Exam Details
Exam Code
:MD-101Exam Name
:Managing Modern DesktopsCertification
:Microsoft CertificationsVendor
:MicrosoftTotal Questions
:421 Q&AsLast Updated
:Oct 30, 2023
Microsoft Microsoft Certifications MD-101 Questions & Answers
-
Question 21:
HOTSPOT
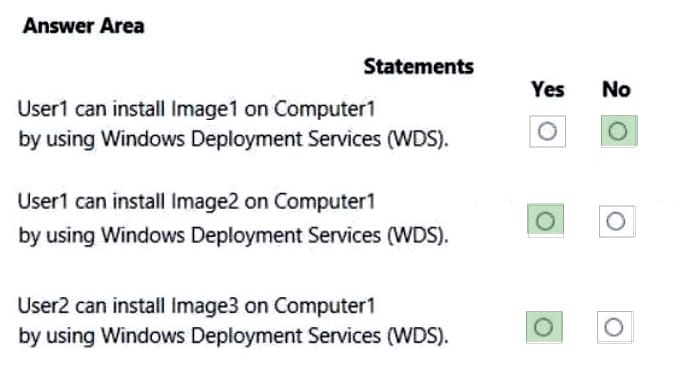
Your network contains an Active Directory domain. The domain contains the users shown in the following table.
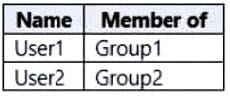
You have a server named Server that runs Windows Server 2019 and has the Windows Deployment Services role installed. Server1 contains an x86 boot image and three Windows 10 install images. The install images are shown in the following table.
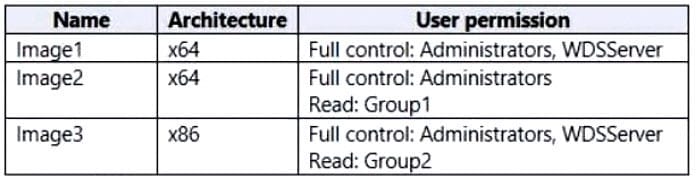
You purchase a computer named Computer1 that is compatible with the 64-bit version of Windows 10.
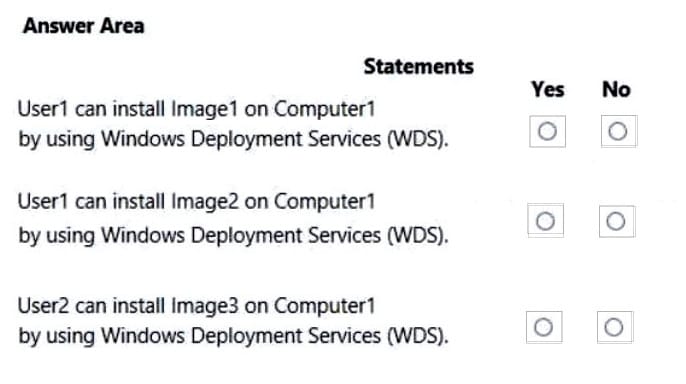
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 22:
HOTSPOT
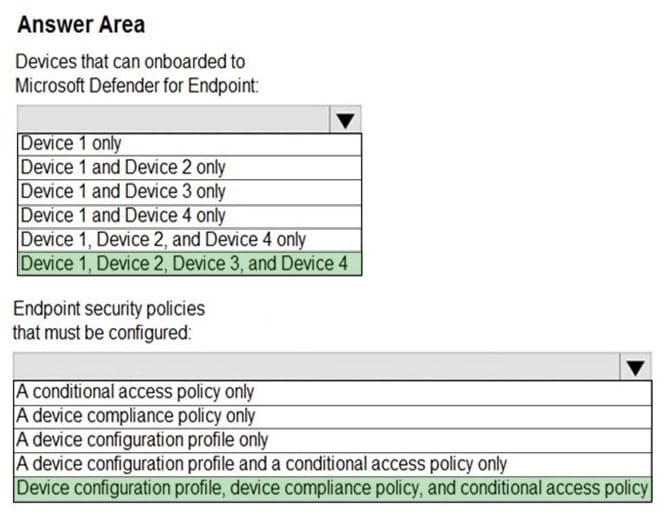
You have a Microsoft 365 E5 tenant that connects to Microsoft Defender for Endpoint.
