Exam Details
Exam Code
:MD-101Exam Name
:Managing Modern DesktopsCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:421 Q&AsLast Updated
:Oct 30, 2023
Microsoft Microsoft Certifications MD-101 Questions & Answers
-
Question 31:
HOTSPOT
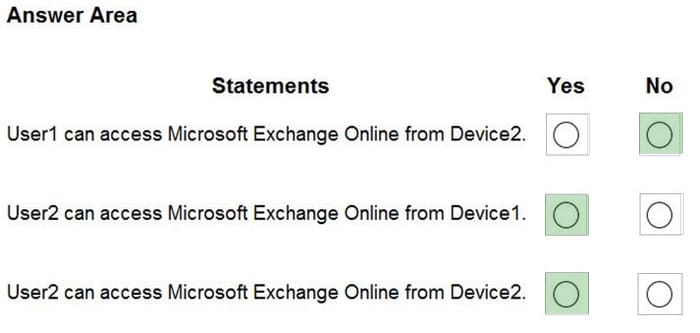
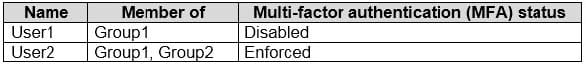
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
You have the devices shown in the following table.
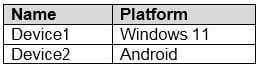
You have a Conditional Access policy named CAPolicy1 that has the following settings: Assignments
-Users or workload identities: Group1
-Cloud apps or actions: All cloud apps
Conditions
-Device platforms: include: Windows, Android
-Grant access controls: Require multi-factor authentication
You have a Conditional Access named CAPolicy2 that has the following settings:
Assignments
-Users or workload identities: Group2
-Cloud apps or actions: All cloud apps
Conditions
-Device platforms: Android
-Access controls: Block access
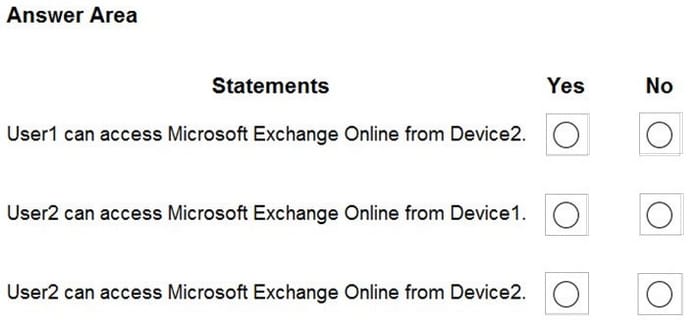
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 32:
HOTSPOT
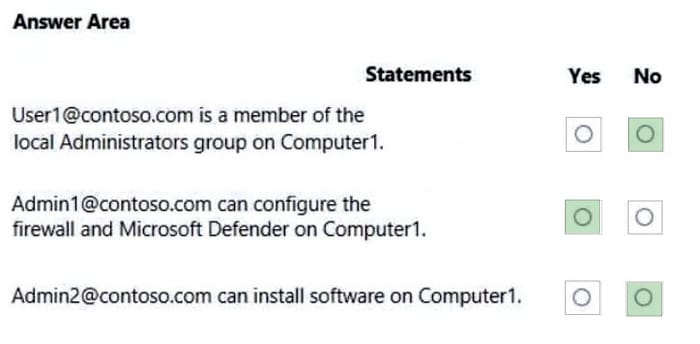
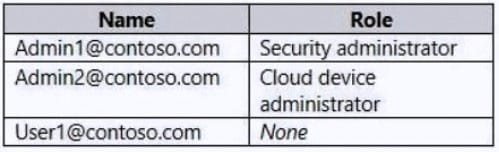
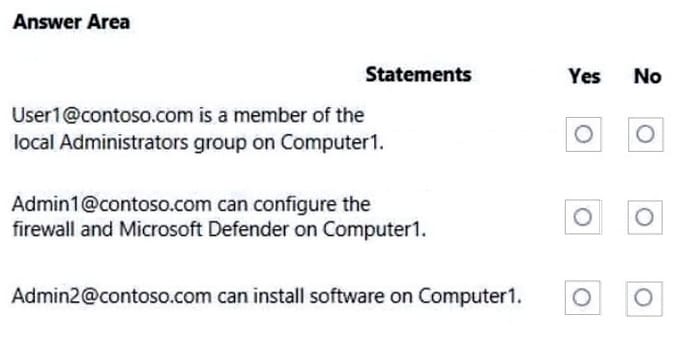
You have a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com that contains the users shown in the following table.
