Exam Details
Exam Code
:N10-008Exam Name
:CompTIA Network+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1219 Q&AsLast Updated
:Feb 16, 2025
CompTIA CompTIA Certifications N10-008 Questions & Answers
-
Question 181:
Which of the following would most likely be considered for an IDF installation in a secure facility?
A. Full-size body scanners
B. Iris scanner
C. RFID badge readers
D. Smart deadbolt
-
Question 182:
Which of the following are environmental factors that should be considered when installing equipment in a building? (Choose two.)
A. Fire suppression system
B. UPS location
C. Humidity control
D. Power load
E. Floor construction type
F. Proximity to nearest MDF
-
Question 183:
Which of the following cloud deployment models involves servers that are hosted at a company's property and are only used by that company?
A. Public
B. Private
C. Hybrid
D. Community
-
Question 184:
A technician needs to find the MAC address of a connecting router. Which of the following commands should the technician use?
A. arp
B. traceroute
C. nslookup
D. ping
-
Question 185:
A technician needs to set up a wireless connection that utilizes MIMO on non-overlapping channels. Which of the following would be the best choice?
A. 802.11a
B. 802.11b
C. 802.11g
D. 802.11n
-
Question 186:
A network engineer designed and implemented a new office space with the following characteristics:

One month after the office space was implemented, users began reporting dropped signals when entering another room and overall poor connections to the 5GHz network. Which of the following should the engineer do to best resolve the issue?
A. Use non-overlapping channels.
B. Reconfigure the network to support 2.4GHz
C. Upgrade to WPA3.
D. Change to directional antennas.
-
Question 187:
A network technician is troubleshooting internet connectivity issues with users in a subnet. From a host, the technician runs tcpdump and then attempts to navigate to a website using a web browser. The technician receives the following output:
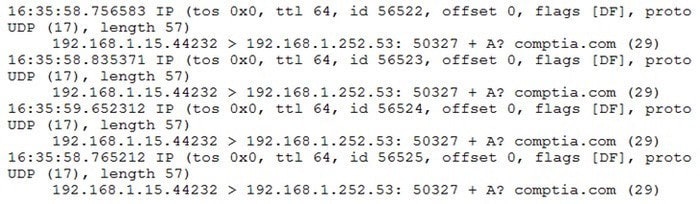
Afterward, the browser displays an error. Which of the following explains this issue?
A. A routing loop is within the network.
B. The host is configured with incorrect DNS settings.
C. A broadcast storm is occurring on the subnet.
D. The host is missing a route to the website.
-
Question 188:
A network engineer turned on logging to assist with troubleshooting a suspected configuration issue. Which of the following would provide the network engineer with the most informative log information?
A. FATAL
B. ERROR
C. DEBUG
D. WARN
-
Question 189:
Which of the following topologies requires me MOST connections when designing a network?
A. Mesh
B. Star
C. Bus
D. Ring
-
Question 190:
Which of the following fouling protocols is generally used by major ISPs for handing largescale internet traffic?
A. RIP
B. EIGRP
C. OSPF
D. BGP
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your N10-008 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.