Exam Details
Exam Code
:NSE4Exam Name
:Fortinet Network Security Expert 4 Written Exam (400)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:301 Q&AsLast Updated
:Apr 21, 2024
Fortinet Fortinet Certifications NSE4 Questions & Answers
-
Question 41:
Two FortiGate devices fail to form an HA cluster, the device hostnames are STUDENT and REMOTE. Exhibit A shows the command output of show system ha for the STUDENT device. Exhibit B shows the command output of show system ha for the REMOTE device.
Exhibit A:
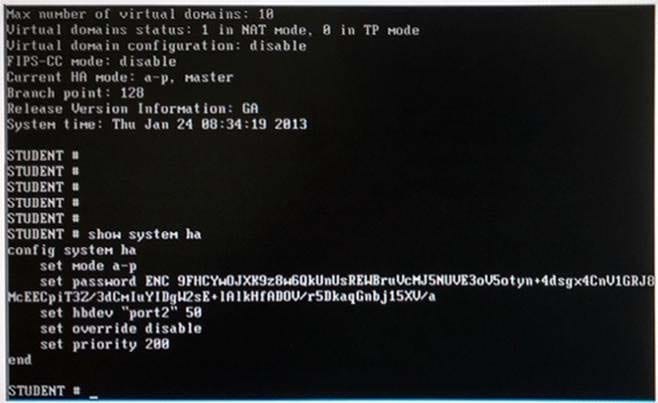
Exhibit B:
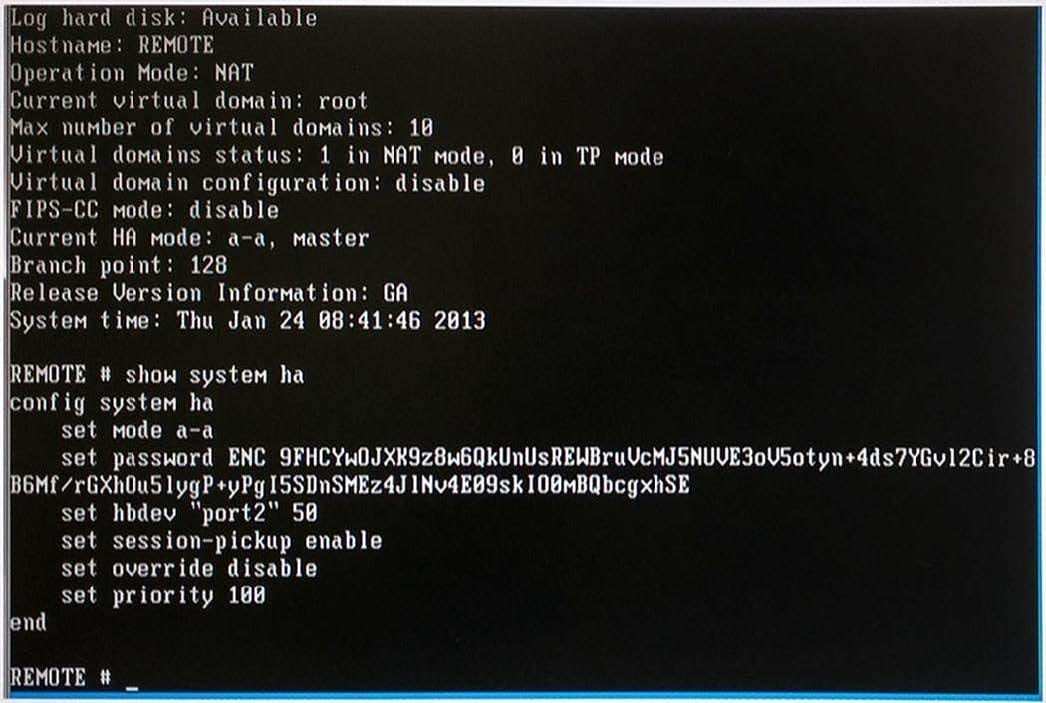
Which one of the following is the most likely reason that the cluster fails to form?
A. Password
B. HA mode
C. Hearbeat
D. Override
-
Question 42:
Which of the following statements are true regarding WAN Link Load Balancing? (Choose two).
A. There can be only one virtual WAN Link per VDOM.
B. FortiGate can measure the quality of each link based on latency, jitter, or packets percentage.
C. Link health checks can be performed over each link member if the virtual WAN interface.
D. Distance and priority values are configured in each link member if the virtual WAN interface.
-
Question 43:
Which statements correctly describe transparent mode operation? (Choose three.)