You have a computer named Computer1 that runs Windows 10. Computer1 is in a workgroup and has the local users shown in the following table.
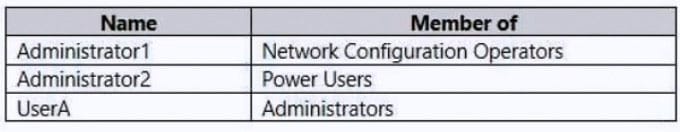
UserA joins Computer1 to Azure AD by using [email protected].
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 33:
HOTSPOT
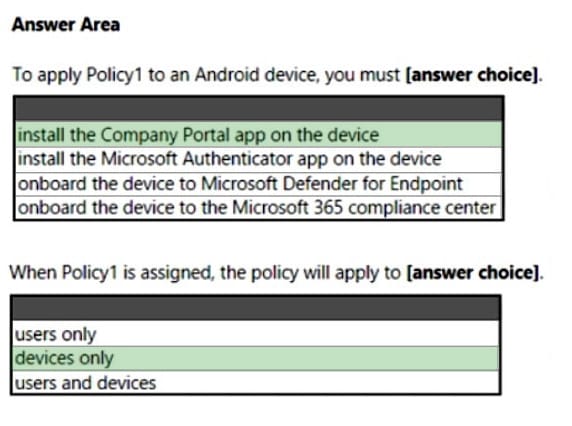
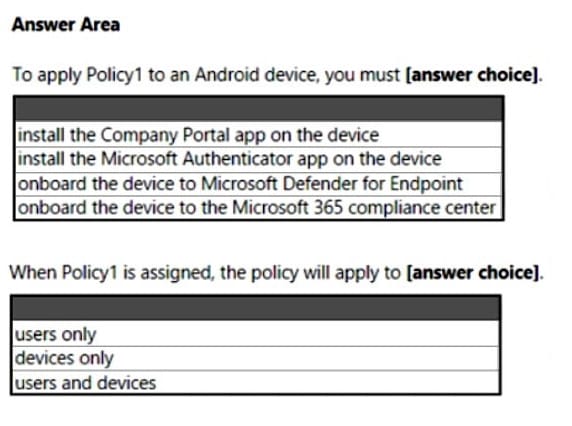
You have a Microsoft 365 E5 subscription.
You create an app protection policy for Android devices named Policy1 as shown in the following exhibit.