Exam Details
Exam Code
:NSE4Exam Name
:Fortinet Network Security Expert 4 Written Exam (400)Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:301 Q&AsLast Updated
:Apr 21, 2024
Fortinet Fortinet Certifications NSE4 Questions & Answers
-
Question 31:
Which of the following web filtering modes can inspect the full URL? (Choose two.)
A. Proxy based
B. DNS based
C. Policy based
D. Flow based
-
Question 32:
Which IPsec configuration mode can be used for implementing GRE-over-IPsec VPNs?
A. Policy-based only.
B. Route-based only.
C. Either policy-based or route-based VPN.
D. GRE-based only.
-
Question 33:
What is the FortiGate password recovery process?
A. Interrupt boot sequence, modify the boot registry and reboot. After changing the password, reset the boot registry.
B. Log in through the console port using the ''maintainer'' account within several seconds of physically power cycling the FortiGate.
C. Hold down the CTRL + Esc (Escape) keys during reboot, then reset the admin password.
D. Interrupt the boot sequence and restore a configuration file for which the password has been modified.
-
Question 34:
Review the configuration for FortiClient IPsec shown in the exhibit.
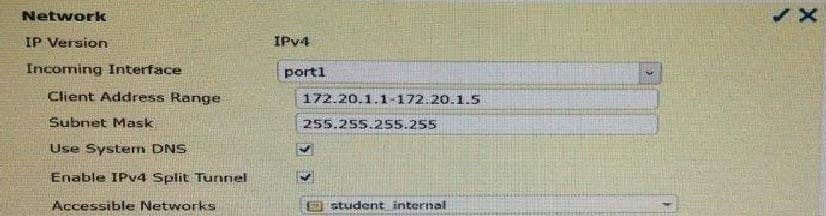
Which statement is correct regarding this configuration?
A. The connecting VPN client will install a route to a destination corresponding to the student internal address object.
B. The connecting VPN client will install a default route.
C. The connecting VPN client will install a route to the 172.20.1.[1-5] address range.
D. The connecting VPN client will connect in web portal mode and no route will be installed.
-
Question 35:
Which of the following statements are correct differences between NAT/route and transparent mode? (Choose two.)
A. In transparent mode, interfaces do not have IP addresses.
B. Firewall polices are only used in NAT/ route mode.
C. Static routers are only used in NAT/route mode.
D. Only transparent mode permits inline traffic inspection at layer 2.
-
Question 36:
What is required in a FortiGate configuration to have more than one dialup IPsec VPN using aggressive mode?
A. All the aggressive mode dialup VPNs MUST accept connections from the same peer ID.
B. Each peer ID MUST match the FQDN of each remote peer.
C. Each aggressive mode dialup MUST accept connections from different peer ID.
D. The peer ID setting must NOT be used.
-
Question 37:
What methods can be used to deliver the token code to a user that is configured to use two-factor authentication? (Choose three.)
A. Browser pop-up window.
B. FortiToken.
C. Email.
D. Code books.
E. SMS phone message.
-
Question 38:
A FortiGate device is configured with two VDOMs. The management VDOM is 'root' , and is configured in transparent mode,'vdom1' is configured as NAT/route mode. Which traffic is generated only by 'root' and not 'vdom1'? (Choose three.)
A. SNMP traps
B. FortiGaurd
C. ARP
D. NTP
E. ICMP redirect
-
Question 39:
Which of the following email spam filtering features is NOT supported on a FortiGate unit?
A. Multipurpose Internet Mail Extensions (MIME) Header Check
B. HELO DNS Lookup
C. Greylisting
D. Banned Word
-
Question 40:
Review the IPS sensor filter configuration shown in the exhibit.
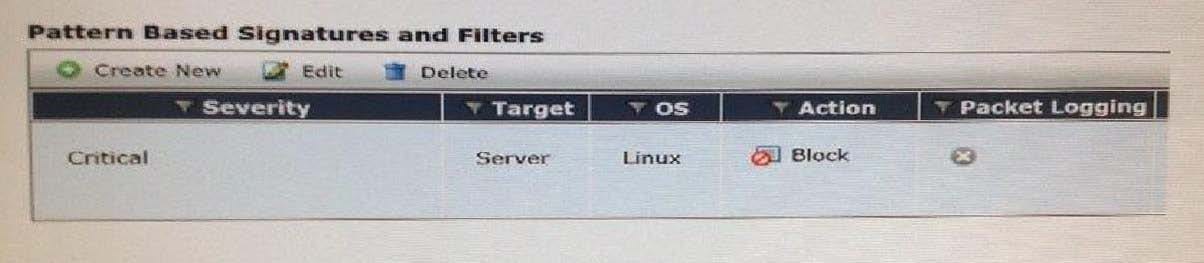
Based on the information in the exhibit, which statements are correct regarding the filter? (Choose two.)
A. It does not log attacks targeting Linux servers.
B. It matches all traffic to Linux servers.
C. Its action will block traffic matching these signatures.
D. It only takes affect when the sensor is applied to a policy.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE4 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.