You have devices enrolled in Microsoft Intune as shown in the following table.
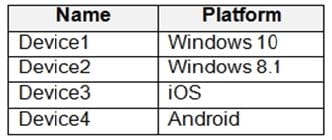
You plan to use risk levels in Microsoft Defender for Endpoint to identify whether a device is compliant. Noncompliant devices must be blocked from accessing corporate resources.
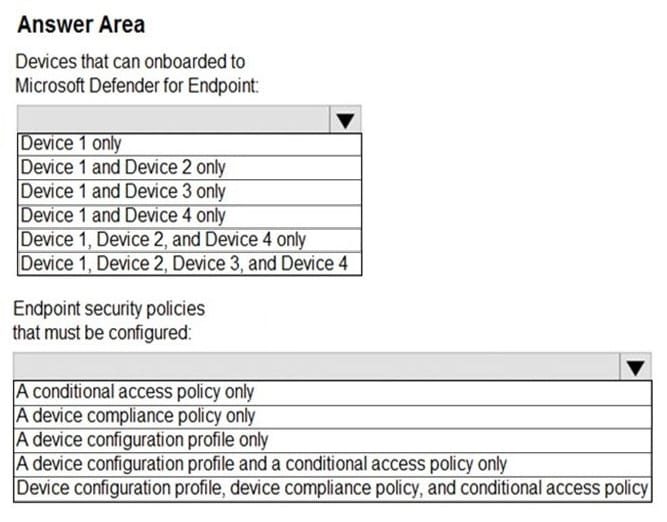
You need to identify which devices can be onboarded to Microsoft Defender for Endpoint, and which Endpoint security policies must be configured.
What should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 23:
HOTSPOT
You have a Microsoft Intune subscription that has the following device compliance policy settings:
1.
Mark devices with no compliance policy assigned as: Compliant
2.
Compliance status validity period (days): 14
On January 1, you enroll Windows 10 devices in Intune as shown in the following table.
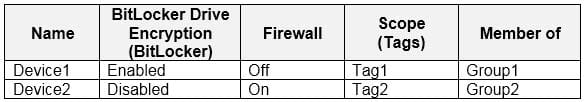
On January 4, you create the following two device compliance policies:
1.
Name: Policy1
2.
Platform: Windows 10 and later
3.
Require BitLocker: Require
4.
Mark device noncompliant: 5 days after noncompliance
5.
Scope (Tags): Tag1
6.
Name: Policy2
7.
Platform: Windows 10 and later
8.
Firewall: Require
9.
Mark device noncompliant: Immediately 10.Scope (Tags): Tag2 On January 5, you assign Policy1 and Policy2 to Group1.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
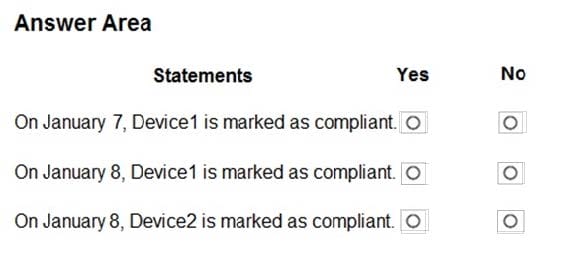
-
Question 24:
HOTSPOT
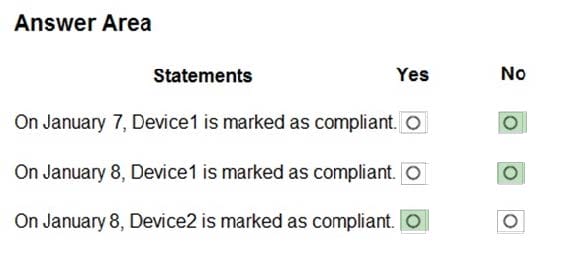
You have two Windows 10 devices enrolled in Microsoft Intune as shown in the following table.

The Compliance policy settings are configured as shown in the following exhibit.
