two.)
Response:
A. System
B. Device
C. Kernel
D. Flow
-
Question 62:
Which statements about an IPv6-over-IPv4 IPsec configuration are correct?
(Choose two.)
Response:
A. The remote gateway IP must be an IPv6 address.
B. The source quick mode selector must be an IPv4 address.
C. The local gateway IP must an IPv4 address.
D. The destination quick mode selector must be an IPv6 address.
-
Question 63:
You have enabled a web filter security profile in a firewall policy to log all blocked websites. What options do you have to either actively or passively monitor these logs? (Choose two.)
Response: A. Alert Message console
B. FortiView menu
C. Alert email
D. Monitor menu
-
Question 64:
Which statements about the firmware upgrade process on an active-active high availability (HA) cluster are
true?
(Choose two.)
Response:
A. The firmware image must be manually uploaded to each FortiGate.
B. Only secondary FortiGate devices are rebooted.
C. Uninterruptable upgrade is enabled by default.
D. Traffic load balancing is temporally disabled while upgrading the firmware.
-
Question 65:
Under which circumstance is the IPsec ESP traffic encapsulated over UDP? Response:
A. When using IKE version 2 (IKEv2)
B. When the phase 1 is configured to use aggressive mode
C. When the IPsec VPN is configured as dial-up
D. When NAT-T detects there is a device between both IPsec peers doing NAT over the IPsec traffic
-
Question 66:
Examine this output from a debug flow:
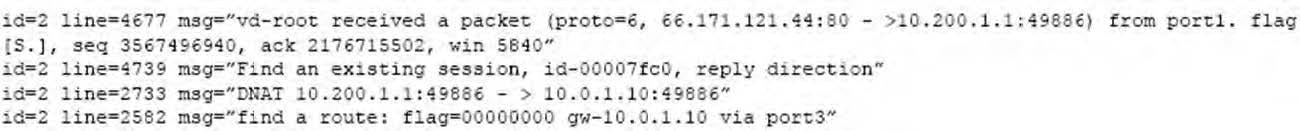
Which statements about the output are correct?
(Choose two.)
Response:
A. FortiGate received a TCP SYN/ACK packet.
B. The source IP address of the packet was translated to 10.0.1.10.
C. FortiGate routed the packet through port 3.
D. The packet was allowed by the firewall policy with the ID 00007fc0.
-
Question 67:
Which of the following statements about advanced AD access mode for the FSSO collector agent are true? (Choose two.)
Response:
A. FortiGate can act as an LDAP client to configure the group filters.
B. It is only supported if DC agents are deployed.
C. It supports monitoring of nested groups.
D. It uses the Windows convention for naming; that is, Domain\Username.
-
Question 68:
How do you configure inline SSL inspection on a firewall policy?
(Choose two.)
Response:
A. Enable one or more flow-based security profiles on the firewall policy.
B. Enable the SSL/SSH Inspection profile on the firewall policy.
C. Execute the inline ssl inspection CLI command.
D. Enable one or more proxy-based security profiles on the firewall policy.
-
Question 69:
Which statements about antivirus scanning using flow-based full scan are true?
(Choose two.)
Response:
A. The antivirus engine starts scanning a file after the last packet arrives.
B. It does not support FortiSandbox inspection.
C. FortiGate can insert the block replacement page during the first connection attempt only if a virus is detected at the start of the TCP stream.
D. It uses the compact antivirus database.
-
Question 70:
FortiGate scans packets for matches in a specific order for application control. Which option provides the correct sequence order?
Response:
A. Static domain overrides -> application overrides -> filter overrides
B. Categories -> application overrides -> filter overrides
C. Application overrides -> filter overrides -> categories
D. Rate based overrides -> filter overrides -> categories
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4_FGT-5.6 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.