Exam Details
Exam Code
:JPR-934Exam Name
:Security, Expert (JNCIE-SEC)Certification
:Juniper CertificationsVendor
:JuniperTotal Questions
:61 Q&AsLast Updated
:Aug 20, 2025
Juniper Juniper Certifications JPR-934 Questions & Answers
-
Question 21:
You work as a Network Administrator for ABC.com. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server. An application named Accounts is installed on
the network. The Accounts application uses a shared folder named AccFolder to keep all its data. The AccFolder folder is placed on a file server named uCFileServer. All users in the network use the application to update the accounts
information of various clients of the company. The application opens various data files to work upon.
You are required to accomplish the following tasks:
All files in the AccFolder folder should be backed up automatically twice daily.
The backup process should take a backup of all the open files in the folder.
In order to accomplish the tasks, you take the following steps:
Configure the Backup and Restore Wizard to take a backup of AccFolder.
Unselect the Disable volume shadow copy check box in the Backup and Restore Wizard.
Set the schedule of the Backup and Restore Wizard to take a backup every 12 hours through the Advanced Schedule Options.
What will happen after taking the required steps?
A. The backup process will take a backup of all the open files in the folder.
B. Both tasks will be accomplished.
C. All the files in the AccFolder folder will be backed up automatically twice daily.
D. None of the tasks will be accomplished.
-
Question 22:
You work as a Network Administrator for ABC.com. The company has a Windows Active Directory-based single domain single forest network. The functional level of the forest is Windows Server. An intranet-based Web site is required to be
installed on the network. Two servers are available for installing the application. You are required to accomplish the following tasks:
The Web site should be available all the time for the clients.
Both servers should be capable of fulfilling the clients' requests at a time.
You take the following steps:
Create a two-node server cluster.
Configure one server as an active server and the other as a passive server.
Which of the required tasks will be accomplished by taking these steps?
A. Both servers will be capable of fulfilling the clients' requests at a time.
B. None of the tasks will be accomplished.
C. The Web site will be available all the time for the clients.
D. Both tasks will be accomplished.
-
Question 23:
You administer your company's network. The network consists of a single Active Directory domain. All servers run Windows Server. The network contains a two-node server cluster. The company's security expert informs you that the
password on the domain user account that is used for the Cluster service has been compromised and must be changed immediately. Your actions should cause minimal or no disruption of the services provided by the cluster because the
cluster is running a mission-critical application.
Which of the following should you do?
A. Use Active Directory Users and Computers to reset the password.
B. Use the Services console to change the password on any one of the cluster nodes.
C. Use the Cluster command with the appropriate options.
D. Use the dsmod user command with the appropriate options.
E. Use the dsmod computer command with the appropriate options.
-
Question 24:
You are the network administrator for your company's network. The network consists of two Active Directory domains: lmiweb.com and hr.lmiweb.com. The lmiweb.com domain supports most of the company's user accounts and resources.
The hr.lmiweb.com domain contains the user accounts and resources for the company's human resources department.
The company has deployed an extensive 802.11b wireless network. Access points (APs) have been deployed throughout the company to provide users in all departments with wireless connectivity and serve as bridges to the wired LAN. A
total of 325 users, including all members of hr.lmiweb.com, have been issued laptops with 802.11bcompliant network adapters. No other computers have wireless connectivity. All wireless LANs have Wired Equivalent Privacy (WEP) enabled
to secure these communications.
Human resources users work throughout the company providing employee training and informational seminars. These users require access to the wireless LAN in all company locations. You must ensure that all human resources data is as
secure as possible as it is transmitted across the wireless LAN. Only users with accounts in only specific users/computers groups should be able to access the human resources division's wireless LAN. In addition, users without accounts in
this domain should not be able to view or select the LAN from their list of available networks.
What should you do? Each correct answer presents part of the solution. (Choose three.)
A. Configure MAC filtering on each department's wireless LAN.
B. Configure MAC filtering on the human resources wireless LAN.
C. Enable Service Set Identifier (SSID) broadcasting on each department's access point.
D. Configure a unique Service Set Identifier (SSID) for each department's wireless LAN.
E. Configure a unique Service Set Identifier (SSID) for the human resources wireless LAN.
F. Enable Service Set Identifier (SSID) broadcasting on all the human resources access points.
G. Disable Service Set Identifier (SSID) broadcasting on all the human resources access points.
-
Question 25:
You are the network administrator for your company. The network consists of a single Active Directory domain with five domain controllers that run Windows Server, Enterprise Edition. You are updating the public key infrastructure (PKI) for your company. Issuing Certification Authorities (CAs) have been provided certificates with a validity period of five years. Certificates are issued to enable network users to encrypt files on their computers. Basic EFS certificates have been issued and have been configured with the default validity period. You want to configure all new EFS certificates so that they are valid for up to three years.
What should you do? Each correct answer presents part of the solution. (Choose all that apply.)
A. Duplicate and rename the Basic EFS certificate template.
B. Open the Basic EFS certificate template Properties dialog box.
C. Select the General tab and edit the validity period.
D. Select the General tab and edit the renewal period.
E. Select the Security tab and change the permission for the Administrators group to Enroll.
-
Question 26:
You administer your company's Web site, which contains executable programs. You want to provide the highest level of trust to Internet users who download your programs, and you want to ensure that users' browsers will allow them to
download the programs. Your company's network includes an enterprise root Certification Authority (CA) and an issuing enterprise subordinate CA.
Which of the following actions should you take?