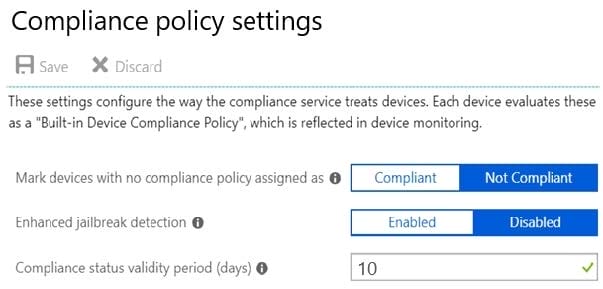
On August 1, you create a compliance policy as shown in the following exhibit.
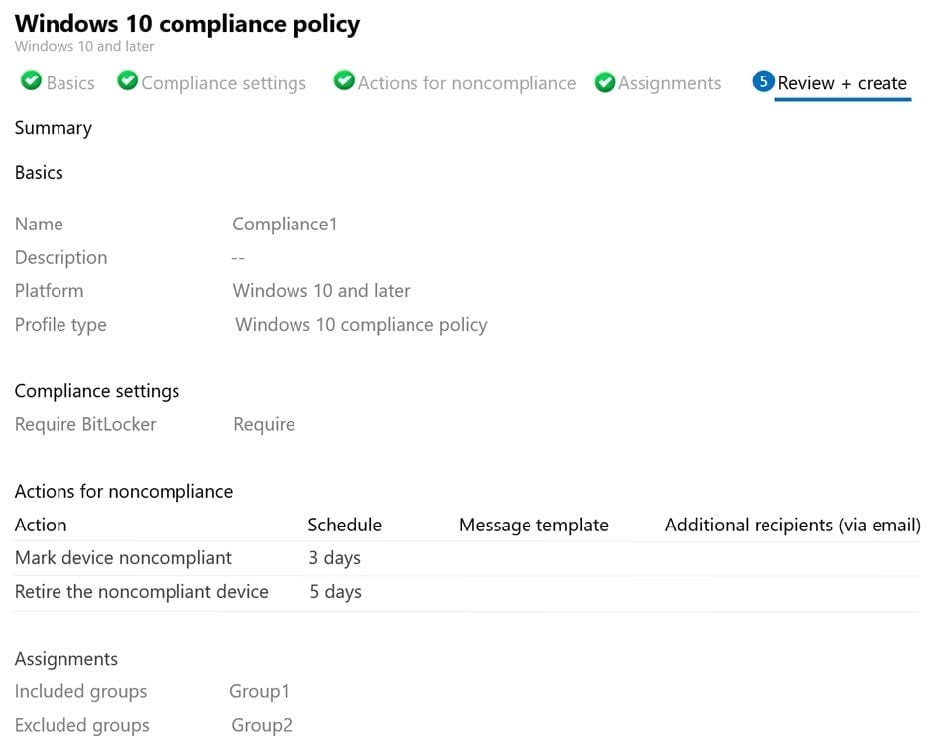
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:

-
Question 25:
HOTSPOT
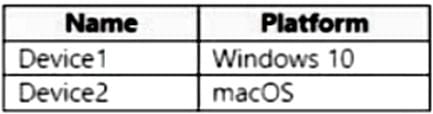
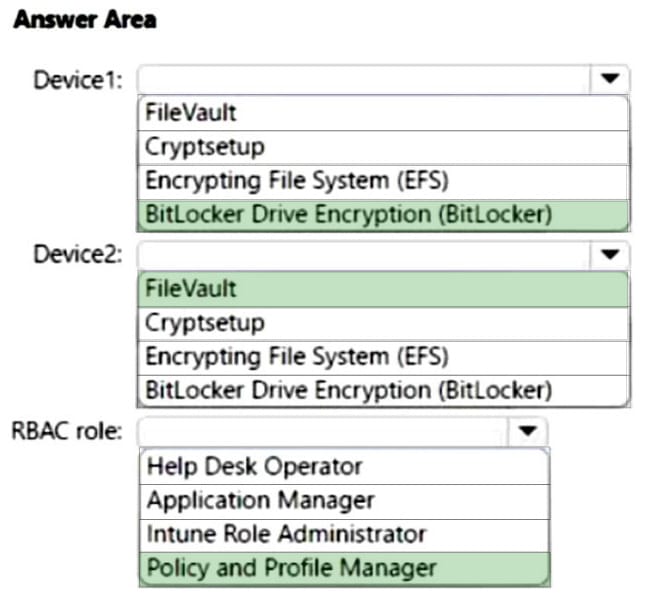
You have a Microsoft 365 tenant that uses Microsoft Intune and contains the devices shown in the following table.