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 34:
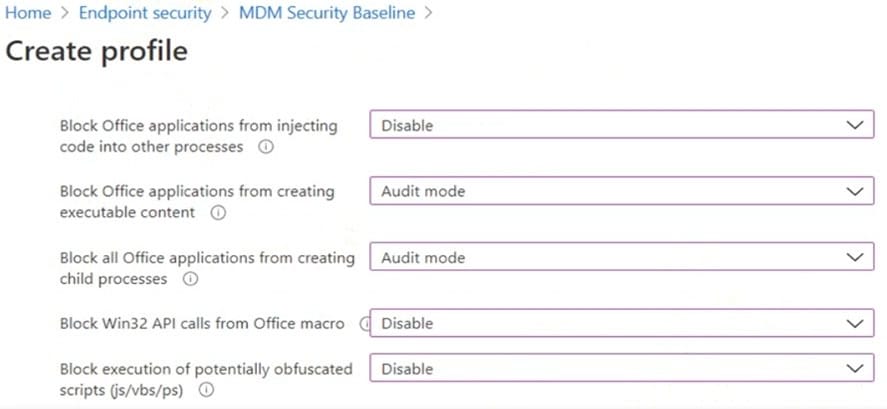
HOTSPOT
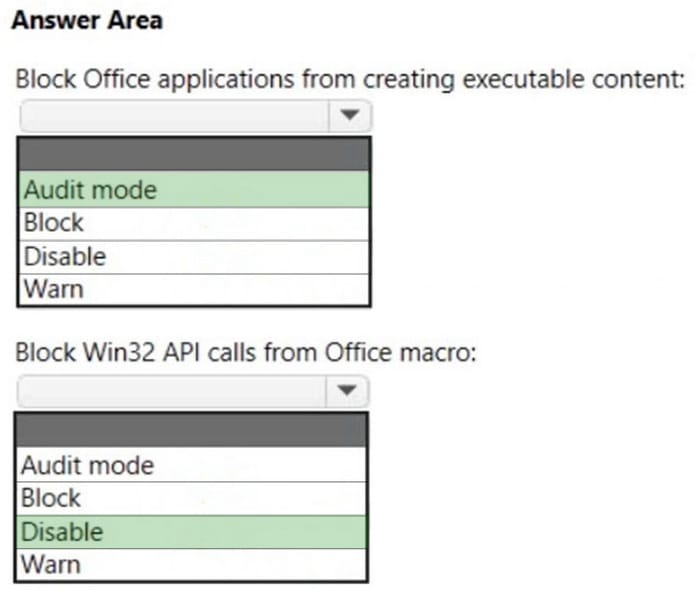
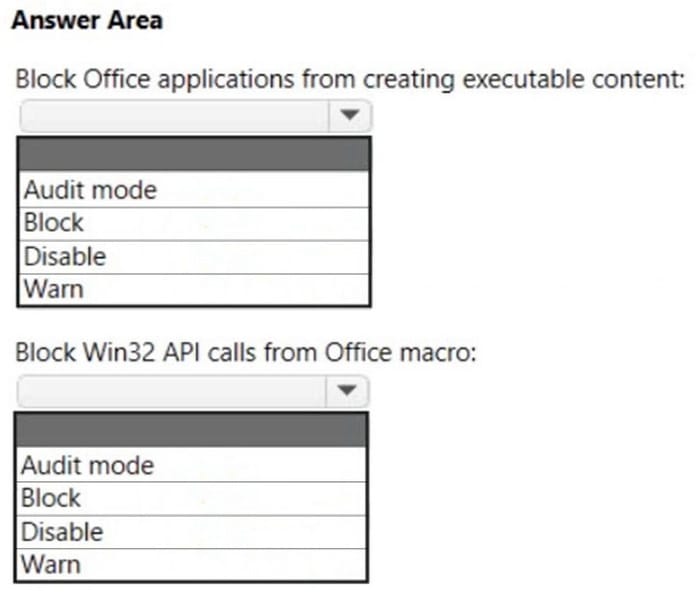
You have the MDM Security Baseline profile shown in the MDM exhibit. (Click the MDM tab.)
You have the ASR Endpoint Security profile shown in the ASR exhibit. (Click the ASR tab.)
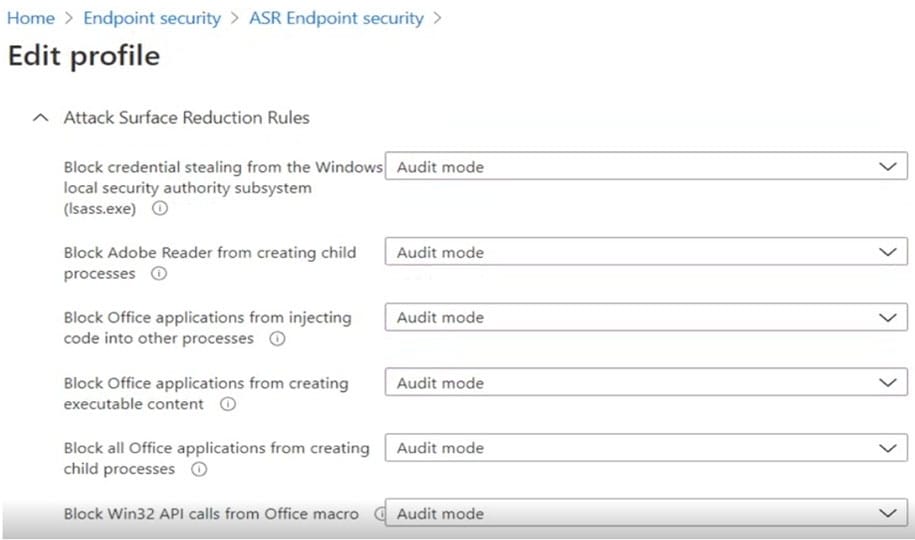
You plan to deploy both profiles to devices enrolled in Microsoft Intune.