A. Request a Code Signing certificate from your company's enterprise subordinate CA.
B. Request a Code Signing certificate from a commercial CA.
C. Request a User Signature Only certificate from your company's enterprise subordinate CA.
D. Request a User Signature Only certificate from a commercial CA.
-
Question 27:
You are one of the administrators for your company's Windows Server network. The relevant portion of the network is presented in the following exhibit.
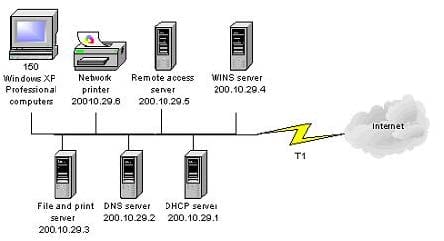
All servers, client computers and one network print device are currently configured with static IP addresses. The network IP address is 200.10.29.0. A DHCP server has been deployed but has not yet been configured. You must configure a
new scope that will provide the existing client computers with IP configurations. The new scope should support an additional 25 new client computers that will be deployed within the next two months.
Which settings should be included in the new DHCP scope? Each correct answer presents part of the solution. (Choose three.)
A. subnet mask: 255.255.255.0
B. subnet mask: 255.255.255.128
C. DHCP scope starting IP address: 200.10.29.7 DHCP scope ending IP address: 200.10.29.254
D. DHCP scope starting IP address: 200.10.29.1 DHCP scope ending IP address: 200.10.29.254
E. DHCP scope exclusion range starting IP address: 200.10.29.1 DHCP scope exclusion range ending IP address: 200.10.29.6
F. DHCP scope exclusion range starting IP address: 200.10.29.1 DHCP scope exclusion range ending IP address: 200.10.29.254
-
Question 28:
You administer your company's network. The network consists of a single Active Directory domain. All servers run Windows Server. The network contains a two-node server cluster. The company's security expert informs you that the password on the domain user account that is used for the Cluster service has been compromised and must be changed immediately. Your actions should cause minimal or no disruption of the services provided by the cluster because the cluster is running a mission-critical application.
Which of the following should you do?
A. Use Active Directory Users and Computers to reset the password.
B. Use the Services console to change the password on any one of the cluster nodes.
C. Use the Cluster command with the appropriate options.
D. Use the dsmod user command with the appropriate options.
E. Use the dsmod computer command with the appropriate options.
-
Question 29:
You administer your company's Windows network. The network consists of 25 Windows Server computers. The network contains an offline root Certification Authority (CA) located in the main office and a subordinate issuing CA in the main
office and each of the remaining four retail locations.
One of the four retail locations has been purchased and will operate as a franchise. You must ensure that resources on the company network will not accept certificates from the associated subordinate CA in this retail location after the sale is
completed. Your solution must use a minimum amount of administrative effort.
What should you do? (Choose three. Each correct answer presents part of the solution.)
A. On the company's root CA, revoke the certificate of the subordinate CA.
B. Disconnect the subordinate CA from the network.
C. On the subordinate CA, remove the CA software and remove the CA files.
D. On the subordinate CA, revoke the certificates that it has issued.
E. Publish a new Certificate Revocation List.
F. Copy the Edb.log file from the root CA to its Certification Distribution Point on your network.
G. Copy the Edb.log file from the subordinate CA to its Certification Distribution Point on your network.
H. Copy the Certificate Revocation List file to the Certificate Distribution Point on your network.
-
Question 30:
You are the backup administrator for your company. You are responsible for ensuring that all data on ten files servers are protected against data loss. Normal business hours from 8 A.M. to 5 P.M., Monday through Friday, are observed.
Network access is prohibited outside normal business hours.
A member server named File1 contains shared folder accessed by users in the sales department. The disk structure of File1 is shown in the following exhibit:
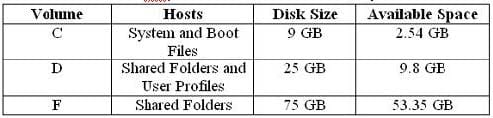
You have scheduled a daily backup of File1 as shown in the exhibit. (Click the Exhibit(s) button.) Users in the Sales department frequently leave documents open on their desktops when they leave work. These users occasionally request that
you restore a previous version of a file from backup. However, some of these files are not included in recent backup sets. You must modify the backup procedures for File1 so that all files, including open documents, will be included in the daily
backup. You also want to provide users with the ability to restore their files.
What should you do? (Choose all that apply. Each correct answer presents part of the solution.)
A. Move all shared user data folders from drive D to drive F.
B. Move all shared folders user data from drive F to drive D.
C. Enable Shadow Copies of Shared Folders on drive F.
D. Enable Volume shadow copy for the scheduled backup job.
E. Select the Disable volume shadow copy option for the scheduled backup job.
F. Install the Previous Versions Client software on all Sales department computers.
G. Create a new daily backup job by using the same settings, but clear the Disable volume shadow copy option.
Related Exams:
JN0-102
Internet Associate, Junos(JNCIA-Junos)JN0-104
Junos, Associate (JNCIA-Junos)JN0-105
Junos, Associate (JNCIA-Junos)JN0-1101
Juniper Networks Certified Design Associate (JNCDA)JN0-1103
Design, Associate (JNCIA-Design)JN0-130
Juniper networks Certified internet specialist.e(jncis-e)JN0-1301
Data Center Design, Specialist (JNCDS-DC)JN0-1302
Data Center Design Specialist (JNCDS-DC)JN0-1331
Security Design, Specialist (JNCDS-SEC)JN0-1332
Security Design, Specialist (JNCDS-SEC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Juniper exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your JPR-934 exam preparations and Juniper certification application, do not hesitate to visit our Vcedump.com to find your solutions here.