In Endpoint security, you need to configure a disk encryption policy for each device.
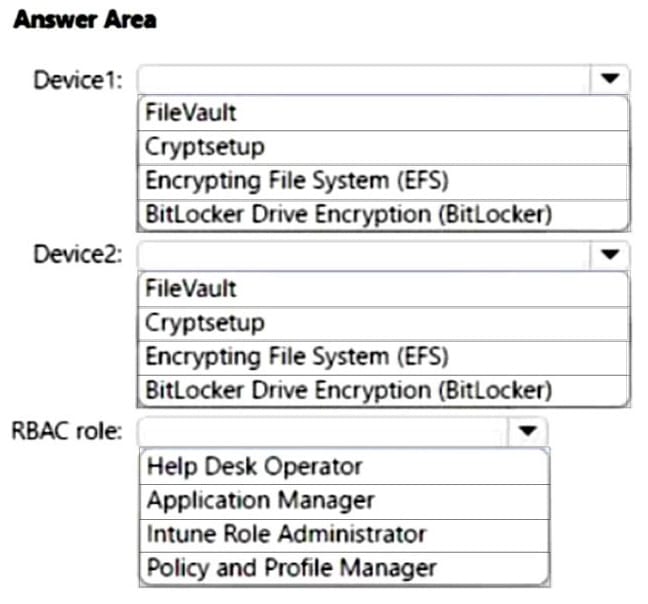
Which encryption type should you use for each device, and which role-based access control (RBAC) role in Intune should you use to manage the encryption keys?
To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 26:
HOTSPOT
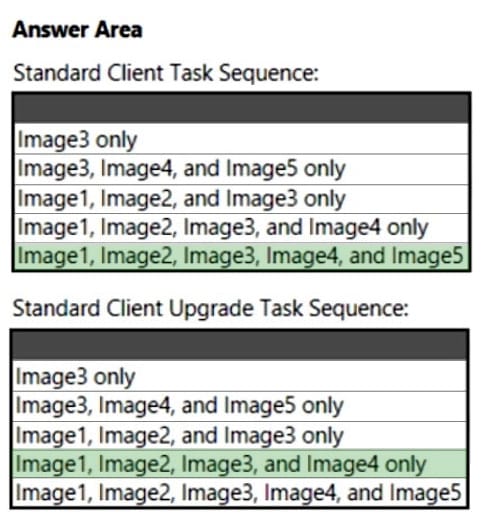
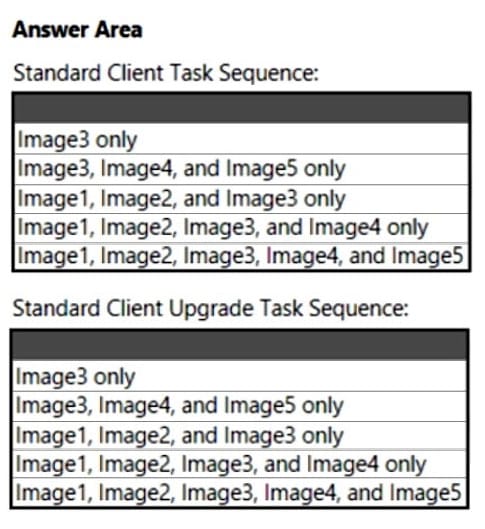
You have a Microsoft Deployment Toolkit (MDT) deployment share named Share1.
You add Windows 10 images to Share1 as shown in the following table.