You need to identify how the following settings will be configured on the devices:
1.
Block Office applications from creating executable content
2.
Block Win32 API calls from Office macro
Currently, the settings are disabled locally on each device.
What are the effective settings on the devices? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 35:
HOTSPOT
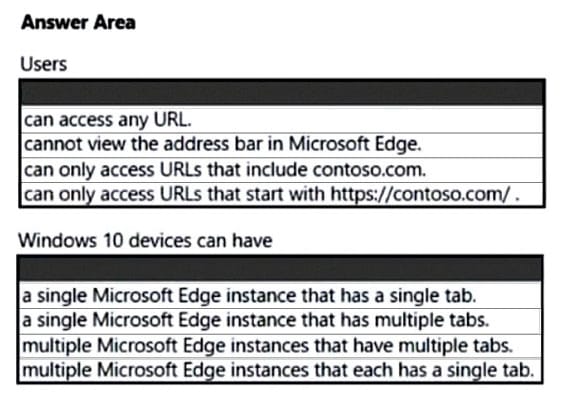
You have the device configuration profile shown in the following exhibit.
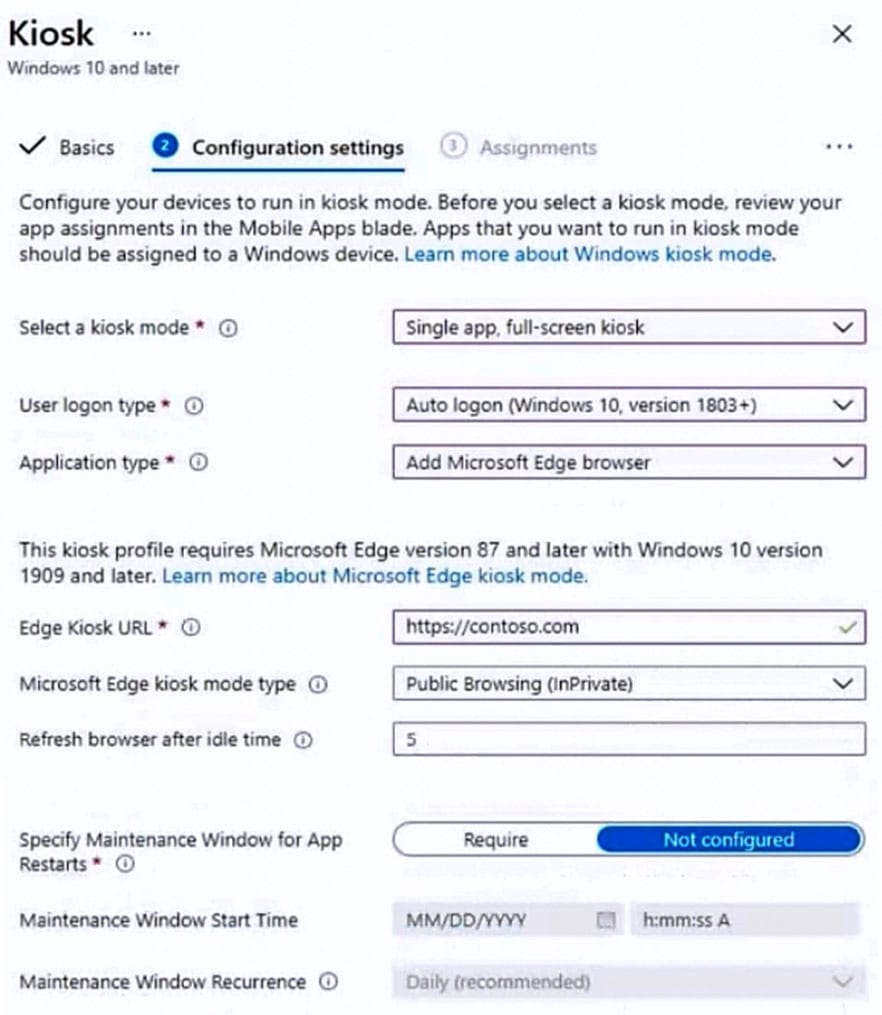