A. The FortiGate acts as transparent bridge and forwards traffic at Layer-2.
B. Ethernet packets are forwarded based on destination MAC addresses, NOT IP addresses.
C. The transparent FortiGate is clearly visible to network hosts in an IP trace route.
D. Permits inline traffic inspection and firewalling without changing the IP scheme of the network.
E. All interfaces of the transparent mode FortiGate device most be on different IP subnets.
-
Question 44:
The exhibit shows two static routes to the same destinations subnet 172.20.168.0/24.
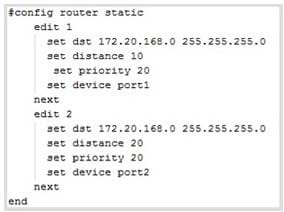
Which of the following statements correctly describes this static routing configuration? (choose two)
A. Both routes will show up in the routing table.
B. The FortiGate unit will evenly share the traffic to 172.20.168.0/24 between routes.
C. Only one route will show up in the routing table.
D. The FortiGate will route the traffic to 172.20.168.0/24 only through one route.
-
Question 45:
Which profile could IPS engine use on an interface that is in sniffer mode? (Choose three)
A. Antivirus (flow based
B. Web filtering (PROXY BASED)
C. Intrusion Protection
D. Application Control
E. Endpoint control
-
Question 46:
Of the following information, what can be recorded by a Data Leak Prevention sensor configured to do a summary archiving? (Choose three.)
A. Visited URL (for the case of HTTP traffic)
B. Sender email address (for the case of SMTP traffic)
C. Recipient email address (for the case of SMTP traffic)
D. Attached file (for the case of SMTP traffic)
E. Email body (for the case of SMTP traffic)
-
Question 47:
Examine the exhibit; then answer the question below.
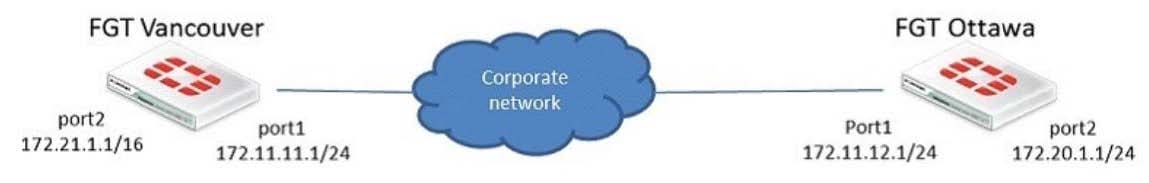
The Vancouver FortiGate initially had the following information in its routing table: S 172.20.0.0/16 [10/0] via 172.21.1.2, port2 C 172.21.0.0/16 is directly connected, port2 C 172.11.11.0/24 is directly connected, port1 Afterwards, the following static route was added: config router static edit 6 set dst 172.20.1.0 255.255.255.0 set priority 0 set device port1 set gateway 172.11.12.1 next Since this change, the new static route is NOT showing up in the routing table. Given the information
provided, which of the following describes the cause of this problem?
A. The subnet 172.20.1.0/24 is overlapped with the subnet of one static route that is already in the routing table (172.20.0.0/16), so, we need to enable allow-subnet-overlap first.
B. The 'gateway' IP address is NOT in the same subnet as the IP address of port1.
C. The priority is 0, which means that the route will remain inactive.
D. The static route configuration is missing the distance setting.
-
Question 48:
How is traffic routed onto an SSL VPN tunnel from the FortiGate unit side?
A. A static route must be configured by the administrator using the ssl.root interface as the outgoing interface.
B. Assignment of an IP address to the client causes a host route to be added to the FortiGate unit's kernel routing table.
C. A route back to the SSLVPN IP pool is automatically created on the FortiGate unit.
D. The FortiGate unit adds a route based upon the destination address in the SSL VPN firewall policy.
-
Question 49:
Examine the following log message for IPS:
2012-07-01 09:54:28 oid=2 log_id=18433 type=ips subtype=anomaly pri=alert vd=root
severity=''critical'' src=''192.168.3.168'' dst=''192.168.3.170'' src_int=''port2'' serial=0
status=''detected'' proto=1 service=''icmp'' count=1 attack_name=''icmp_flood'' icmp_id=''0xa8a4''
icmp_type=''0x08'' icmp_code=''0x00'' attack_id=16777316 sensor=''1''
ref=''http://www.fortinet.com/ids/VID16777316'' msg=''anomaly: icmp_flood, 51 > threshold 50''
Which statement is correct about the above log? (Choose two.)
A. The target is 192.168.3.168.
B. The target is 192.168.3.170.
C. The attack was NOT blocked.
D. The attack was blocked.
-
Question 50:
Which of the following statements are true about PKI users created in a FortiGate device? (Choose two.)
A. Can be used for token-based authentication
B. Can be used for two-factor authentication
C. Are used for certificate-based authentication
D. Cannot be members of user groups
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.