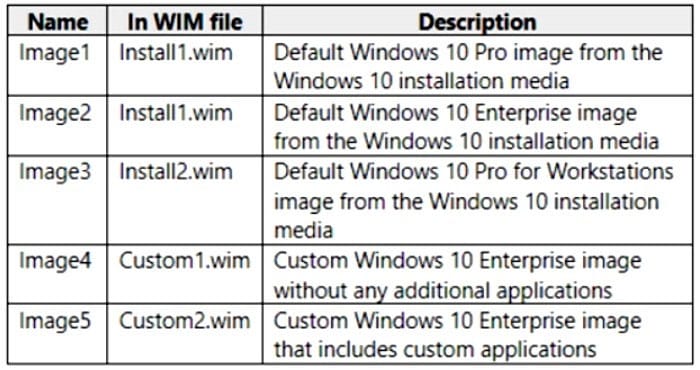
Which images can be used in the Standard Client Task Sequence, and which images can be used in the Standard Client Upgrade Task Sequence? NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 27:
HOTSPOT
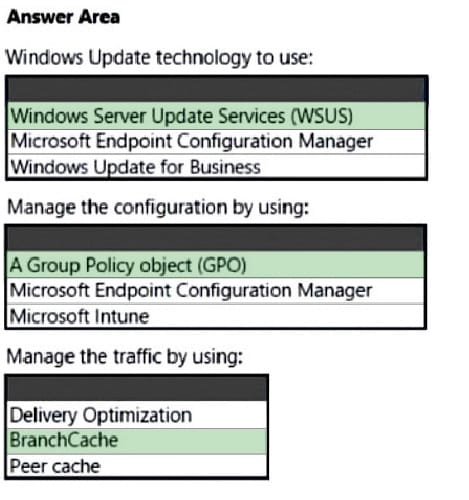
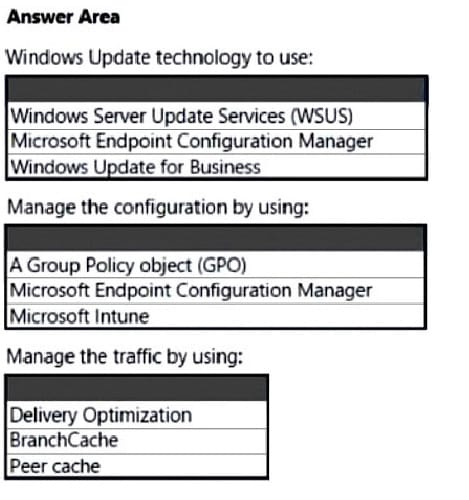
You have 100 computers that run Windows 10. You have no servers. All the computers are joined to Microsoft Azure Active Directory (Azure AD).
The computers have different update settings, and some computers are configured for manual updates.
You need to configure Windows Update. The solution must meet the following requirements:
1.
The configuration must be managed from a central location.
2.
Internet traffic must be minimized.
3.
Costs must be minimized.
How should you configure Windows Update? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 28:
HOTSPOT
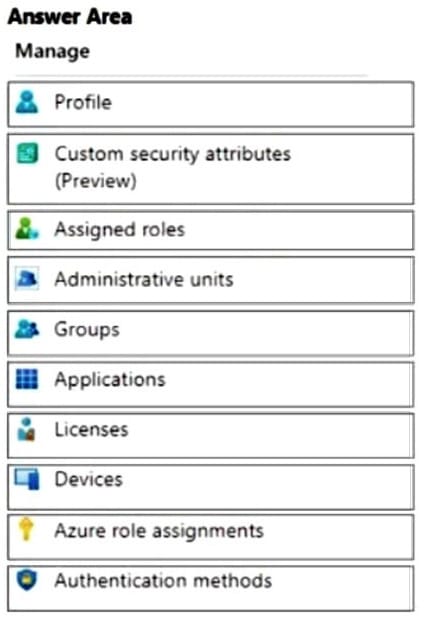
You have a Microsoft 365 E5 subscription that contains a user named User1. You need to perform the following tasks for User1:
1.
Set the Usage location to Canada.
2.
Configure the Phone and Email authentication contact info for self-service password reset (SSPR).
Which two settings should you configure in the Azure Active Directory admin center? To answer, select the appropriate settings in the answer area.
NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 29:
HOTSPOT
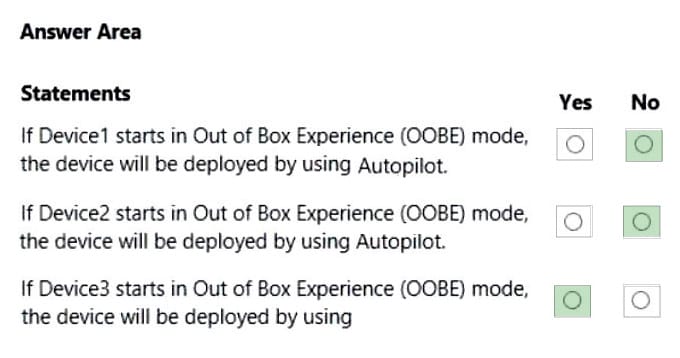
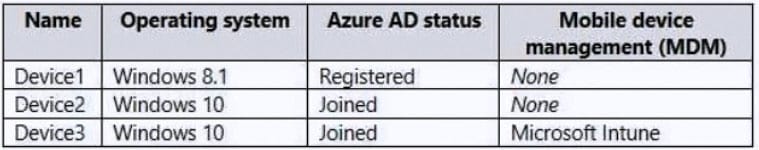
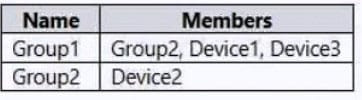
You have an Azure Active Directory (Azure AD) tenant named contoso.com that contains the devices shown in the following table.
Contoso.com contains the Azure Active Directory groups shown in the following table.
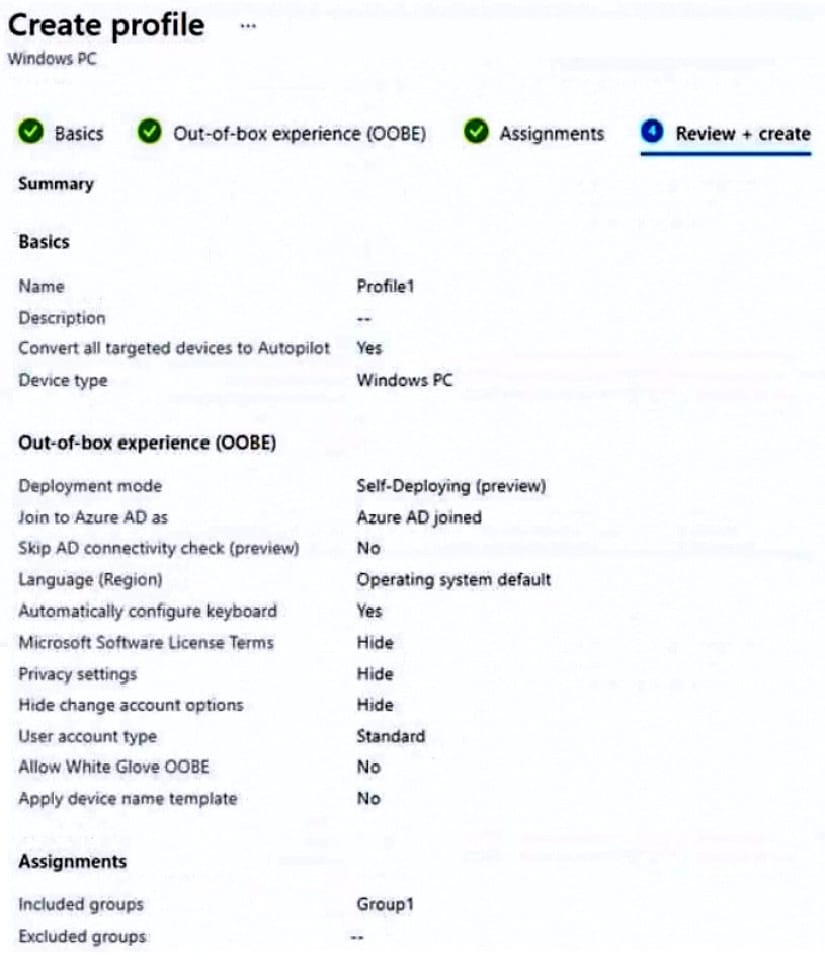
You add a Windows Autopilot deployment profile. The profile is configured as shown in the following exhibit.