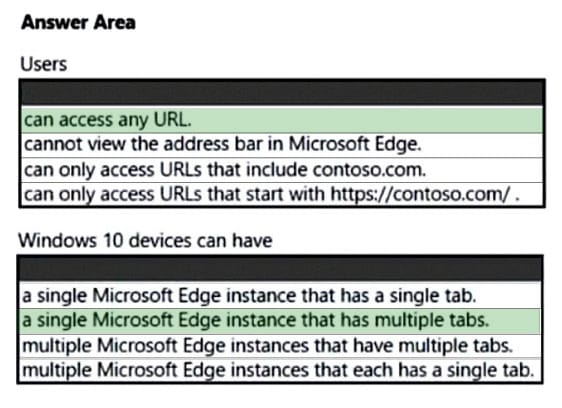
Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 36:
HOTSPOT
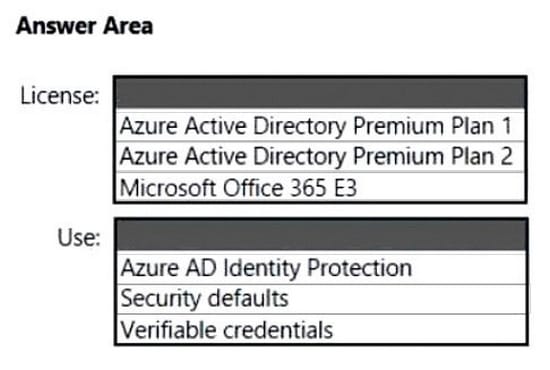
You have an Azure Active Directory (Azure AD) tenant named contoso.com.
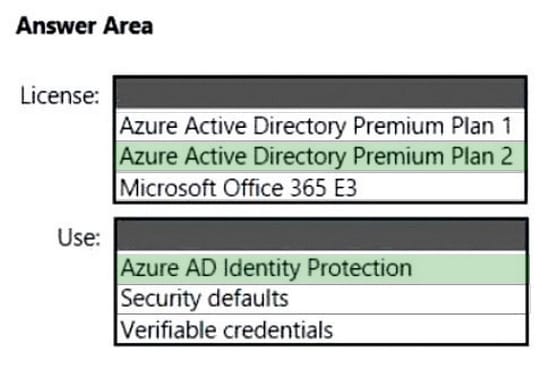
You plan to create a Conditional Access policy to block users that have a high sign-in risk level.
You need to identify the required license, and what to use to identify the sign-in risk level.
The solution must minimize costs.
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
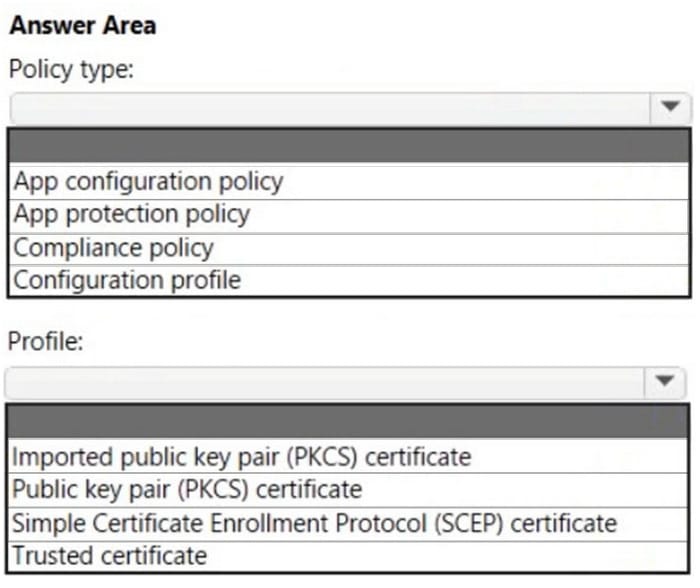
Question 37:
HOTSPOT
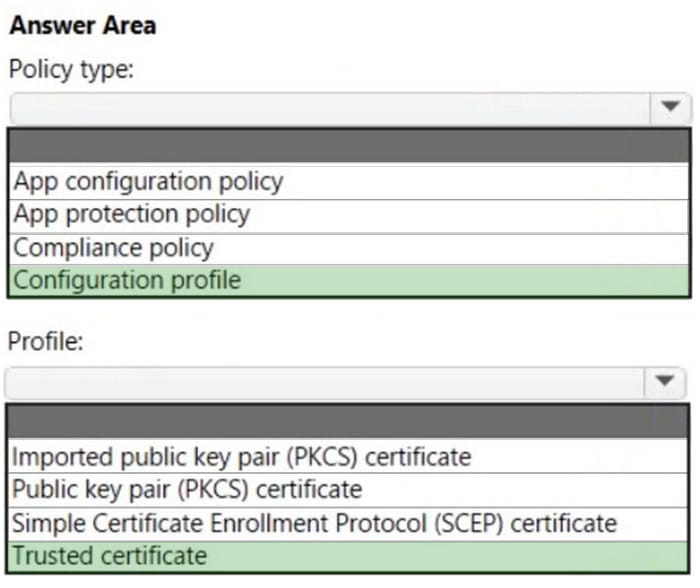
You have a Microsoft 365 tenant and an internal certification authority (CA).
You need to use Microsoft Intune to deploy the root CA certificate to managed devices.
Which type of Intune policy and profile should you use? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 38:
HOTSPOT
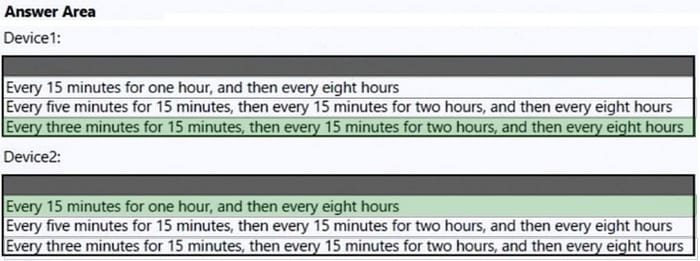
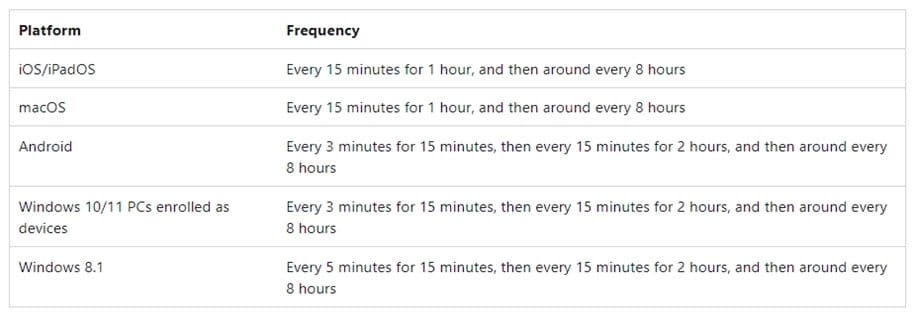
You have a Microsoft 365 subscription that contains the devices shown in the following table.
You plan to enroll the devices in Microsoft Intune.
How often will the compliance policy check-ins run after each device is enrolled in Intune?