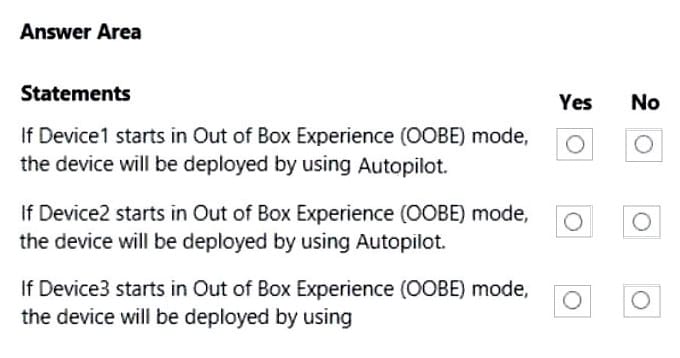
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
-
Question 30:
HOTSPOT
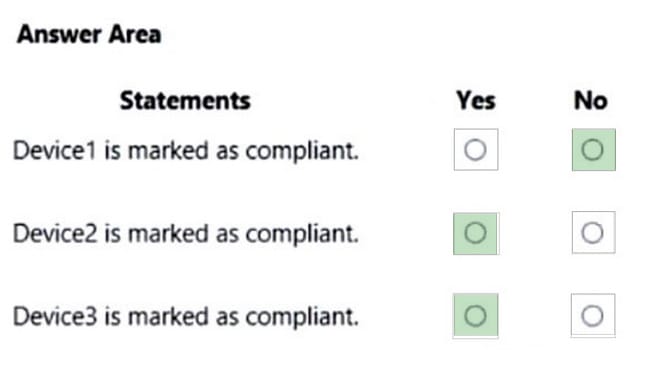
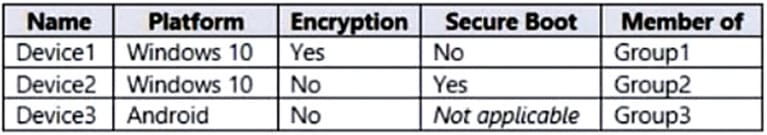
You have devices enrolled in Microsoft Intune as shown in the following table.
Intune includes the device compliance policies shown in the following table.
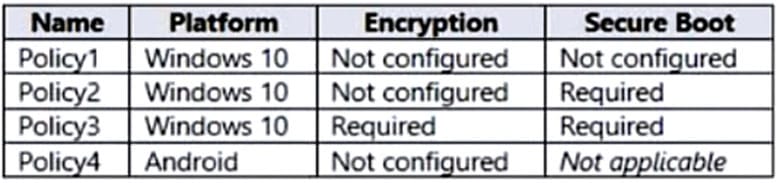
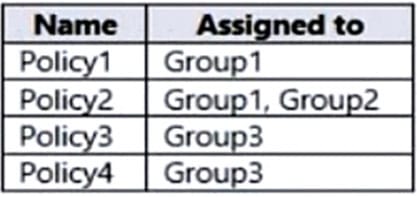
The device compliance policies have the assignments shown in the following table.
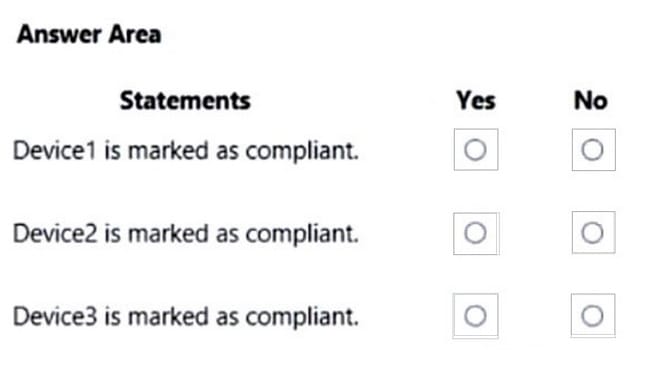
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
Hot Area:
Related Exams:
62-193
Technology Literacy for Educators70-243
Administering and Deploying System Center 2012 Configuration Manager70-355
Universal Windows Platform – App Data, Services, and Coding Patterns77-420
Excel 201377-427
Excel 2013 Expert Part One77-725
Word 2016 Core Document Creation, Collaboration and Communication77-726
Word 2016 Expert Creating Documents for Effective Communication77-727
Excel 2016 Core Data Analysis, Manipulation, and Presentation77-728
Excel 2016 Expert: Interpreting Data for Insights77-731
Outlook 2016 Core Communication, Collaboration and Email Skills
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Microsoft exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your MD-101 exam preparations and Microsoft certification application, do not hesitate to visit our Vcedump.com to find your solutions here.