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
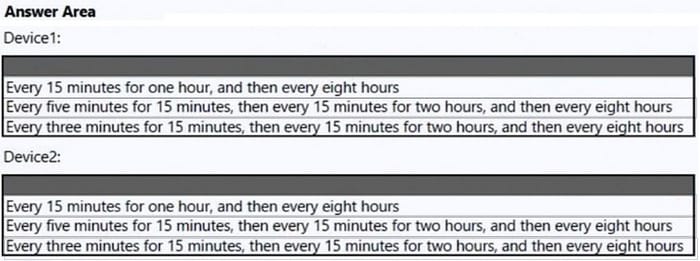
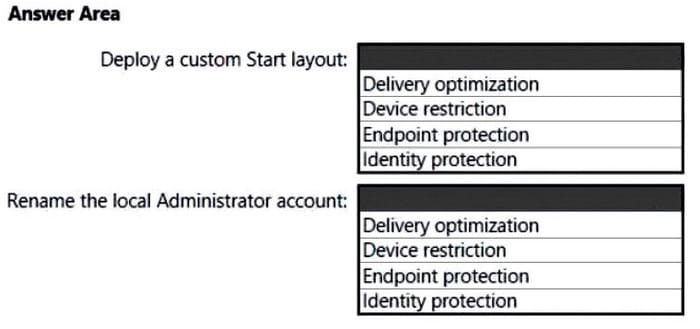
Question 39:
HOTSPOT
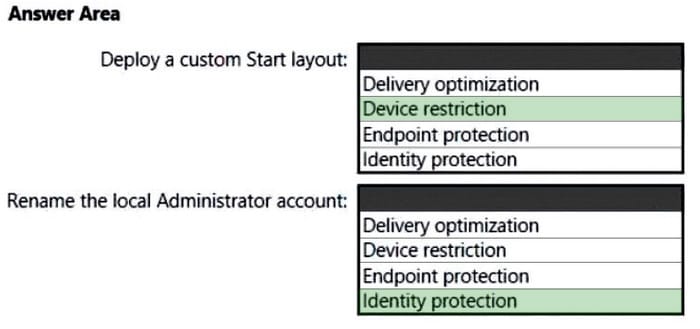
You have a Microsoft 365 subscription that uses Microsoft Intune and contains 100 Windows 10 devices.
You need to create Intune configuration profiles to perform the following actions on the devices:
1.
Deploy a custom Start layout.
2.
Rename the local Administrator account.
Which profile template should you use for each action? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
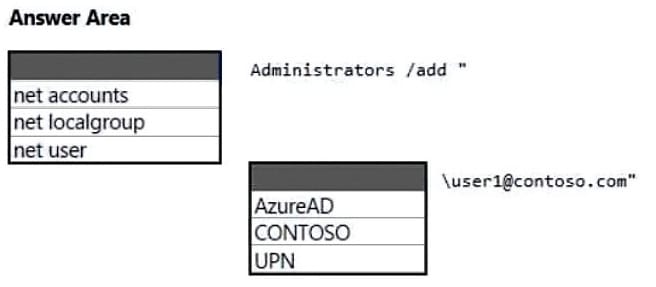
Question 40:
HOTSPOT
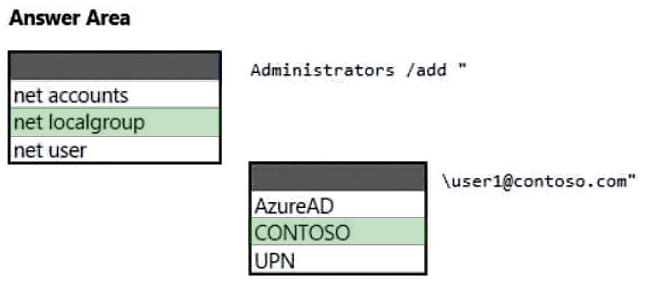
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains a user named User1. User1 has a user principal name (UPN) of user1 @contoso.com.
You join a Windows 10 device named Client1 to contoso.com.
You need to add User1 to the local Administrators group of Client1.
How should you complete the command? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MD-101 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.